PHISHING INDEX
Below are the most common email phishing attempts detected by TG Soft's Anti-Malware Research Center in
June 2023:
30/01/2023 =>
Mediolanum
24/01/2023 =>
Intesa Sanpaolo
20/01/2023 =>
Mooney
19 and 20/01/2023 =>
Aruba
18/01/2023 =>
Account Posta Elettronica (Email Account)
18/01/2023 =>
Amazon Smishing
16/01/2023 =>
Aruba
15/01/2023 =>
BRT
14/01/2023 =>
TV Samsung
14/01/2023 =>
Carrefour
14/01/2023 =>
Aruba
13/01/2023 =>
Account Posta Elettronica (Email Account)
12/01/2023 =>
MediaWorld
11/01/2023 =>
BRT
09/01/2023 =>
SexTortion
07/01/2023 =>
Carrefour
03/01/2023 =>
Subito
02/01/2023 =>
Carrefour
02/01/2023 =>
BRT
01/01/2023 =>
Q8 Buoni carburante (Fuel vouchers)
These emails are intended to trick some unfortunate person into providing sensitive data - such as bank account information, credit card codes or personal login credentials - with all the possible easily imaginable consequences .
January 30, 2023 ==> Phishing Mediolanum
«SUBJECT:<
Fwd:.>
This new phishing attempt comes from a fake e-mail from
Mediolanum.
The message notifies the unsuspecting recipient, that Banca Mediolanum's new security service has been activated, replacing the code received via SMS, that will disappear in early 2023. It then invites him to activate the new security system, to access the account online, through the following link:
ACCEDI => (LOGIN)
The alert message comes from an email address <bafataz(at)ns(dot)sympatico(dot)ca> unrelated to the Mediolanum's domain and contains a very generic text, although the cybercriminal had the graphic foresight to include the well-known Mediolanum logo, that could mislead the user.
The purpose is to get the recipient to click on the link ACCEDI => (LOGIN) which, we would like to point out, links to a page that has nothing to do with the Mediolanum site, but has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
January 24, 2023 ==> Phishing Intesa Sanpaolo
«SUBJECT: <
Sicurezza del cliente - Attiva il nuovo sistema di sicurezza>
(Client security - Activate the new security system)
This new phishing attempt comes from a fake e-mail simulating a message from
Intesa Sanpaolo.
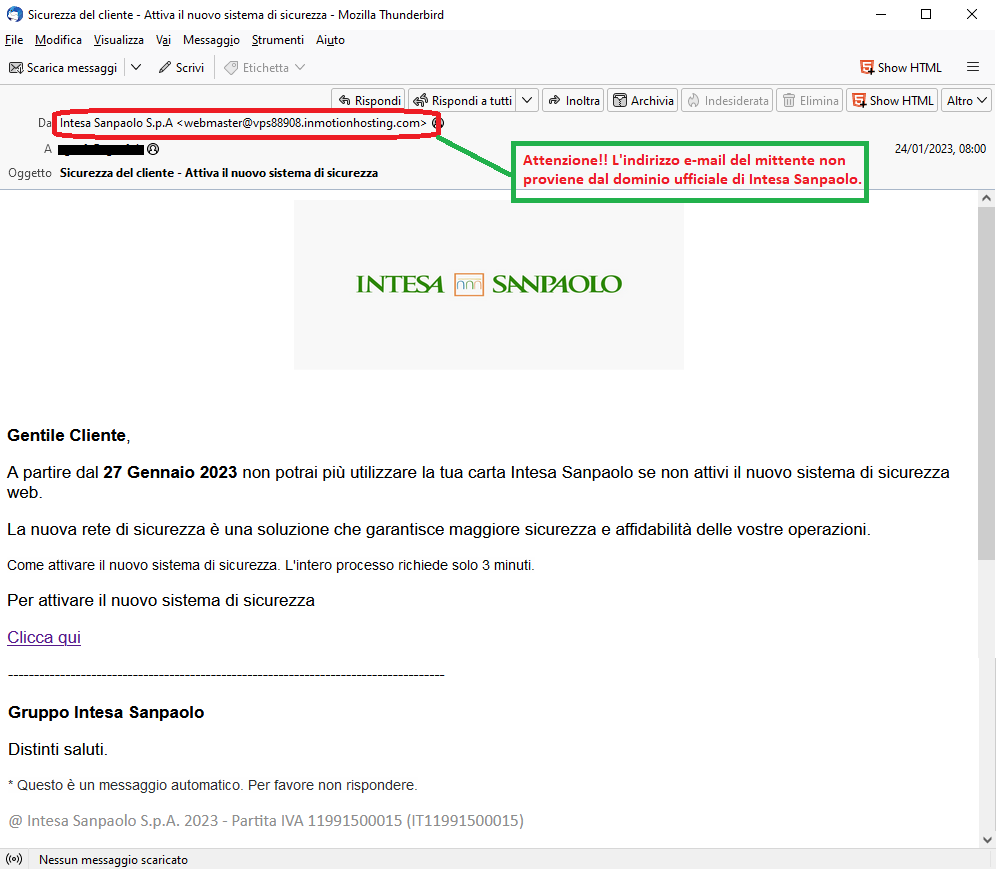
The message notifies the unsuspecting recipient tha,t as of January 27, 2023, he will no longer be able to use his Intesa Sanpaolo card, unless he activates the new web security system, which provides greater security and reliability to transactions. It then invites him to activate the new security system.The operation is simple and takes only 3 minutes, through the following link:
Clicca qui (Click here)
We can see right away that the alert message comes from an email address <webmaster(at)vps88908(dot)inmotionhosting(dot)com> unrelated to the Intesa Sanpaolo's domain and contains a very generic text, although the cybercriminal had the graphic foresight to include the well-known Intesa Sanpaolo logo, that could mislead the user.
The purpose is to get the recipient to click on the link Clicca qui (Click here) which, we would like to point out, connect to a page that has nothing to do with the Intesa Sanpaolo's site, but has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
January 20, 2023 ==> Phishing Mooney
«SUBJECT: <
Verifica del tuo account! > (
Verification of your account!)
We examine below a new phishing attempt that comes as a false communication from
Mooney, the Italian Proximity Banking & Payments company.
The message informs the recipient that the account verification process has not been completed, because the phone number associated with the account has not yet been confirmed.
It then invites him to verify the personal information entered in his account and validate the phone number, in order to receive notifications and alerts about the service, through the following link:
accedi al mio account (login to my account)
This time the phishing campaign simulates a communication from the Italian online payment company
Mooney, which is clearly unrelated to the mass sending of these emails, that are real scams, whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
Examining the text of the message, we notice from the outset that the sender's e-mail address <
tina(dot)smith(at)nf(dot)sympatico(dot)ca> is clearly not from
Mooney's official domain, and this should be very suspicious.
Anyone who unluckily clicks on the link
accedi al mio account (login to my account) will be redirected to an anomalous WEB page, which has nothing to do with the official
Mooney's website, but which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
January 19 and 20, 2023 ==> Phishing Aruba
Below we report 2 phishing attempts that comes as a false communication from
Aruba.
EXAMPLE 1
«ATTENZIONE! Hai prodotti in scadenza. REF: IT31025891» (WARNING. You have expiring products . REF: EN31025891)
EXAMPLE 2
«[Promemoria] Hai (2) messaggi non inviati» ([Reminder] You have (2) unsent messages.)
In the first example, the customer is notified that his domain on
Aruba is about to expire, and then invites him to renew before the expiration. The second attempt, on the other hand, reports of a problem in e-mail delivery due to a new regulatory policy adopted by
Aruba, which seems to prevent the proper delivery of some messages. Therefore it invites the victim to retrieve his suspended messages within 72 hours.
In both cases, the purpose is to lead the user to click on a link, such as those below:
RINNOVA ORA CON UN CLICK (RENEW NOW WITH ONE CLICK)
Clicca qui per recuperare il tuo messaggio (Click here to retrieve your message)
Clearly, the well-known web hosting, e-mail and domain registration services company Aruba is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
To detect these phishing attempts, it is necessary, first of all to examine the sender's e-mail address which, as we can see in the 2 reported cases: <
rinnovali(at)sys-update(dot)cloud> and <
lecce(at)abitarepesolino(dot)it>, do not come from
Aruba's official domain.
Very often these messages are poorly written emails that contain spelling errors or renewal requests for not expiring services, since they use urgency or data security to obtain user's information.
It's also important to examine the links or attachments that these messages contain, which usually redirect to a counterfeit website asking to enter your personal information (such as account username and password, or credit card number to make account renewals). If these data are entered, they will be used by cyber criminals
for illegal purposes.
January 18, 2023 ==> Phishing Account Posta Elettronica (Email Account)
«SUBJECT: <
Azione richiesta >
(Action required)
We examine below the phishing attempt that aims to steal the credentials of the victim's e-mail account.
The message, in English, informs the recipient that his mailbox password, which is reported, has expired on 18/01/2023. It then invites him to confirm his current password in order to continue using it. To proceed with the update, he will simply click on the following link:
Re-confirm Password
Examining the email, we see that the message comes from an email address not referable to the server that hosts the mailbox <
info(at)wmn(dot)cloudns(dot)ph>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
Re-confirm Password, you will be redirected to an anomalous WEB page, which, as you can see from the side image, has nothing to do with the e-mail account manager.
The page to which you are redirected, to enter your mail account credentials, is hosted on an abnormal address/domain, which we show below:
https[:]//fleek[.]ipfs[.]io/ipfs/QmSVxst1tt2seu4XN4QqK4RVRGEZNrDpc....
We always urge you to be careful and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber crooks, with all the associated easily imaginable risks .
January 18, 2023 ==> Smishing Amazon
This smishing attempt, which comes back this month, is behind a fake text message from
Amazon.
If you click on the link within the message, it sends you to a web page graphically deceptive in that it is very similar to the
Amazon page, where you are asked to participate in a short survey, for a chance to win a fantastic iPhone 14 Pro.
The web page, which we quote on the side, is graphically well laid out, and it looks like a must-have offer. In fact, we have been drawn among the 10 lucky users who will have a chance to win the fantastic prize...
"
Today, January 18, 2023, you have been chosen to participate in our survey. It will only take you a minute and you will receive a fantastic prize: Apple IPhone 14 PRO!"
The user, who is one of the 10 lucky winners drawn today, is asked below to participate in a short 4-question survey for a chance to win the new iPhone 14 Pro!
To justify this lucky draw and encourage the user to answer the short questions, it is reported that the survey is aimed at "
improving the quality of service for our users". This is to emulate the protection of Amazon's image and perception of users about service and quality that, for international brands, is very important.
Below are some comments from customers who seem to have already participated in the survey and who, more or less lucky, seem to have won the new IPhone 14 PRO. Obviously the purpose is to induce the user to participate.The subsequent questions are very general.
At the end of the survey, we finally get to a new screen that makes us select gift packs to win the prize, we have 3 attempts, Good Luck!...Once you have selected the boxes, they confirm our winning of the IPhone 14 PRO! Estimated delivery is 5-7 business days, and instructions on how to claim the prize are given....
Then, you should be directed to a further page to enter your shipping address and paying shipping charges.
Surely if so many users have been lucky why not try your luck? In any case, the amount required is really small....
Instead, the aim of cyber criminals is to induce the user to enter his sensitive data and credit card details that are requested for payment!
To conclude, we always urge you to be wary of advertisements/promotional messages that brag about "giving away" valuables, and avoid clicking on suspicious links which could lead to a counterfeit site, putting your most valuable data in the hands of cyber crooks.
January 14, 2023 ==> Phishing TV Samsung
SUBJECT: <
---Hai vinto un televisore Samsung--- >
(You won a Samsung television)
The following is a phishing attempt, hiding behind a false communication, that brags about the chance to win a new Samsung TV.
The message, which we quote on the side, is graphically well laid out, and looks like a must-have offer. In fact, if you select an Internet service provider from those listed, you have a chance to win the fantastic prize, by participating in a survey.
"
You have been selected to participate in our Loyalty Program for FREE! To receive this fantastic prize, all you need is a minute"
Examining the email, we notice that the message comes from a suspicious email address:<
el_janati(dot)hib(dot)fst(at)uhp(dot)ac(dot)ma>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who clicks on the link
VISUALIZZA PIANI DISPONIBILI (VIEW AVAILABLE PLANS) will be redirected to a web page, where you are asked to participate in a short survey to win the prize, a fantastic Samsung 4K TV!
From the screenshot shown, the site appears to be traceable to
Fastweb, but we can see that the page is hosted on an anomalous address/domain, which we report below:
https[:]//kaffirgramar[.]com/1449199...
By clicking on
Partecipa subito al sondaggio (
Join the survey now) you are directed to the next screens, where you are shown the 4 questions you must answer to win the prize.
At the end of the survey, we finally get to a new screen that makes us select gift packs to win the prize. Once we made our choices, we are confirmed to have won the Samsung TV, with estimated delivery in 5-7 business days, and instructions on how to claim the prize....
At this point you should be redirected to a further page, to enter your shipping address and paying shipping charges.
Surely if so many users have been lucky why not try your luck? In any case, the amount required is really small....
Instead, the aim of cyber criminals is just to induce the user to enter his sensitive data and credit card details, that are requested for payment!
The page to which you are referred, to enter your personal data, is hosted on an anomalous address/domain, which we report below:
https[:]//instagoodness[.]net/c/Cn4xFBF?s1...
To conclude, we always urge you to be wary of advertising/promotional messages that brag about "giving away" valuables, and avoid clicking on suspicious links which could lead to a counterfeit site, putting your most valuable data in the hands of cyber crooks for uses of their greatest interest and profit.
January 14 - 16, 2023 ==> Phishing Aruba - Rinnovo automatico (Automatic renewal)
«SUBJECT: <
Dominio in scadenza, per rinnovare? >
(Expiring domain, to renew?)
Here is a new phishing attempt that comes as a false communication from
Aruba.
The message informs the recipient that his domain hosted on
Aruba, linked to his mail account, will expire on
16/01/2023. It then warns him that, if the domain is not renewed, all the services associated with it will be deactivated, including the mailboxes, so he will no longer be able to receive and send messages. It therefore invites the user to renew the domain through the following link
:
RINNOVA IL DOMINIO (RENEW THE DOMAIN)
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
Examining the text of the message, we notice right away that the sender's e-mail address <
no.reply(at)tempestadisorrisi(dot)it> is not from the official domain of
Aruba.
Anyone who clicks on the link
RINNOVA IL DOMINIO (RENEW THE DOMAIN), will be redirected to an anomalous WEB page, which has nothing to do with the officiali
Aruba's website, but which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
January 13, 2023 ==> Phishing Account Posta Elettronica (Email Account)
«SUBJECT: <
la tua password scade >
(your password will expire)
We examine below another phishing attempt aimed to stea the credentials of the victim's e-mail account.
The message informs the recipient that his mailbox password, which is reported, will expire soon. It then invites him to confirm his current password, as it is very secure. To proceed with the update, he will simply click on the following link:
CONTINUA A UTILIZZARE LA PASSWORD ATTUALE (KEEP USING YOUR CURRENT PASSWORD)
Examining the email, we see that the message seems to come from an email address not traceable to the server hosting the mailbox <
info(at)boa(dot)org>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
CONTINUA A UTILIZZARE LA PASSWORD ATTUALE (KEEP USING YOUR CURRENT PASSWORD) will be redirected to an anomalous WEB page, which, as you can see from the image on the side, has nothing to do with the e-mail account manager.
The page to which you are redirected to enter your email account credentials, is hosted on an abnormal address/domain, which we show below
https[:]//ipfs[.]io/ipfs/QmaXK7cbS8vfVtijNdNN3r2BWbhC....
We always urge you to be careful and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber crooks, with all the associated easily imaginable risks .
January 12, 2023 ==> Phishing MediaWorld
SUBJECT: <
...CONGRATULAZIONI! Sei il vincitore di una nuovissima Playstation 5 >
(CONGRATULATIONS!!! You are the winner of a brand new Playstation 5)
Below is a phishing attempt, which is behind a false communication from
MediaWorld, that brags about a chance to win a new Playstation 5.
The message, which we quote on the side, is graphically well laid out, and looks like a must-have offer for video game fans. The well-known electronics and home appliances chain
MediaWorld, is giving a chance to win one of their products by participating in a survey.
"You have been selected to participate in our FREE Loyalty Program! All you need is a minute to receive this fantastic prize."
Examining the email, we notice that the message comes from an email address not traceable to
MediaWorld's email domain <
magueri(dot)naj(dot)fst(at)uhp(dot)ac(dot)ma>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who clicks on the link
RISPONDI SUBITO AL SONDAGGIO (ANSWER THE SURVEY NOW) will be redirected to a web page, where you are asked to participate in a short survey to win the prize, a fantastic Playstation 5!
Below are some comments from customers who appear to have already participated in the survey.
In the following Screenshots we can see the 4 questions you are asked to answer to win the prize.
At the end of the survey, we finally get to a new screen confirming our winning of the PlayStation 5, with estimated delivery in 5-7 business days, and instructions on how to claim the prize....
Next, you should be directed to a further page to enter your shipping address and pay shipping charges.
Surely if so many users have been lucky why not try your luck? In any case, the amount required is really small....
Instead, the aim of cyber criminals is just for the user to enter their sensitive data and credit card details that are requested for payment!
The page to which you are redirected, to enter your personal information, is hosted on an anomalous address/domain, which we report below:
https[:]//launchtothesky[.]net/c/4nrhICw?s1=102e3eaef8c0378ff32ea9....
To conclude we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links, whose links could lead to a counterfeit site, putting your most valuable data in the hands of cyber crooks
.
January 09, 2023 ==> SexTortion: "Leaked uncensored photos from your device..."
The SexTortion-themed SCAM campaign persists. The e-mail would seem to suggest that the scammer gained access to the victim's device, which he used to collect data and personal videos. Then he blackmailed the user by demanding payment of a sum of money, in Bitcoin, not to divulge among his email and social contacts, a private video of him viewing adult sites.
The following is an extract from the text, in English, of the email on the side:
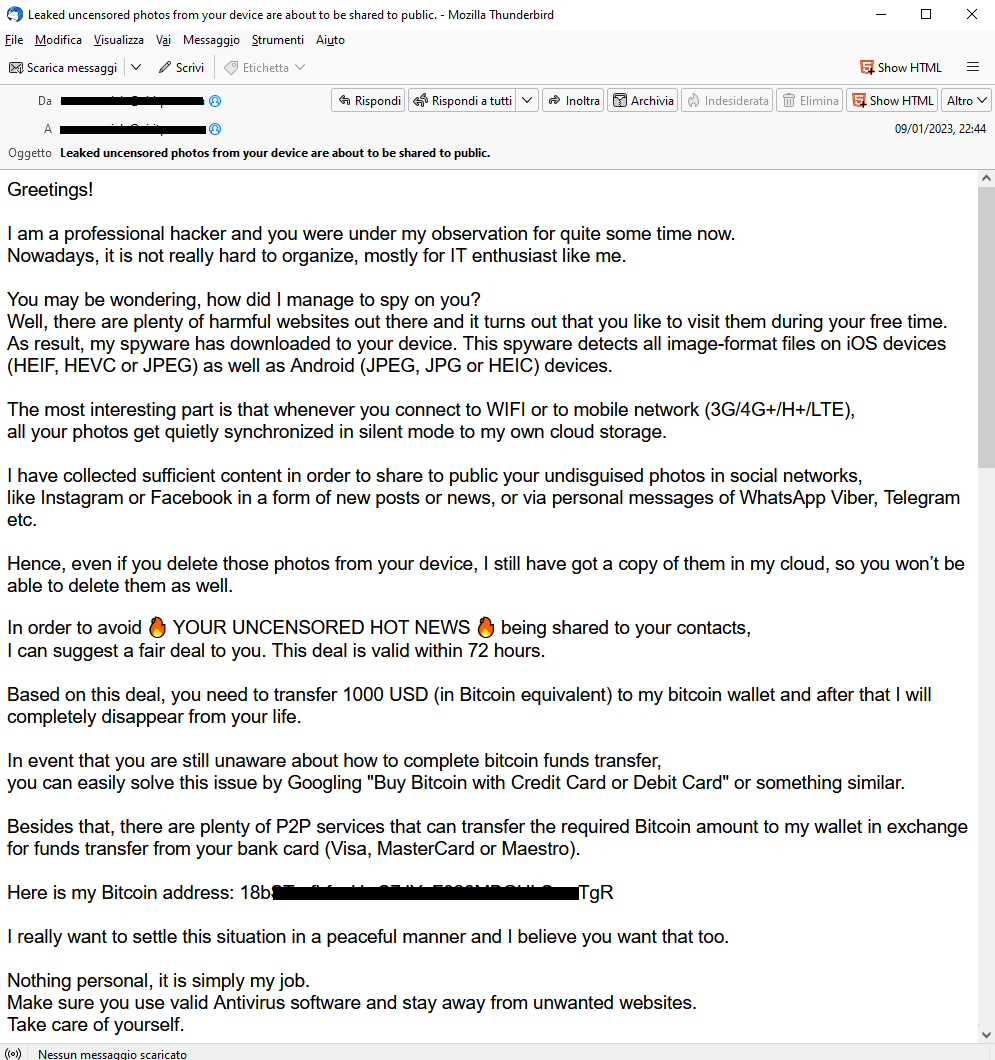 " I am a professional Hacker and you were under my observation for quite some time now. Nowadays, it is not really hard to organize, mostly for IT enthusiast like me. You may be wondering, how did I manage to spy on you? Well there are plenty of harmaful websites out there and it turns out that you like to visit them during your free time. AS result, my spyware has downloaded to your device. This spyware detects all image-format files on IOS devices (HEIF, HEVC or JPEG) as well as Android (JPEG, JPG or HEIC) devices. The most interesting part is that whenever you connect to WIFI or to mobile network(3G/4G+/H+/LTE), all your photos get quietly synchronized in silent mode to my own cloud storage. I have collected sufficient content in order to share to public your undisguised photos in social networks, like Instagram or Facebook in a form of new posts or news, or via personal messages of WhatsApp Viber, Telegram etc. Hence, even if you delete your photos from your device, I still have got a copy of them in my cloud, so you won't be able to delete them as well"
" I am a professional Hacker and you were under my observation for quite some time now. Nowadays, it is not really hard to organize, mostly for IT enthusiast like me. You may be wondering, how did I manage to spy on you? Well there are plenty of harmaful websites out there and it turns out that you like to visit them during your free time. AS result, my spyware has downloaded to your device. This spyware detects all image-format files on IOS devices (HEIF, HEVC or JPEG) as well as Android (JPEG, JPG or HEIC) devices. The most interesting part is that whenever you connect to WIFI or to mobile network(3G/4G+/H+/LTE), all your photos get quietly synchronized in silent mode to my own cloud storage. I have collected sufficient content in order to share to public your undisguised photos in social networks, like Instagram or Facebook in a form of new posts or news, or via personal messages of WhatsApp Viber, Telegram etc. Hence, even if you delete your photos from your device, I still have got a copy of them in my cloud, so you won't be able to delete them as well"
At this point you are prompted to send 1000 USD in Bitcoin to the wallet listed below: "18bXXXXXXXXXXXXXXXXXXXXXXTgR'. After receiving the transaction all data will be deleted, otherwise a video depicting the user, will be sent to all colleagues, friends and relatives, the victim has 72 hours to make the payment!
Examining the payments made on the wallet indicated by the cyber criminal as of 03/02/2023, we see 3 transactions totaling $1315.97.
In such cases we always urge you:
- not to answer these kinds of e-mails and not to open attachments or click lines containing unsafe links, and certainly NOT to send any money. You can safely ignore or delete them.
- If the criminal reports an actual password used by the user - the technique is to exploit passwords from public Leaks (compromised data theft) of official sites that have occurred in the past (e.g., LinkedIn, Yahoo, etc.) - it is advisable to change it and enable two-factor authentication on that service.
January 07, 2023 ==> Phishing Carrefour
SUBJECT: <
Hai vinto un Smeg Stand Mixer>
(You won a Smeg Stand Mixer)
We find the phishing attempt again, pretending to be a communication from
Carrefour, the French hypermarket chain.
The message informs the unsuspecting recipient of the chance to participate in their loyalty program, to win a fantastic prize: the "Smeg Stand Mixer".
It then invites the user to participate, via the following link:
INIZIA ORA (START NOW)
At first we notice that the alert email comes from an email address <
walad(dot)ima(dot)fst(at)uhp(dot)ac(dot)ma> that is clearly not from the
Carrefour's domain.
Anyone who unluckily clicks on the link
INIZIA ORA (START NOW) will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
January 03, 2023 ==> Phishing Subito
«SUBJECT: <
hai messaggi non ricevuti sul sito subito >
(hai messaggi non ricevuti sul sito subito)
Here is a new phishing attempt that comes as a false communication from
Subito.
The message informs the recipient that there are messages not received from his
Subito listings because the account has been spammed.
It then informs him that to unblock his mailbox, it is necessary to contact technical support, through the following link:
Cliccando qui (Clicking here)
Clearly, the well-known free classifieds company, Subito is unrelated to the mass sending of these emails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
Examining the text of the message, we notice right away that the sender's e-mail address <
messages(at)subito(dot)it> could mislead an inexperienced user, but it is not from the official
Subito's domain, since a label e-mail is probably used.
Anyone who unluckily clicks on the link,
Cliccando qui (Clicking here) will be redirected to an anomalous WEB page, which has nothing to do with the official website of Subito, but which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
January 02 -14 2023 ==> Phishing Carrefour
SUBJECT: <
>>>Hai vinto un Le Creuset : Codice di tracciamento#IT869.> (
You won a Le Creuset : Tracking Code#IT869.)
SUBJECT: <
--Hai vinto un Le Creuset---> (
You won a Le Creuset)
This new phishing attempt pretends to be a communication from
Carrefour, the French hypermarket chain.
The message informs the unsuspecting recipient to enter their loyalty program to win a fantastic prize: the new "La Creuset" pot.
It then invites the user to participate, via the following link:
INIZIA ORA (Start Now)
At first we notice that the alert email comes from the following email addresses
<khald(dot)dou(dot)fst(at)uhp(dot)ac(dot)ma> - <el_janati(dot)hib(dot)fst(at)uhp(dot)ac(dot)ma> which are clearly not from
Carrefour's domain, and which moreover is the same e-mail address used in
BRT's previous Phishing campaign.
Anyone who unluckily clicks on the link, will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
January 02 - 11 - 15, 2023 ==> Phishing BRT: Spedizione in attesa (Pending shipment)
«SUBJECT:
< .Questa è la tua occasione per ricevere .....> (This is your chance to receive...)
«SUBJECT:
< ...Abbiamo cercato di contattarti - per favore rispondi!..> (We have been trying to reach you - please reply!)
«SUBJECT:
< ---Abbiamo cercato di contattarti - È ora di eccitarsi.---> (We've been trying to reach you - It's time to get excited)
Here we find another phishing attempt, which was also circulating in December, hiding behind a false communication apparently from the
BRT service, regarding the delivery of an alleged package.
The message notifies the unsuspecting recipient that his package could not be delivered because there was no one to sign the delivery receipt. An alleged delivery code <34632900-371> is also reported. We notice that the email is graphically well laid out to make the message, which would appear to be from
BRT, more trustworthy. These messages are increasingly used to scam consumers who, more and more, use e-commerce for their purchases.
The message then invites the user to confirm the delivery address, to reschedule the shipment, by clicking on the following link:
CONTROLLA QUI (CHECK HERE)
The alert email comes from an email address <khald(dot)dou(dot)fst(at)uhp(dot)ac(dot)ma> that is clearly not from BRT's domain. Anyone who unluckily clicks on the link will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
January 01, 2023 ==> Phishing Q8
SUBJECT: <
Sfida il caro benzina la sorte: puoi vincere 200€>
(Challenge high Gasoline prices and luck: you can win €200)
We find again in this beginning of 2023, the following phishing attempt that pretends to be a communication from
Q8.
The message is very impactful as it concerns a very current issue that weighs heavily on the pockets of all Italians, that of rising fuel prices "
Sfida il caro benzina e la sorte"
(Challenge high Gasoline prices and luck)
The message leverages the chance to win a fuel voucher worth €200 by entering the lucky draw, via the following link:
PARTECIPA ORA (JOIN NOW)
First, we see that the alert email comes from an email address <
news(at)news.(dot)all29con99(dot)com> that is clearly not from the official domain of
Q8.
Anyone who unluckily clicks on the link
PARTECIPA ORA (JOIN NOW) will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
A little bit of attention and glance, can save a lot of hassle and headaches....
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on Phishing techniques for more details:
02/12/2022 15:04
- Phishing: the most common credential theft attempts in December 2022..
04/11/2022 17:27 - Phishing: the most common credential theft attempts in November 2022...
05/10/2022 11:55 - Phishing: the most common credential theft attempts in October 2022...
06/09/2022 15:58 - Phishing: the most common credential theft attempts in September 2022...
04/08/2022 16:39 - Phishing: the most common credential theft attempts in August 2022...
06/07/2022 12:39 - Phishing: the most common credential theft attempts in July 2022...
06/06/2022 14:30 - Phishing: the most common credential theft attempts in June 2022...
02/05/2022 11:06 - Phishing: the most common credential theft attempts in May 2022...
06/04/2022 16:51 - Phishing: the most common credential theft attempts in April 2022...
08/03/2022 17:08 - Phishing: the most common credential theft attempts in March 2022..
03/02/2022 16:25 - Phishing: the most common credential theft attempts in February 2022...
04/01/2022 09:13 - Phishing: the most common credential theft attempts in January 2022...
Try Vir.IT eXplorer Lite
 If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently.
Vir.IT eXplorer Lite has the following special features:
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs. We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
VirIT Mobile Security AntiMalware ITALIAN for ALL Android Devices
VirIT Mobile Security, the Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats and empowers the user to safeguard their privacy with an advanced heuristic approach (Permission Analyzer).
 TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings
TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings
You can upgrade to the PRO version by purchasing it directly from our website https://www.tgsoft.it/italy/ordine_step_1.asp
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities to our Research Center that allowed us to make this information as complete as possible.
How to send suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways:
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- Save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
 For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
TG Soft's C.R.A.M. (Anti-Malware Research Center)


 " I am a professional Hacker and you were under my observation for quite some time now. Nowadays, it is not really hard to organize, mostly for IT enthusiast like me. You may be wondering, how did I manage to spy on you? Well there are plenty of harmaful websites out there and it turns out that you like to visit them during your free time. AS result, my spyware has downloaded to your device. This spyware detects all image-format files on IOS devices (HEIF, HEVC or JPEG) as well as Android (JPEG, JPG or HEIC) devices. The most interesting part is that whenever you connect to WIFI or to mobile network(3G/4G+/H+/LTE), all your photos get quietly synchronized in silent mode to my own cloud storage. I have collected sufficient content in order to share to public your undisguised photos in social networks, like Instagram or Facebook in a form of new posts or news, or via personal messages of WhatsApp Viber, Telegram etc. Hence, even if you delete your photos from your device, I still have got a copy of them in my cloud, so you won't be able to delete them as well"
" I am a professional Hacker and you were under my observation for quite some time now. Nowadays, it is not really hard to organize, mostly for IT enthusiast like me. You may be wondering, how did I manage to spy on you? Well there are plenty of harmaful websites out there and it turns out that you like to visit them during your free time. AS result, my spyware has downloaded to your device. This spyware detects all image-format files on IOS devices (HEIF, HEVC or JPEG) as well as Android (JPEG, JPG or HEIC) devices. The most interesting part is that whenever you connect to WIFI or to mobile network(3G/4G+/H+/LTE), all your photos get quietly synchronized in silent mode to my own cloud storage. I have collected sufficient content in order to share to public your undisguised photos in social networks, like Instagram or Facebook in a form of new posts or news, or via personal messages of WhatsApp Viber, Telegram etc. Hence, even if you delete your photos from your device, I still have got a copy of them in my cloud, so you won't be able to delete them as well" If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently. TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings
TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis