PHISHING INDEX
Below are the most common email phishing attempts detected by TG Soft's Anti-Malware Research Center in
July 2023:
24/07/2023 =>
Aruba - Avviso di disattivazione e-mail (Email deactivation notice)
24/07/2023 =>
Agenzia delle Entrate (Revenue Agency)
17/07/2023 =>
Banca Popolare di Sondrio
11/07/2023 =>
Banca Sella (Sella Bank)
11/07/2023 =>
Istituto Bancario (Bank)
11/07/2023 =>
Agenzia delle Entrate (Revenue Agency)
10/07/2023 =>
SexTortion
10/07/2023 =>
Account di Posta - Storage Full
10/07/2023 =>
Ups
10/07/2023 =>
Aruba - Rinnova il dominio (Renew the domain)
09/07/2023 =>
MetaMask
03/07/2023 =>
Smishing Banca Popolare di Sondrio
03/07/2023 =>
Ups
03/07/2023 =>
EuroPages
These emails are intended to trick some unfortunate person into providing sensitive data - such as bank account information, credit card codes or personal login credentials - with all the possible easily imaginable consequences.
July 24, 2023 ==> Phishing Aruba - Avviso di disattivazione e-mail (Email deactivation notice)
SUBJECT: <
Avviso di disattivazione e-mail xxx@xxx>
(Email deactivation notice xxx@xxx)
Phishing attempts, pretending to be messages from the
Aruba brand, continued in July.
This time we are dealing with a computer fraud with a new look, compared to the ''classic''
Aruba phishing, previously analyzed.
The message invites the user to perform an email box update, to acquire more security on his account. He is therefore urged to start the update procedure through the attached html page.
Although the alert is graphically deceptive, due to the logo's presence and the inclusion of a kind of banner advertisement allegedly from
Aruba, there are some details that should not go unnoticed. First of all, the message contains some grammatical inaccuracies and syntax errors. We also find that the sender's email address <
eser_46(at)hotmail(dot)com> is anomalous and not traceable to the official
Aruba's domain. This last element is a distinguishing feature of phishing campaigns that we should pay close attention to.
In order to induce the victim to promptly upgrade his mailbox, a maximum time limit of 7 days is also given, after which the mailbox will be deactivated.
Anyone who unluckily clicks and opens the attached html page named
Aruba[.]it[.]html, will actually be redirected to the page displayed below.
As we can see, the page shown was created to resemble the real one but in fact has nothing to do with the official
Aruba's website.
In fact, we expect to be on a page hosted on
Aruba's legitimate site. Instead, in this specific case, we are even inside a local html page. Proceeding to enter the requested data - specifically the email address and password - these will be delivered to the cyber criminals behind the scam, who will use them for criminal purposes.
We remind, always and in any case, that
the well-known web hosting, e-mail and domain registration services company Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
July 24, 2023 ==> Phishing Agenzia delle Entrate (Revenue Agency)
SUBJECT: <
Avviso Raccomandata #AR308L8T7V8>
(Registered mail notice #AR308L8T7V8)
Below we analyze another phishing attempt, that comes as a fake message from the
Agenzia delle Entrate (
Revenue agency).
The message informs the recipient that a new notification addressed to him is available with the following information:
- Issuing Institution: Revenue Agency
- Holder: Recipient's email address
- Subject: Administrative Notification
- Protocol n.: AR308L8T7V8
Examining the alert we immediately observe its anomalous email address i.e. <agenzia[.]entrate(at)avisi(dot)com>, which is not hosted on the official domain of the Agenzia delle Entrate's website (Revenue Agency).
The notice is also very generic; in fact it addresses a ''
Dear Taxpayer'' without reporting the recipient's first and last name. We do not even find clear references about the Holder, in the information concerning the administrative notification. We only find the email address of the recipient, which is not a tax identification.
Two links are then provided below to access the notification:
"https[:]//www[.]agenziaentrateriscossione[.]gov[.]it/it"
"notifica"
By placing the cursor on the links, we can see that both of them point to :
https[:]//cstxxonid[.]com
which is definitely suspicious.
In any case, anyone who unfortunately clicks on the links will be redirected to a counterfeit web page on the
Agenzia delle Entrate's site
(Revenue Agency) , hosted on a domain quite similar to the institutional one.
From the image below we can see that the web page is graphically well done and mimics quite well the official website of the
Agenzia delle Entrate (Revenue Agency).
In order to make it more reliable and induce the victim to access the restricted area, the cyber-criminals also had the foresight to include at the bottom some authentic data of the
Agenzia delle Entrate (Revenue Agency), such as address and F.C./VAT number.
However, to access the Restricted Area, an email address and its password are required...so in fact, we are facing an attempt to steal our email account's credentials.
We also highlight that, in order to access the platform of the Agenzia delle Entrate (Revenue Agency), you need a specific identity within the Public Digital Identity System (SPID, CIE or CNS) or credentials issued by the Agenzia delle Entrate (Revenue Service). This should therefore make us more suspicious about the reliability of the request.
Considering all that, we urge you to pay close attention to any misleading details. We should always remember - as a good rule before proceeding to enter sensitive data -
to verify the url address of the authentication form and assess the legitimacy of the request itself.
Obviously the Agenzia delle Entrate (Revenue Service) is clearly uninvolved in the mass sending of these phishing campaigns. Anyway, in case of doubt, we urge you to check its official website, where scam attempts exploiting its brand are repeatedly reported.
July 17, 2023 ==> Phishing Banca Popolare di Sondrio
«SUBJECT:
<Attiva la tua nuova app SCRIGNOapp ! > (Activate your new SCRIGNOapp)
We analyze below a new phishing attempt, that comes as a fake e-mail from
Banca Popolare di Sondrio, trying to steal the home banking login credentials of the victim.
The message, allegedly from
Banca Popolare di Sondrio, informs of the opportunity to activate the new SCRIGNOapp, which provides easier and faster access to banking services. To ensure access to the full services offered by the banking institution, the activation must be completed within 7 days.
Clearly people who are not
Banca Popolare di Sondrio's customers, understand easier that this is a real scam. However even the customers of the bank can identify it as a real cyberscam attempt.
Let's see what are the alarm bells we should pay attention to.
First we notice that the message comes from an email address not traceable to the
Banca Popolare di Sondrio's domain. This is definitely anomalous and should immediately make us suspicious.
Secondly, we can also observe that there is no actual reference to
Banca Popolare di Sondrio as the sender of the message, not even in signature.
Furthermore it is highly peculiar that a link is sent with a request for home banking credentials, via e-mail
.
Anyone who unluckily clicks on the link
Attiva ora (
Activate now), will be redirected to an anomalous WEB page, which has nothing to do with the official
Banca Popolare di Sondrio's website
.
From the image on the side we can see that the web page is graphically well done and simulates quite well the official website of the new Scrigno portal of
Banca Popolare di Sondrio.
To make the whole thing more reliable and induce the victim to access the portal, the cyber-criminals also had the foresight to report, at the bottom, some authentic data of Banca Popolare di Sondrio, such as address and F.C../VAT number.
Scrolling down the page we also observe that comforting indications are provided on how to request assistance and block the account in case of need... all this with the aim of further reassuring the user on the authenticity of the portal, although many links within it do not lead to the expected pages.
Considering all that, we urge you to pay close attention to any misleading details. We should always remember - as a good rule before proceeding to enter sensitive data (in this case home banking credentials i.e. User Code and PIN) -
to verify the url address of the authentication form.
The page shown in this case is hosted on the url address:
https[:]//formxxxc[-]arles[.]xx/wp1/online/login[.]php
which has nothing to do with the official website of
Banca Popolare di Sondrio.
This DECEPTIVE page/ WEBSITE is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for malicious purposes.
July 11, 2023 ==> Phishing Banca Sella (Sella Bank)
«SUBJECT: <
Aggiornamento dell'Applicazione! >
(Application Update!)
We find again this month the phishing campaign spread through an e-mail, allegedely from
Banca SELLA which, exploiting stolen graphics or similar to the official site, tries to induce the unsuspecting recipient to do what requested and fall into this trap based on social engineering techniques
.
The message informs the recipient that "
Squadra Sella.it" (Team Sella.it), in order to provide a secure and reliable service, is carrying out a major update of the "
Sicurezza Sella" (Security Sella) application.
The recipient is then asked to complete the application update, which is mandatory, in order to continue using online banking services safely and without interruption.
To proceed with the application update, it will be sufficient to click on the following link:
Aggiornare (Update)
Examining the email we notice right away that the alert message comes from an email address not traceable to the
Banca SELLA's domain <
contact(at)eltech-systems(dot)it>.
This is definitely anomalous and should make us suspicious, even though the cybercriminal had the graphic foresight to include the well-known logo of the banking institution, that could mislead an inexperienced user.
The aim is to lead the recipient to click on the link
Aggiornare (Update) which, we would like to point out, links to a page that has nothing to do with the official site of
Banca SELLA, but has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
July 11, 2023 ==> Phishing Istituto Bancario (Bank)
SUBJECT: <
Copia del pagamento>
(Copy of the payment)
We find again this month the phishing campaign spread through an e-mail, that tries to pass itself off as an official communication from a well-known national banking institution - exploiting stolen graphics, or similar to the official site - in order to induce the unsuspecting recipient to do what requested, and fall into this trap based on social engineering techniques
.
The message notifies the unsuspecting recipient that on July 11, 2023, a Single European Transfer was made to the company's bank account; they are then asked to confirm the payment sent, via the link contained in the email "Conferma IL PAGAMENTO.shtml" (Confirm the payment).
We can see from the outset, that the alert message comes from an e-mail address <mirosart(dot)pop(at)hotmail(dot)com> highly suspicious and contains a very generic text, although the cybercriminal had the graphic foresight to include the well-known logo of the banking institution, that might mislead the user.
The purpose is to get the receiver to open the attachment that has already been reported as a DECEPTIVE file/page. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
July 11, 2023 ==> Phishing Agenzia delle Entrate (Revenue Agency)
SUBJECT:: <
Avviso Raccomandata #AR3075R1DA0> (
Registered mail notice #AR3075R1DA0)
Below we analyze a new phishing attempt coming through an e-mail, which tries to pass itself off as an official communication from the
Agenzia delle Entrate(Revenue Agency).
The message, as we can see from the image, informs the recipient that there is a new "Administrative Notification" available, that has been registered under No. "AR3075R1DA0", addressed to him.
Two links to access the notification are then provided, below:
"https[:]//www[.]agenziaentrateriscossione[.]gov[.]it/it" o "notifica"
Clearly, this is an attempt at credential theft that has nothing to do with the
Agenzia delle Entrate (Revenue Agency), which is unrelated to the mass sending of these e-mails whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
Examining the text of the message, we notice right away that the sender's e-mail address <
entrate(at)agency(dot)com>, is not from the official domain of the
Agenzia delle Entrate (Revenue Agency).
Anyone who unluckily clicks on one of the two links given, will be redirected to an anomalous WEB page, which has nothing to do with the official website of the
Agenzia delle Entrate (Revenue Agency), and which we quote below:
https[:]//northbayrestaurantweek[.]com/?....
The landing page has already been reported as a DECEPTIVE page /SITE.In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
July 10, 2023==> SexTortion "You have an outstanding payment."
This month we find again the SexTortion-themed SCAM campaign. The email suggests that the scammer accessed the victim's device since he reports the email password as proof of the breach. He then claims the collection of data and personal videos, and then blackmails the user by demanding payment of a sum of money, in the form of Bitcoin, not to divulge among his email and social contacts a private video of him looking at adult sites.
The following is an extract from the text of the email on the side:
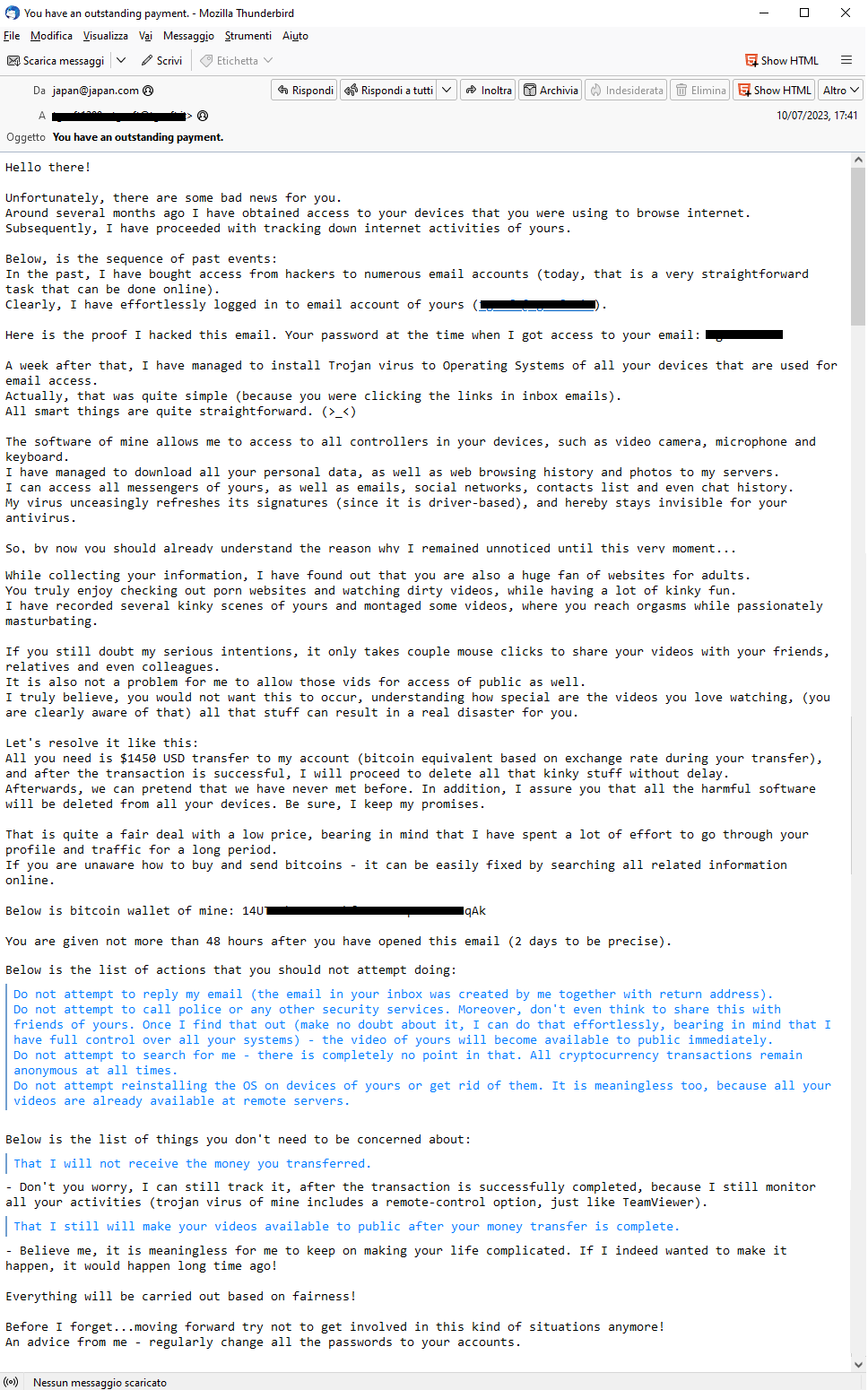
"Unfortunately, there are some bad news for you. Around several months ago I have obtained access to your devices that you were using
to browse internet. Subsequently, I have proceeded with tracking down internet activities of yours. Below is the sequence of past events: in the past I have bought access from hackers to numerous email accounts (today that is a vey straightforward task task that can be done online). Clearly, I have effortlessly logged in to email account of yours (*****). here is the proof I hacked this email. Your password at the time I got access (****).
A week after that I have managed to install to install trojan virus to Operating Systems of all your devices that are used for email access. Actually that was quite simple (because you were clicking the links in the inbox emails)... The software of mine allows me to access to all controllers in your devices, such as videocamera, microphone and keyboard. I have managed to download all your personal data , as well as browsing history and photos to my servers. I can access all messangers of yours, as well as social network, contact list and even chat history. My virus unceasingly refreshes its signatures (since it is driver based) and hereby stays invisible for your antivirus.So, by now you should already understand the reason why I remained unnoticed until this very moment. While collecting your information, I have find out that you are also a huge fan of websites for adults...I have recorded several kinky scenes of yours and montaged some videos..
If you still doubt my serious intentions, it only takes couple of mouse clicks to share your videos with your frineds, relatives and even colleagues."
You are then asked to send $1450 USD in Bitcoin to the wallet listed below: "
14UXXXXXXXXXXXXXXXXXXXXXXXqAk'.After receiving the transaction all data will be deleted, otherwise a video depicting the user, will be sent to all colleagues, friends and relatives, the victim has 48 hours to make the payment!
Examining the payments made on the wallet as of
13/07/2023, it shows 1 transaction amounting to 1424.97 USD.
In such cases we always urge you:
- not to answer these kinds of e-mails and not to open attachments or click lines containing unsafe links, and certainly NOT to send any money. You can safely ignore or delete them
- If the criminal reports an actual password used by the user - the technique is to exploit passwords from public Leaks (compromised data theft) of official sites that have occurred in the past (e.g., LinkedIn, Yahoo, etc.) - it is advisable to change it and enable two-factor authentication on that service
July 10, 2023 ==> Phishing Account Posta Elettronica (Email Account)
SUBJECT: <
NOTICE!!! Email Storage Full>
We analyze below another phishing attempt aimed at stealing the victim's e-mail account credentials.
The message, in English, informs the recipient that the storage space in his mailbox is full, and that he may not be able to receive and send e-mail. It then invites him to clean his mailbox, to recover storage space or to purchase new additional space, through the following link:
Clean up space
Examining the email, we notice that the message comes from an email address not traceable to the server that hosts the mailbox <
no-reply(at)gsmedi(dot)com>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
Clean up space,
will be redirected to an anomalous WEB page, which has nothing to do with
with the server hosting the mailbox, but which has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
July 10, 2023 ==> Phishing Aruba - Rinnova il dominio (Renew the domain)
SUBJECT: <
Promemoria: fattura per € 5,99 in attesa di pagamento>
(Reminder: invoice for € 5.99 awaiting payment)
Here we find another phishing attempt that comes as a false communication from
Aruba.
The message informs the recipient that his domain, hosted on
Aruba and linked to his e-mail account, will expire on
10/07/2023. It then warns him to manually renew his services to avoid the cancellation of the account and the deactivation of all the services associated with it - including the mailboxes - and the stop to the use of messages. It then invites the user to log in to renew services, through the following link:
RINNOVA IL DOMINIO (RENEW THE DOMAIN)
Clearly, the well-known web hosting, e-mail and domain registration services company Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
Examining the text of the message, we notice right away that the sender's e-mail address
<nfo82(at)pagafatturaarubaitaly(dot)com> does not come from the official domain of
Aruba.
Anyone who unluckily clicks on the link
RINNOVA IL DOMINIO (RENEW THE DOMAIN), will be redirected to an anomalous WEB page, which has nothing to do with the official
Aruba's website, but which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
July 09, 2023 ==> Phishing MetaMask
«SUBJECT
: <Metamask: Your Account Will be Temporary Down.>
We analyze below a new phishing attempt aimed at stealing the victim's cryptocurrency "wallet" login credentials from San Francisco-based company
MetaMask.
MetaMask is a cryptocurrency software wallet used to interact with the Ethereum blockchain. It allows users to access their Ethereum wallet via a browser extension or mobile app..
The message, in English, which we examine below, informs the recipient that, due to an update of their databases, all
MetaMask users must update their account. It then invites him to make the update as soon as possible and in any case within 24 hours, otherwise it will be deleted and, until he makes the update, the account will remain inactive. To proceed, he must click on the following link:
Update Information
Examining the e-mail, we notice that the message comes from a highly suspicious e-mail address, not traceable to the official
MetaMask's domain <
techsupport(at)smartjoules(dot)in>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link Update Information, will be redirected to an anomalous WEB page, which has nothing to do with the official MetaMask's website, but which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
July 03, 2023 ==> Smishing Banca Popolare di Sondrio (Sondrio Popular Bank)
We analyze below a new smishing attempt aimed at obtaining sensitive data by sending a fraudulent text message.
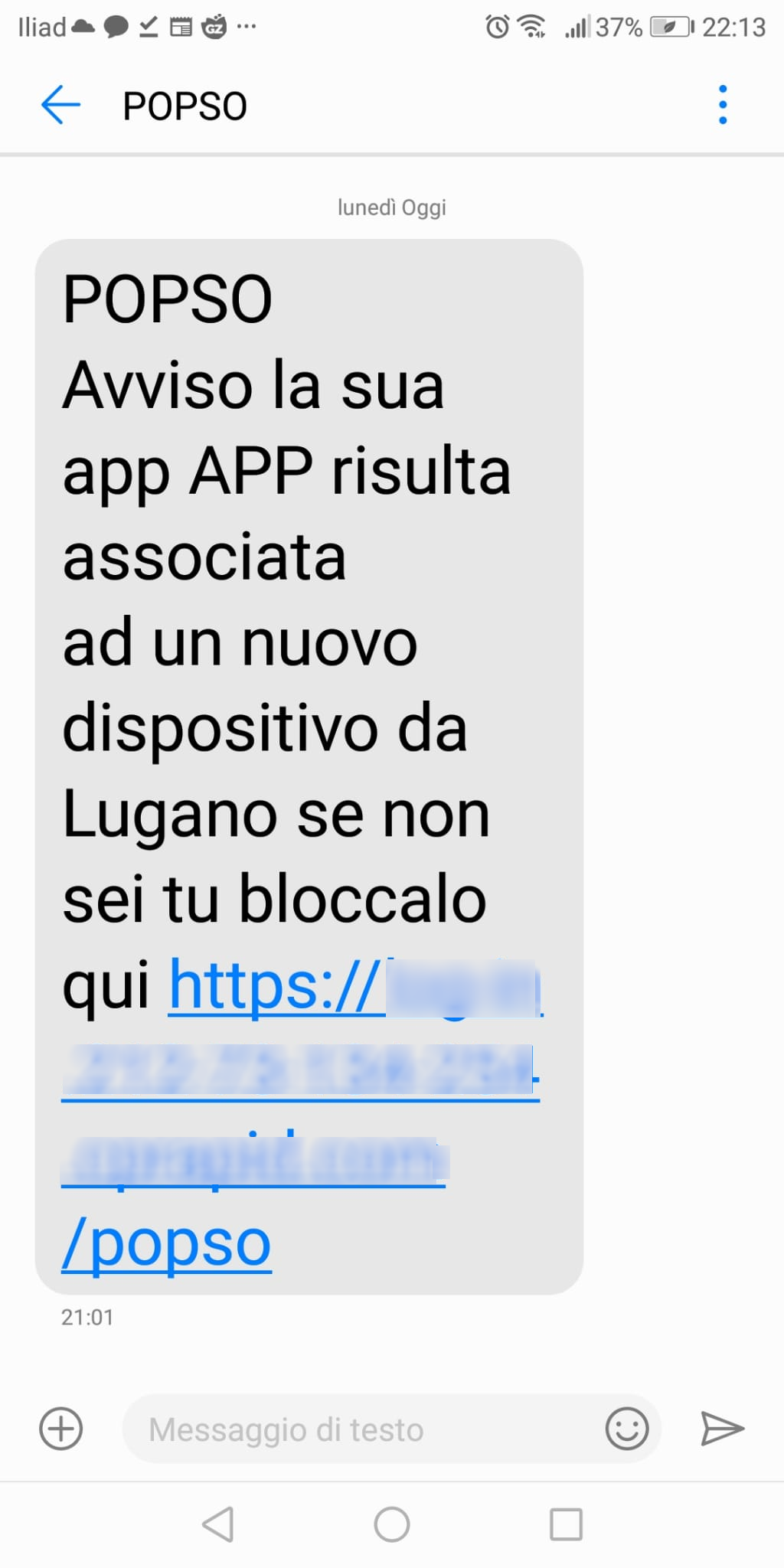
The message, shown on the side, comes from POPSO, which appears to correspond to the acronym for Banca Popolare di Sondrio (Sondrio Popular Bank), and alerts the unsuspecting recipient, that a new device from Lugano seems to be associated with its APP. To block the device it is necessary to click on the link
"https[:]//log-in[.]212-73-xxx-2xxxx[.]cprxxx[.]com/popso"
The text message refers to abnormal access via the app linked to the well-known credit institution.
Through the false detection of a suspicious transaction, the criminals induce the user to promptly log into his home banking for verification, so that they can steal his credentials.
Clearly, for those who are not customers of Banca Popolare di Sondrio (Sondrio Popular Bank), it is more intuitive to understand that this is a real scam. However even for the customers of the institution, it is not difficult to detect the computer fraud attempt.
Already at a glance, in fact, we notice that the link given in the text message is anomalous and certainly not traceable to the official website of Banca Popolare di Sondrio (Sondrio Popular Bank).
We remind you that the communication channels used by financial institutions to report any anomalous access are quite different from sending an alert text message to the victim.
Anyone who unluckily clicks on the link, will be redirected to an anomalous WEB page, which has nothing to do with the official Banca Popolare di Sondrio's website, but which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
03 - 10 July 2023==> Phishing Ups
«SUBJECT
: <Abbiamo bisogno della tua conferma per spedire il pacco!> (We need your confirmation to ship the package!)
We analyze below a new phishing attempt pretending to be an email from
Ups that aims to steal the victim's account login credentials.
The message, seemingly from the well-known courier company
Ups, warns of a package awaiting delivery. To unlock the delivery, the user is asked to log into his account through the following link:
Pianifica la tua consegna (Schedule your delivery)
To make it more trustworthy, more detailed information about the alerted shipment is given, such as the delivery number 190039 ES. Examining the email we notice, however, that the message comes from an email address not traceable to the official
Ups domain <
upssacostumerservice(at)rencontres2e(dot)com>. This is definitely anomalous and should, at the very least, make us suspicious. In addition a payment of 1.90 Euro is requested to proceed, and this is very suspicious.
Anyone who unluckily clicks on the link
Pianifica la tua consegna (Schedule your delivery), will be redirected to an anomalous WEB page.
From the side image we notice that, the web page to which we are redirected, requests a set of personal data in order to verify the information linked to the
Ups account.
At a glance, however, we notice that the login page is hosted on an anomalous address/domain, which has nothing to do with the official
Ups site:
https[:]//yoakenomyu[.]com/it/
numerodiriferimento[dot]ups[dot]com..
Continuing, if we try to log into the account by entering fictitious data and clicking on
Continue > we find a new screen, hosted on the same anomalous url address seen previously. This time it requires us to confirm the payment related to the 1.90 Euro storage fee by entering our own credit card details.
Both forms examined, require the input of sensitive data: first personal data such as first name, last name C.F. etc, and then our credit card codes.
Therefore, we urge you to be careful because, when you enter your data, they will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks .
July 03, 2023 ==> Phishing EuroPages
«SUBJECT
: <Heinrich: Ti ha inviato un messaggio di richiesta del prodotto> (Heinrich: He sent you a product request message.)
We find again this month the following phishing attempt, coming as a false
communication from
EuroPages and aimed to steal the victim's account login credentials.
The message seems to come from
EuroPages, the largest international B2B sourcing platform, and notifies the user that a message from a certain "Heinrich" has arrived, concerning the user's product listed on EuroPages. It then invites him to log into his account, to view the inquiry message, via the following link:
ACCEDI AL MIO ACCOUNT (LOGIN TO MY ACCOUNT)
Examining the email, we realize that the message comes from an email address not traceable to the official
EuroPages domain <
info(at)italcerchio(dot)it>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
ACCEDI AL MIO ACCOUNT, (LOGIN TO MY ACCOUNT),,
will be redirected to an anomalous WEB page.
From the side image, we notice that the web page seems more relatable to the Aruba page. In fact its well-known logo is shown, and you are prompted to log in to your account to confirm your identity and to be redirected to the EuroPages site to view the request message concerning your product
At a glance, however, we notice that the login page is hosted on an anomalous address/domain...
https[:]//3dniti[.]ru/wp-admin/user/Mainjsp[.]beta[.]aruba_2Mail.....
If you enter your own data on this FORM, to carry out their verification/confirmation, the data will be sent to a remote server and used by cyber crooks with all the related, easily imaginable, risks.
A little bit of attention and glance, can save a lot of hassle and headaches....
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on Phishing techniques for more details:
07/06/2023 15:57
- Phishing: the most common credential and/or data theft attempts in June 2023...
03/05/2023 17:59
- Phishing: the most common credential and/or data theft attempts in May2023...
05/04/2023 17:34 - Phishing: the most common credential and/or data theft attempts in April2023...
03/03/2023 16:54 - Phishing: the most common credential and/or data theft attempts in March 2023....
06/02/2023 17:29 - Phishing: the most common credential and/or data theft attempts in February 2023...
02/01/2023 15:28
- Phishing: the most common credential and/or data theft attempts in January 2023...
02/12/2022 15:04
- Phishing: the most common credential and/or data theft attempts in December 2022..
04/11/2022 17:27 - Phishing: the most common credential and/or data theft attempts in November 2022.....
05/10/2022 11:55 - Phishing: the most common credential and/or data theft attempts in October 2022...
06/09/2022 15:58 - Phishing: the most common credential and/or data theft attempts in September 2022...
04/08/2022 16:39 - Phishing: the most common credential and/or data theft attempts in August 2022...
06/07/2022 12:39 - Phishing: the most common credential and/or data theft attempts in July 2022...
06/06/2022 14:30 - Phishing: the most common credential and/or data theft attempts in June 2022...
Try Vir.IT eXplorer Lite
 If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
Vir.IT eXplorer Lite has the following special features:
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- fully interoperable with other AntiVirus software and/or Internet Security products (both free and commercial) already installed on your computer. It doesn't need any uninstallation and it doesn't cause slowdowns, as some features have been appropriately reduced to ensure interoperability with the AntiVirus software already on your PC/Server. This, however, allows cross-checking through the scan;
- it identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M
- proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
VirIT Mobile Security AntiMalware ITALIAN for ALL AndroidTM Devices
VirIT Mobile Security Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats, and empowers the user to safeguard their privacy with an advanced heuristic approach (Permission Analyzer).
 TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings
TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings
You can upgrade to the PRO version by purchasing it directly from our website=> click here to order
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities, to our Research Center that allowed us to make this information as complete as possible.
How to send suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways:
- any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
 For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
TG Soft's C.R.A.M. (Anti-Malware Research Center)



 If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS. TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings
TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis