INDICE dei PHISHING
Di seguito riportiamo i tentativi di phishing a mezzo email più comuni, rilevati dal Centro Ricerche Anti-Malware di TG Soft nel mese di
settembre 2022:
29/09/2022 =>
Chick-fil-A Gift Card
27/09/2022 =>
Teams
27/09/2022 =>
BRT Spedizione in attesa
26/09/2022 =>
Intesa Sanpaolo
25/09/2022 =>
BRT
20/09/2022 =>
Aruba - Dominio scaduto
14/09/2022 =>
SexTortion
13/09/2022 =>
Smishing DM
13/09/2022 =>
Account di posta
05/09/2022 =>
Aruba - Dominio scaduto
05/09/2022 =>
Aruba iCloud
Queste email hanno lo scopo di ingannare qualche malcapitato inducendolo a fornire dati sensibili, come le informazioni del conto corrente, i codici della carta di credito o credenziali di accesso personali, con tutte le possibili conseguenze facilmente immaginabili.
29 Settembre 2022 ==> Phishing Chick-fil-A Gift Card
OGGETTO: <
You're Invited: To Redeem Your $100 Chick-Fil-A reward>
Questo nuovo tentativo di phishing si spaccia per una falsa comunicazione da parte di
Chick-fil-A, catena di fast food americana.
Il messaggio, in lingua inglese, informa il ricevente che è stato selezionato tra i clienti per la vincita di una Gift Card del valore di 100$.
Quindi invita l'utente a partecipare
, attraverso il seguente link:
CLICK HERE!
In prima battuta notiamo che il testo dell'email è molto generico e scarno. Inoltre la mail di alert giunge da un indirizzo email <
ExclusiveReward(at)chickfilasurvey(dot)us> che non proviene dal dominio ufficiale di
Chick-fil-A.
Chi dovesse malauguratamente cliccare sul link
CLICK HERE! verrà dirottato su una pagina WEB che non ha nulla a che vedere con il sito ufficiale di
Chick-fil-A, ma che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali..
27 Settembre 2022 ==> Phishing Teams
«OGGETTO: <
**** conferenza>
Questo nuovo tentativo di phishing giunge da una finta e-mail da parte di
Teams, la piattaforma di teleconferenza.
Il messaggio sembra l'invito alla partecipazione di una teleconferenza tramite la nota piattaforma di comunicazione Teams. Nel messaggio viene indicato l'orario e il giono della conferenza programmata <<L'incontro è previsto per le 9 di domani mattina>> e il seguente link per partecipare:
Clicca qui per accettare l'invito alla riunione
Il messaggio di alert giunge da un indirizzo email <conferenza-id95(dot)****(at)bambola-sbc(dot)com> estraneo al dominio di Teams e contiene un testo estremamente scarno e conciso.
L'intento è quello di portare il ricevente a cliccare sul link:
Clicca qui per accettare l'invito alla riunione
che, ci preme precisarlo, rimanda ad una pagina che non ha nulla a che vedere con il sito di
Teams ma che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali..
27 Settembre 2022 ==> Phishing BRT: Spedizione in attesa
«OGGETTO: < Abbiamo bisogno della tua conferma per spedire il tuo ordine *****>
Ecco che ritroviamo un altro tentativo di phishing, che si cela dietro a una falsa comunicazione giunta apparentemente dal servizio di
BRT, relativamente alla consegna di un presunto pacco.
II messaggio segnala all'ignaro ricevente che non è stato possbile consegnare il suo pacco in quanto non c'era nessuno che potesse firmare la consegna. Viene riportato anche un presunto codice di consegna <
34632900-371>. Notiamo che la mail è graficamente ben impostata per far sembrare più attendibile il messaggio, che sembrerebbe provenire da
BRT. Questi messaggi vengono sempre più utilizzati per perpetrare la truffa ai danni dei consumatori che utlizzano sempre più l'e-commerce per i propri acquisti.
Il messagio invita quindi l'utente a confermare l'indirizzo di consegna per riprogramare la spedizione, cliccando sul seguente link:
CONTROLLA QUI
La mail di alert giunge da un indirizzo email <
admin.=?*/{B?jGeIZbuIAelPu?(at)doorp(dot)org(dot)uk> che non proviene chiaramente dal dominio di BRT. Chi dovesse cliccare sul link verrà rimandato su una pagina web, che simula graficamente la pagina di
BRT e che avvisa di 1 messaggio da aprire.
Notiamo tuttavia, nell'immagine di lato, che l'indirizzo url presente sulla barra del broswer non ha proprio nulla a che vedere con il dominio autentico di
BRT:
https[:]//reelingmoon[.]com/01ffe6cdd...
Cliccando poi su ''Conferma'' veniamo catapultati su un'altra videata dove ci viene segnalato che la consegna del pacco è in sospeso e viene riportato un presunto codice di tracciamento per riprogrammare la consegna del pacco...
Proseguendo, dopo aver cliccato su ''Pianifica la consegna'' ci viene proposta una nuova videata
|
La videata che segue ci dà informazionoi sullo stato del pacchetto "Fermato all'hub di distribuzione" e ci invita a scegliere la modalità per predisporre la nuova consegna, al costo di € 1,95.
|
La successiva schermata ci richiede come preferiamo che venga effettuata la consegna del pacco: "Desidero che me lo consegnino" o
"Lo ritirerò di persona".
|
Seguono altre 2 domande come la precedente, dove ci viene richiesto dove preferiamo che venga effettuata la consegna del pacco: "
A casa" o "
A lavoro" e quando preferiamo che venga consegnato: "Giorni lavorativi" o "Fine settimana".
Dopo aver selezionato le nostre preferenze, finalmente arriviamo ad una nuova videta che ci conferma l'invio del pacco, con consegna stimata in 3 giorni....A questo punto si dovrebbe venir rimandati su un'ulteriore pagina per l'inserimento dei propri dati di contatto e il pagamento delle spese di spedizione di €1,95.
Dall'immagine di lato notiamo che vengono effettivamente richiesti i propri dati personali per l'invio del pacco e successivamente il pagamento. Come si può notare la pagina di accesso è ospitata su un indirizzo/dominio anomalo e che chiaramente a non ha nulla a che fare con
BRT...
https[:]//greatstuffforyout[.]com/c/1422t41g?s1=102da120dd55...
Lo scopo di tutto questo è indurre l'utente ad inserire i suoi dati personali.
In conclusione vi invitiamo sempre a diffidare da qualunque email che richieda l'inserimento di dati riservati, evitando di cliccare su link sospetti, i cui collegamenti potrebbero condurre ad un sito contraffatto difficilmente distinguibile dall'originale, mettendo i vostri dati più preziosi nelle mani di cyber-truffatori per usi di loro maggiore interesse e profitto.
26 Settembre 2022 ==> Phishing Intesa Sanpaolo
«OGGETTO: <
Re:Annullate immediatamente questa transazione!>
Questo nuovo tentativo di phishing giunge da una finta e-mail da parte di
Intesa Sanpaolo.
Il messaggio segnala all'ignaro ricevente che sono state rilevate delle attività non autorizzate sul conto, viene indicata per completezza la data e l'ora di accesso e il pagamento non autorizzato di Euro 207,98, che è stato bloccato dal sistema. Se il pagamento non è stato autorizzato dal cliente, è necessario cliccare sul link di seguito e seguire la procedura di rimborso:
Accedere al proprio account
Il messaggio di alert giunge da un indirizzo email <info-HJREBWQC7660AV4J8X32(at)shisha-galerie(dot)de> estraneo al dominio di Intesa Sanpaolo e contiene un testo che, oltre ad essere estremamente scarno e conciso, è molto generico.
L'intento è quello di portare il ricevente a cliccare sul link:
Accedere al proprio account
che, ci preme precisarlo, rimanda ad una pagina che non ha nulla a che vedere con il sito di
Intesa Sanpaolo ma che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali..
25 Settembre 2022 ==> Phishing BRT
«OGGETTO: <
BRT - Avviso spedizione in consegna 986241136>
Segnaliamo questo mese diverse truffe di phishing attraverso e-mail che sembrano provenire da
BRT.
Il messaggio informa il cliente che il suo pacco non è stato consegnato, a causa delle "
spese di sdoganamento aggiuntive non pagate" . Lo avvisa quindi che il pacco verrà consegnato non appena veranno pagate le spese che ammontano a: 1,99 Euro.
Per procedere con il pagamento viene richiesto di cliccare sul seguente link:
Invia il mio pacco
Analizzando la mail notiamo che il messaggio, estremamente generico, proviene da un indirizzo email estraneo al dominio di
BRT <support(at)geors(dot)ir> . La mail inoltre non presenta alcun riferimento sul tracciamento del pacco gestito da
BRT, diversamente da quanto avviene nelle comunicazioni ufficiali e autentiche di questo tipo. Vengono però riportato in calce dei presunti dati identificati di BRT.
L'intento è quello di portare l'utente a cliiccare sul link
Invia il mio pacco in seguito verrà indirizzato su una pagina WEB malevola, che non ha nulla a che vedere con il sito di
BRT, ma che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali..
20 Settembre 2022 ==> Phishing Aruba - Dominio scaduto
«OGGETTO: <
Il dominio è scaduto ed è stato sospeso a causa di fatture non pagate ! >
Ecco un altro tentativo di phishing che giunge da una falsa comunicazione sempre da parte di
Aruba.
II messaggio informa il ricevente che il suo dominio ospitato su
Aruba scadrà il giorno
21/09/2022. Qualora il dominio non venga rinnovato entro tale data, questi e tutti i servizi associati, comprese le caselle di posta verranno disattivati. Invita quindi l'utente a rinnovare il dominio attraverso il seguente link:
RINNOVA IL DOMINIO
Chiaramente la nota azienda di servizi di web hosting, e-mail e registrazione domini,
Aruba è estranea all'invio massivo di queste mail che sono delle vere e proprie truffe il cui obiettivo resta, come sempre, quello di rubare dati sensibili dell'ignaro ricevente.
Analizzando il testo del messaggio notiamo fin da subito che l'indirizzo e-mail del mittente
<postmaster(at)consorziovallealesa(dot)it> non proviene dal dominio ufficiale di
Aruba.
Chi dovesse malauguratamente cliccare sul link
RINNOVA IL DOMINIO verrà dirottato su una pagina WEB anomala, che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali.
14 Settembre 2022 ==> SexTortion: "You have outstanding debt."
Ritroviamo questo mese la campagna SCAM a tema SexTortion. L'e-mail sembrerebbe far desumere che il truffatore abbia avuto accesso al dispositivo della vittima, che ha utilizzato per raccogliere dati e i video personali, per poi ricattare l'utente richiedendo il pagamento di una somma di denaro, sottoforma di Bitcoin, per non divulgare tra i suoi contatti mail e social
un suo video privato mentre guarda siti per adulti.
Di seguito Vi riportiamo un estratto del testo, in lingua inglese, di una mail tipo:
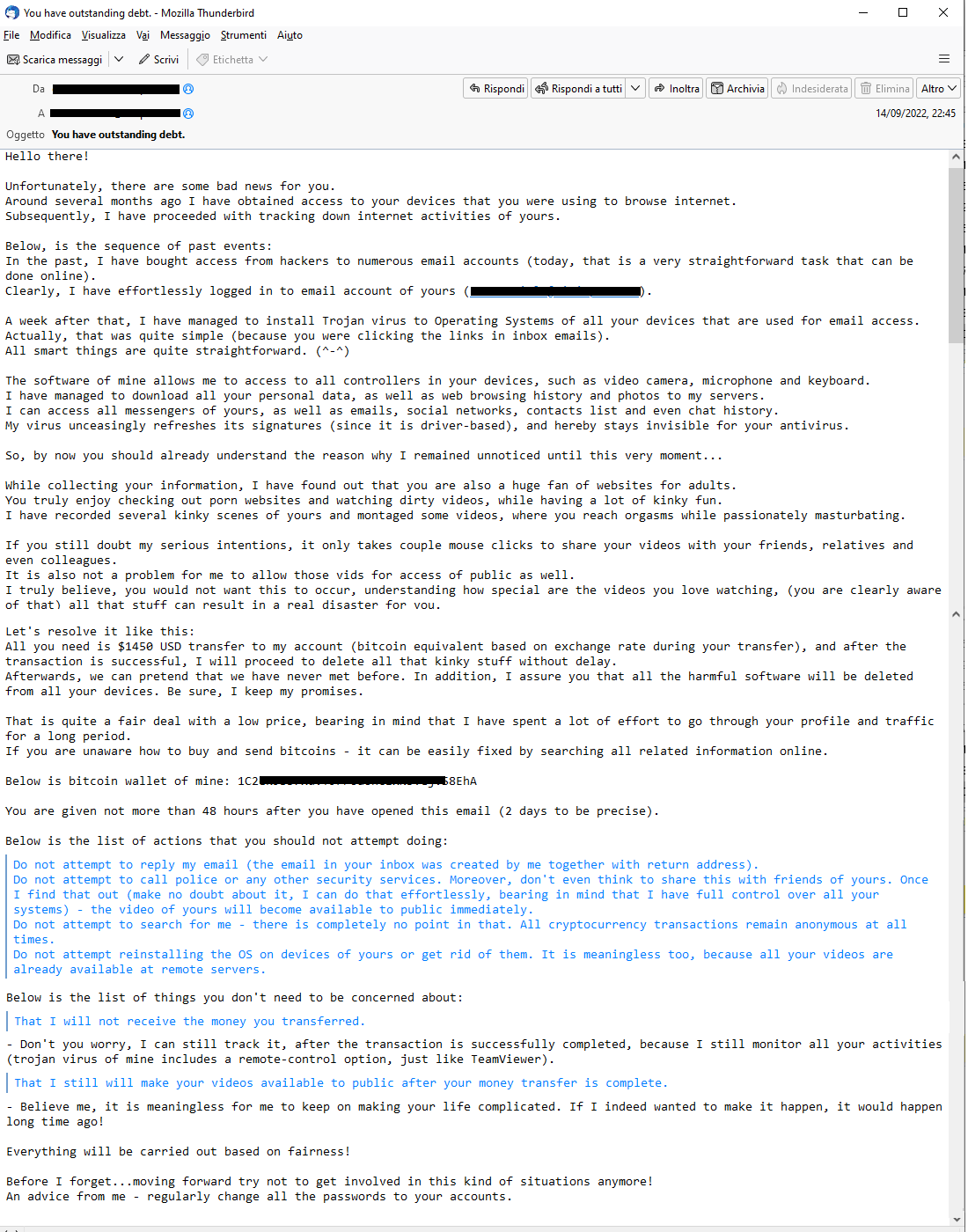 "Circa diversi mesi fa ho ottenuto l'accesso ai tuoi dispositivi che stavi utilizzando per navigare in Internet. Successivamente, ho provveduto a rintracciare le vostre attività su Internet. Di seguito, la sequenza degli eventi passati: In passato, ho acquistato l'accesso da hacker a numerosi account di posta elettronica (oggi è un'operazione molto semplice che può essere eseguita online). Chiaramente, ho effettuato l'accesso senza sforzo al tuo account di posta elettronica (****). Una settimana dopo, sono riuscito a installare il virus Trojan sui sistemi operativi di tutti i dispositivi utilizzati per l'accesso alla posta elettronica. In realtà, è stato abbastanza semplice (perché stavi facendo clic sui collegamenti nelle e-mail di posta in arrivo).... Il mio software mi permette di accedere a tutti i controller dei tuoi dispositivi, come videocamera, microfono e tastiera. Sono riuscito a scaricare tutti i tuoi dati personali, così come la cronologia di navigazione web e le foto sui miei server. Posso accedere a tutti i tuoi messaggi di posta, nonché a e-mail, social network, elenco contatti e persino cronologia chat.
"Circa diversi mesi fa ho ottenuto l'accesso ai tuoi dispositivi che stavi utilizzando per navigare in Internet. Successivamente, ho provveduto a rintracciare le vostre attività su Internet. Di seguito, la sequenza degli eventi passati: In passato, ho acquistato l'accesso da hacker a numerosi account di posta elettronica (oggi è un'operazione molto semplice che può essere eseguita online). Chiaramente, ho effettuato l'accesso senza sforzo al tuo account di posta elettronica (****). Una settimana dopo, sono riuscito a installare il virus Trojan sui sistemi operativi di tutti i dispositivi utilizzati per l'accesso alla posta elettronica. In realtà, è stato abbastanza semplice (perché stavi facendo clic sui collegamenti nelle e-mail di posta in arrivo).... Il mio software mi permette di accedere a tutti i controller dei tuoi dispositivi, come videocamera, microfono e tastiera. Sono riuscito a scaricare tutti i tuoi dati personali, così come la cronologia di navigazione web e le foto sui miei server. Posso accedere a tutti i tuoi messaggi di posta, nonché a e-mail, social network, elenco contatti e persino cronologia chat.
Durante la raccolta delle tue informazioni, ho scoperto che sei anche un grande fan dei siti Web per adulti... Ho registrato diverse tue scene perverse e montato alcuni video... Se dubiti ancora delle mie intenzioni serie, bastano pochi clic del mouse per condividere i tuoi video con i tuoi amici, parenti e persino colleghi.
A questo punto viene richiesto di inviare 1450 USD in Bitcoin sul portafoglio di seguito indicato: "1C2XXXXXXXXXXXXXXXXXXXXXX8EhA'. Dopo aver ricevuto la transazione tutti i dati veranno cancellati, altrimenti in caso contrario un video che ritrae l'utente, verrà mandato a tutti i colleghi, amici e parenti, il malcapitato ha 48 ore di tempo per effettuare il pagamento!
Analizzando i pagamenti effettuati sul wallet indicato dal cyber criminale alla data del 19/09/2022, vediamo che risultano esserci ben 3 transazioni per un totale di $ 4012,81.
In questi casi vi invitiamo a:
- non rispondere a questo genere di e-mail e a non aprire allegati o a cliccare righe contenenti link non sicuri, e certamente a NON inviare alcuna somma di denaro, si possono tranquillamente ignorare o eliminare.
- Nel caso in cui il criminale dovesse riportare una password effettiva utilizzata dall'utente -la tecnica è quella di sfruttare le password provenienti da Leak (furto di dati compromessi) pubblici di siti ufficiali avvenuti in passato (es. LinkedIn, Yahoo ecc.)- è consigliabile cambiarla e attivare l'autenticazione a due fattori su quel servizio.
13 Settembre 2022 ==> Smishing DM
Analizziamo di seguito un nuovo tentativo di smishing che si cela dietro un falso sms giunto da dm, la catena di negozi tedesca che vende in particolare cosmetici, articoli sanitari e prodotti per la casa.
Il messaggio, in ligua croata che riportiamo di lato, informa il malcapitato di una promozione, ossia dei regali riservati ai clienti della catena di negozi dm. Lo invita quindi a cliccare sul link proposto:
http://amendmenthop[.]cn/dmdm[-]qfla/tb[.]php?ix=dz1663049105022
In prima battuta notiamo che l'alert, contraddistinto dal layout conciso ed essenziale, contiene solo un link e un'immagine del logo di dm che potrebbe trarre in inganno.
Come possiamo vedere dall' immagine riportata di lato la pagina web in cui si viene dirottati dal link presente nell'sms di dm, è graficamente ben impostata, in quanto è stato inserito il logo di dm. Notiamo però che la pagina web è ospitata su un dominio anomalo:
ytzhtazhong[.]cn
Ai consumatori di dm viene richiesto di partecipare a un breve sondaggio per poter vincere un premio di 1000 Euro.
"Attraverso il questionario, avrai la possibilità di vincere 1000 Euro"
Le domande successive sono molto generiche.
|
Domanda 2
|
Domanda 3
|
Domanda 4
|
Al termine del questionario si verrà successivamente rimandati ad un'altra pagina web, dove viene richiesto di scegliere un pacco regalo....Dopo 3 tentativi finalmente riusciamo a completare il questionario e ad avvicinarci al premio di 1000 Euro!
Nell'immagine di lato vengono indicate LE REGOLE per ottenere il premio, tra le quali viene richiesto di:
- Informare della promozione 5 gruppi o 20 amici
- Inserire l'indirizzo e-mail e completare la registrazione
- I regali saranno consegnati entro 5-7 giorni
Per poter ottenere il proprio premio è necessario per prima cosa condividere il messaggio con 5 gruppi o 20 amici sulle app indicate nell'immagine, ossia
Whatsapp e
Messenger, in questo modo lo scopo del cybertuffatore è quello di diffondere la truffa ad altri conoscenti e ottenere più dati possibili.
In conclusione vi invitiamo sempre a diffidare da qualunque email che richieda l'inserimento di dati riservati, evitando di cliccare su link sospetti, i cui collegamenti potrebbero condurre ad un sito contaffatto difficilmente distinguibile dall'originale, mettendo i vostri dati più preziosi nelle mani di cyber-truffatori per usi di loro maggiore interesse e profitto.
13 Settembre 2022 ==> Phishing Account di posta
«OGGETTO: < Password Reset Confirmation >
Analizziamo di segutio il tentativo di phishing che ha l'obiettivo di rubare la casella di posta elettronica del malcapitato.
Il messaggio, in lingua inglese, informa il destinatario che che la password del suo account di posta è in scadenza. Per mantenere la password e non avere interruzioni nei servizi legati al suo account di posta, è necessario confermare la password, attraverso il seguente link:
Click To update
Analizzando la mail notiamo che il messaggio proviene da un indirizzo email che non sembra riconducibile a qualche gestore di posta elettronica <pass-sec(at)tech-center(dot)com>. Questo è decisamente anomalo e dovrebbe quantomai insospettirci.
Chi dovesse malauguratamente cliccare sul link Click To update verrà dirottato su una pagina WEB anomala, che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali....
05 Settembre 2022 ==> Phishing Aruba - Dominio scaduto
«OGGETTO: < Avviso Di Rinnovo >
Ecco un altro tentativo di phishing che giunge da una falsa comunicazione sempre da parte di Aruba.
II messaggio informa il ricevente che il suo dominio ospitato su Aruba scadrà il giorno 07/09/2022. Qualora il dominio non venga rinnovato entro tale data, questi e tutti i servizi associati, comprese le caselle di posta verranno disattivati. Invita quindi l'utente a rinnovare il dominio attraverso il seguente link:
RINNOVA IL DOMINIO
Chiaramente la nota azienda di servizi di web hosting, e-mail e registrazione domini, Aruba è estranea all'invio massivo di queste mail che sono delle vere e proprie truffe il cui obiettivo resta, come sempre, quello di rubare dati sensibili dell'ignaro ricevente.
Analizzando il testo del messaggio notiamo fin da subito che l'indirizzo e-mail del mittente <staff-aruba-rinnovo(at)info(dot)it> non proviene dal dominio ufficiale di Aruba.
Chi dovesse malauguratamente cliccare sul link RINNOVA IL DOMINIO verrà dirottato su una pagina WEB anomala, che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali.
05 Settembre 2022 ==> Phishing Aruba
«OGGETTO: <Re: Hai ricevuto un documento condiviso per ordine commerciale tramite Aruba.it >
Ecco che ritroviamo anche questo mese il seguente tentativo di phishing che giunge da una falsa comunicazione da parte di Aruba.
II messaggio informa il ricevente che è disponibile un nuovo documento condiviso tramite Aruba iCloud, proveniente da una certa: <<finevra(at)gstradesrl(dot)it>> Invita quindi l'utente a visualizzare il file PDF attraverso il seguente link:
Visualizza PDF in linea
Chiaramente la nota azienda di servizi di web hosting, e-mail e registrazione domini, Aruba è estranea all'invio massivo di queste mail che sono delle vere e proprie truffe il cui obiettivo resta, come sempre, quello di rubare dati sensibili dell'ignaro ricevente.
Analizzando il testo del messaggio notiamo fin da subito che l'indirizzo e-mail del mittente <gerd(dot)nielsen(at)mytng(dot)de> non proviene dal dominio ufficiale di Aruba.
Chi dovesse malauguratamente cliccare sul link Visualizza PDF in linea verrà dirottato su una pagina WEB anomala, che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali.
Un po' di attenzione e colpo d'occhio, possono far risparmiare parecchi fastidi e grattacapi...
Vi invitiamo a NON farvi ingannare da queste tipologie di e-mail che, anche se utilizzano tecniche di approccio già viste e non particolarmente sofisticate, se vi è una recrudescenza, con ragionevole probabilità, più di qualche malcapitato viene ingannato.
Vi invitiamo a consultare, per maggiori approfondimenti, le seguenti informativa sulle tecniche di Phishing:
04/08/2022 16:39 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di agosto 2022...
06/07/2022 12:39 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di luglio 2022...
06/06/2022 14:30 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di giungo 2022...
02/05/2022 11:06 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di maggio 2022...
06/04/2022 16:51 - Phishing: i tentativi di furto credenziali e/o dati maggiormente diffusi nel mese di aprile 2022...
08/03/2022 17:08 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di marzo 2022..
03/02/2022 16:25 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di febbraio 2022...
04/01/2022 09:13 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di gennaio 2022...
03/12/2021 15:57 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di dicembre 2021...
04/11/2021 09:33 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di novembre 2021...
07/10/2021 14:38 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di ottobre 2021...
10/09/2021 15:58 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di settembre 2021...
Prova Vir.IT eXplorer Lite
 Se non doveste ancora utilizzare Vir.IT eXplorer PRO è consigliabile installare, ad integrazione dell'antivirus in uso per aumentare la sicurezza dei vostri computer, PC e SERVER indifferentemente, Vir.IT eXplorer Lite -FREE Edition-.
Se non doveste ancora utilizzare Vir.IT eXplorer PRO è consigliabile installare, ad integrazione dell'antivirus in uso per aumentare la sicurezza dei vostri computer, PC e SERVER indifferentemente, Vir.IT eXplorer Lite -FREE Edition-.
Vir.IT eXplorer Lite ha le seguenti caratteristiche peculiari:
- liberamente utilizzabile sia in ambito privato sia in ambito aziendale con aggiornamenti Motore+Firme senza limitazioni temporali;
- interoperabile con eventuali altri AntiVirus, AntiSpyware, AntiMalware o Internet Security già presenti su PC e SERVER, consigliato l'utilizzo ad integrazione dell'AntiVirus già in uso poichè non conflitta nè rallenta il sistema ma permette di aumentare sensibilmente la sicurezza in termini di identificazione e bonifica dei file infetti;
- identifica e, in moltissimi casi, anche rimuove la maggior parte dei virus/malware realmente circolanti o, in alternativa, ne permette l'invio al C.R.A.M. Centro Ricerche Anti-Malware di TG Soft per l'analisi e l'aggiornamento di Vir.IT eXplorer per l'univoca identificazione e la corretta rimozione;
- grazie alla tecnologia Intrusione Detection, resa disponibile anche nella versione Lite di Vir.IT eXplorer, il software è in grado di segnalare eventuali virus/malware di nuova generazione che si siano posti in esecuzione automatica e procedere all'invio dei file segnalati al C.R.A.M. di TG Soft.
- Procedi al download di Vir.IT eXplorer Lite dalla pagina ufficiale di distribuzione del sito di TG Soft.
VirIT Mobile Security AntiMalware ITALIANO per TUTTI i dispositivi AndroidTM
VirIT Mobile Security software Anti-Malware Italiano che protegge smartphone e tablet Android™, da intrusioni di Malware ed altre minacce indesiderate, e che dà la possibilità all'utente di salvaguardare la propria privacy con un approccio euristico avanzato (Permission Analyzer).
 TG Soft rende disponibile gratuitamente VirIT Mobile Security accedendo al market di Google Play Store (https://play.google.com/store/apps/details?id=it.tgsoft.virit) dal quale è possibile prelevare la versione Lite, liberamente utilizzabile sia in ambito privato che aziendale.
TG Soft rende disponibile gratuitamente VirIT Mobile Security accedendo al market di Google Play Store (https://play.google.com/store/apps/details?id=it.tgsoft.virit) dal quale è possibile prelevare la versione Lite, liberamente utilizzabile sia in ambito privato che aziendale.
E’ possibile eseguire il passaggio alla versione PRO, acquistandolo direttamente dal nostro sito https://www.tgsoft.it/italy/ordine_step_1.asp
Ringraziamenti
Il Centro Ricerche Anti-Malware di TG Soft ringrazia tutti i gli utenti, i clienti, i tecnici dei rivenditori e tutte le persone che hanno trasmesso/segnalato al nostro Centro Ricerche materiale riconducibili ad attività di Phishing che ci hanno permesso di rendere il più completa possibile questa informativa.
Come inviare e-mail sospette per l'analisi come possibili phishing ma anche virus/malware o Crypto-Malware
L'invio di materiali da analizzare al Centro Ricerche Anti-Malware di TG Soft per l'analisi che è sempre e comunque gratuito può avvenire in tutta sicurezza in due modalità:
- qualsiasi e-mail che sia da considerarsi sospetta può essere inviata direttamente dalla posta elettronica del ricevente scegliendo come modalità di invio "INOLTRA come ALLEGATO" e inserendo nell'oggetto "Possibile Phishing da verificare" piuttosto che "Possibile Malware da verificare" alla mail lite@virit.com
- salvare come file esterno al programma di posta elettronica utilizzato la mail da inviare al C.R.A.M. di TG Soft per l'analisi. Il file che ne risulterà dovrà essere inviato facendone l'Upload dalla pagina di INVIO File Sospetti. Naturalmente per avere un feed-back rispetto al responso dell'analisi dei file infetti inviati sarà necessario indicare un indirizzo e-mail e sarà gradita una breve descrizione del motivo dell'invio del file (ad esempio: possiible/probabile phishing; possibile/probabile malware o altro).
 Per maggiori approfondimenti su come inoltrare in sicurezza e-mail sospette vi invitiamo a consultare la seguente pagina pubblica: Come inviare e-mail sospette per l'analisi
Per maggiori approfondimenti su come inoltrare in sicurezza e-mail sospette vi invitiamo a consultare la seguente pagina pubblica: Come inviare e-mail sospette per l'analisi
Tutto questo per aiutare ad aiutarvi cercando di evitare che possiate incappare in furti di credenziali, virus/malware o ancor peggio Ransomware / Crypto-Malware di nuova generazione.
C.R.A.M. Centro Ricerche Anti-Malware di TG Soft


 "Circa diversi mesi fa ho ottenuto l'accesso ai tuoi dispositivi che stavi utilizzando per navigare in Internet. Successivamente, ho provveduto a rintracciare le vostre attività su Internet. Di seguito, la sequenza degli eventi passati: In passato, ho acquistato l'accesso da hacker a numerosi account di posta elettronica (oggi è un'operazione molto semplice che può essere eseguita online). Chiaramente, ho effettuato l'accesso senza sforzo al tuo account di posta elettronica (****). Una settimana dopo, sono riuscito a installare il virus Trojan sui sistemi operativi di tutti i dispositivi utilizzati per l'accesso alla posta elettronica. In realtà, è stato abbastanza semplice (perché stavi facendo clic sui collegamenti nelle e-mail di posta in arrivo).... Il mio software mi permette di accedere a tutti i controller dei tuoi dispositivi, come videocamera, microfono e tastiera. Sono riuscito a scaricare tutti i tuoi dati personali, così come la cronologia di navigazione web e le foto sui miei server. Posso accedere a tutti i tuoi messaggi di posta, nonché a e-mail, social network, elenco contatti e persino cronologia chat.
"Circa diversi mesi fa ho ottenuto l'accesso ai tuoi dispositivi che stavi utilizzando per navigare in Internet. Successivamente, ho provveduto a rintracciare le vostre attività su Internet. Di seguito, la sequenza degli eventi passati: In passato, ho acquistato l'accesso da hacker a numerosi account di posta elettronica (oggi è un'operazione molto semplice che può essere eseguita online). Chiaramente, ho effettuato l'accesso senza sforzo al tuo account di posta elettronica (****). Una settimana dopo, sono riuscito a installare il virus Trojan sui sistemi operativi di tutti i dispositivi utilizzati per l'accesso alla posta elettronica. In realtà, è stato abbastanza semplice (perché stavi facendo clic sui collegamenti nelle e-mail di posta in arrivo).... Il mio software mi permette di accedere a tutti i controller dei tuoi dispositivi, come videocamera, microfono e tastiera. Sono riuscito a scaricare tutti i tuoi dati personali, così come la cronologia di navigazione web e le foto sui miei server. Posso accedere a tutti i tuoi messaggi di posta, nonché a e-mail, social network, elenco contatti e persino cronologia chat.  Se non doveste ancora utilizzare Vir.IT eXplorer PRO è consigliabile installare, ad integrazione dell'antivirus in uso per aumentare la sicurezza dei vostri computer, PC e SERVER indifferentemente, Vir.IT eXplorer Lite -FREE Edition-.
Se non doveste ancora utilizzare Vir.IT eXplorer PRO è consigliabile installare, ad integrazione dell'antivirus in uso per aumentare la sicurezza dei vostri computer, PC e SERVER indifferentemente, Vir.IT eXplorer Lite -FREE Edition-. TG Soft rende disponibile gratuitamente VirIT Mobile Security accedendo al market di Google Play Store (https://play.google.com/store/apps/details?id=it.tgsoft.virit) dal quale è possibile prelevare la versione Lite, liberamente utilizzabile sia in ambito privato che aziendale.
TG Soft rende disponibile gratuitamente VirIT Mobile Security accedendo al market di Google Play Store (https://play.google.com/store/apps/details?id=it.tgsoft.virit) dal quale è possibile prelevare la versione Lite, liberamente utilizzabile sia in ambito privato che aziendale. Per maggiori approfondimenti su come inoltrare in sicurezza e-mail sospette vi invitiamo a consultare la seguente pagina pubblica: Come inviare e-mail sospette per l'analisi
Per maggiori approfondimenti su come inoltrare in sicurezza e-mail sospette vi invitiamo a consultare la seguente pagina pubblica: Come inviare e-mail sospette per l'analisi