INDICE dei PHISHING
Di seguito riportiamo i tentativi di phishing a mezzo email più comuni, rilevati dal Centro Ricerche Anti-Malware di TG Soft nel mese di
gennaio 2024:
30/01/2024 =>
EuroPages
30/01/2024 =>
Mooney
27/01/2024 =>
BRT
25/01/2024 =>
Istituto Bancario
24/01/2024 =>
Aruba - Fattura scaduta
18/01/2024 =>
Smishing UniCredit
17/01/2024 =>
Smishing Istituto di Credito
13/01/2023 =>
Account Posta Elettronica
11/01/2024 =>
Account di Posta Elettronica
10/01/2024 =>
Trenitalia
09/01/2024 =>
Aruba - fattura non pagata
09/01/2024 =>
Account Posta Elettronica
08/01/2024 =>
MetaMask
09/01/2024 =>
Mooney
07/01/2024 =>
Mooney
01/01/2024 =>
Aruba - fattura non pagata
Queste email hanno lo scopo di ingannare qualche malcapitato inducendolo a fornire dati sensibili, come le informazioni del conto corrente, i codici della carta di credito o credenziali di accesso personali, con tutte le possibili conseguenze facilmente immaginabili.
30 Gennaio 2024 ==> Phishing EuroPages
«OGGETTO: <Leonardo Rossi ti ha inviato un messaggio di richiesta riguardante il tuo prodotto>
Ritroviamo questo mese il seguente tentativo di phishing che sembra provenire da una falsa comunicazione di
EuroPages e che ha l'obiettivo di rubare le credenziali di accesso all'account del malcapitato.
Il messaggio sembra provenire da
EuroPages,
la più grande piattaforma di sourcing B2B internazionale, e notifica all'utente che è arrivato un messaggio relativo al suo prodotto elencato su EuroPages da parte di un certo "
Leonardo Rossi". Quindi invita l'utente ad accedere al suo account per visualizzare il messaggio di richiesta, attraverso il seguente link:
ACCEDI AL MIO ACCOUNT
Analizzando la mail notiamo che il messaggio proviene da un indirizzo email che non sembra riconducibile al dominio ufficiale di
EuroPages <maisano(at)gruppocracco(dot)com>. Questo è decisamente anomalo e dovrebbe quantomai insospettirci.
Chi dovesse malauguratamente cliccare sul link
ACCEDI AL MIO ACCOUNT verrà dirottato su una pagina WEB anomala, che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali...
30 Gennaio 2024 ==> Phishing Mooney
OGGETTO: <
Nuovo aggiornamento >
Di seguito analizziamo il seguente tentativo di phishing che giunge da una falsa comunicazione da parte di
Mooney, la società italiana di Proximity Banking & Payments
.
II messaggio informa il ricevente che è necessario procedere all'aggiornamento delle proprie informazioni.
Lo invita quindi ad effettuare l'aggiornamento del suo profilo, seguendo i passaggi di sicurezza indicati attraverso il seguente link:
Aggiornamenti
Questa volta la campagna di phishing simula una comunicazione che sembra provenire dalla società italiana di pagamenti online
Mooney,
che chiaramente è estranea all'invio massivo di queste mail che sono delle vere e proprie truffe il cui obiettivo resta, come sempre, quello di rubare dati sensibili dell'ignaro ricevente.
Analizzando il testo del messaggio notiamo sin da subito che il messaggio di alert giunge da un indirizzo e-mail che potrebbe trarre in inganno, ma non è riconducibile al dominio di
Mooney <noreply32425(at)mooney(dot)it>, anche se il cybercriminale ha avuto l'accortezza di inserire il logo della società, prestiamo sempre la massima attenzione prima di cliccare su link sospetti.
Chi dovesse malauguratamente cliccare sul link
Aggiornamenti verrà dirottato su una pagina WEB anomala, che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali...
27 Gennaio 2024 ==> Phishing BRT
«OGGETTO: < Il tuo pacco non può essere consegnato 63AUIT66001 >
Di seguito un nuovo tentativo di phishing, che si cela dietro a una falsa comunicazione giunta apparentemente dal servizio di
BRT, relativamente alla consegna di un presunto pacco.
II messaggio segnala all'ignaro ricevente che la sua spedizione è in sospeso a causa di spese doganali aggiuntive non ancora saldate. Gli comunica quindi che per ricevere il suo pacco deve saldare le spese doganali pari a Euro 2,28. Questi messaggi vengono sempre più utilizzati per perpetrare la truffa ai danni dei consumatori che utlizzano sempre più l'e-commerce per i propri acquisti.
Per completare il pagamento viene indicato il seguente link:
Conferma il pagamento
La mail di alert giunge da un indirizzo email che non ha nulla a che vedere con il dominio di BRT <iubenda(at)magmalab(dot)eu>, questo è decisamente anomalo e dovrebbe quantomai insospettirci.
Chi dovesse cliccare sul link verrà rimandato su una pagina WEB anomala, che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali..
25 Gennaio 2024 ==> Phishing Istituto Bancario
OGGETTO: <
Importante >
Analizziamo di seguito un altro tentativo di phishing, che giunge attraverso un'e-mail che, sfruttando la notorietà di un noto Istituto Bancario nazionale
, cerca di spacciarsi per una comunicazione ufficiale, per indurre l'ignaro ricevente ad effettuare quanto richiesto e a cadere in questo tranello basato su tecniche di ingegneria sociale (social engeenering).
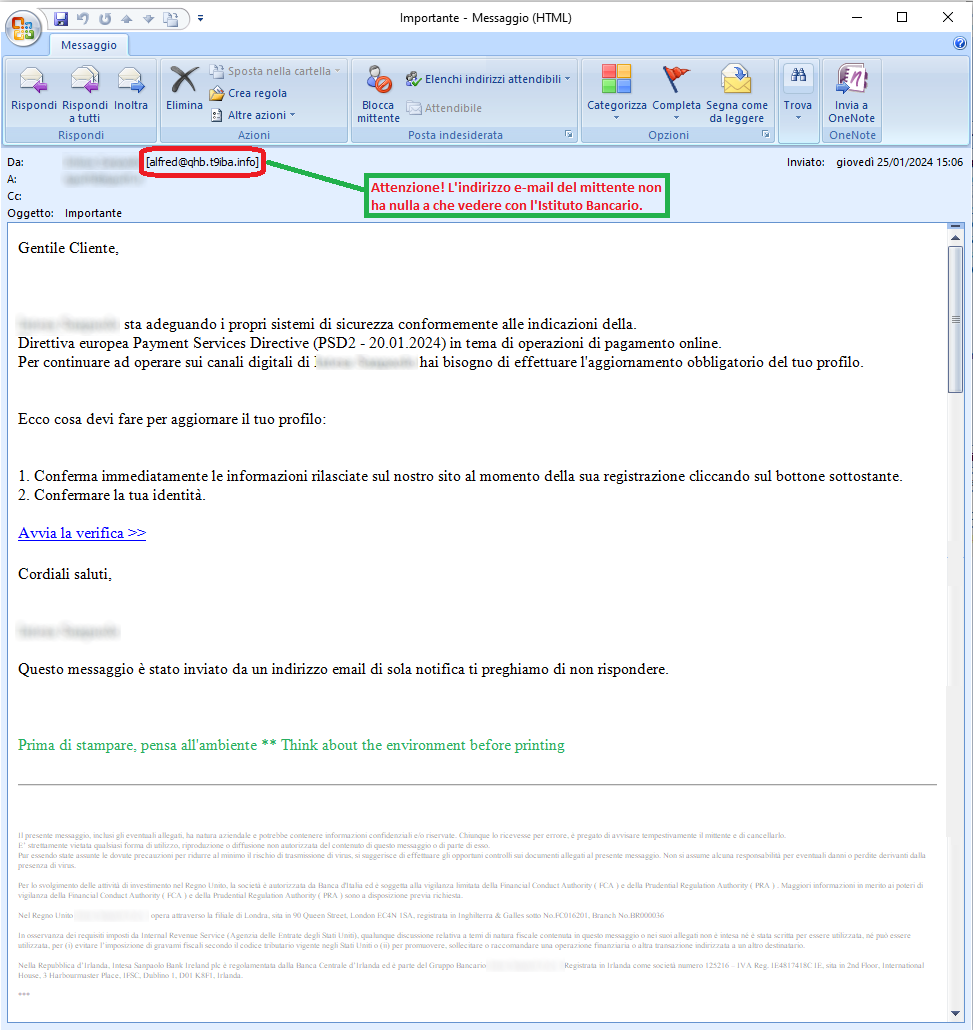
Il messaggio segnala all'ignaro ricevente che a causa di una procedura di adeguamento dei propri sistemi di sicurezza per essere in conformità con la Direttiva Europea in tema di operazioni di pagamento online, per continuare ad operare sui canali bancari è necessario aggiornare il proprio profilo.
Per procedere all'aggiornamento del profilo viene richiesto di confermare le informazioni personali rilasciate sul sito dell'Istituto Bancario al momento della registrazione e di confermare la propria identità, attraverso il seguente link:
Avvia la verifica >>
Possiamo notare sin da subito che il messaggio di alert giunge da un indirizzo e-mail <
alfred(at)qhb(dot)t9iba(dot)info> quanto mai sospetto
. Inoltre il testo è estremamente
scarno e generico, cosa che NON contraddistingue le comunicazioni ufficiali di questo tipo.
L'intento è quello di portare il malcapitato a cliccare sul link per continuare ad usare il proprio account, e sfrutta l'urgenza della comunicazione per far si che il destinatario clicchi.
Chi dovesse malauguratamente cliccare sul link verrà dirottato su una pagina WEB anomala, che non ha nulla a che vedere con il sito ufficiale del noto Istituto Bancario, ma che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali.
24 Gennaio 2024 ==> Phishing Aruba - Fattura scaduta
OGGETTO: <
Aruba.it - Avviso di Fattura Scaduta 24/01/2024>
Continuano i tentativi di phishing che si spacciano per comunicazioni da parte del brand
Aruba.
Il messaggio informa il ricevente che il suo dominio ospitato su
Aruba collegato al suo account di posta elettronica scadrà il giorno 24/01/2024. Lo informa quindi che qyualoria il dominio non verrà rinnovato, questo e tutti i servizi a questo associati, comprese le caselle di posta elettronica, verranno disattivate non potrà più quindi ricevere e inviare messaggi.
Invita quindi l'utente a effettuare il login per rinnovare i servizi, attraverso il seguente link:
RINNOVA IL DOMINIO
Chiaramente la nota azienda di servizi di web hosting, e-mail e registrazione domini, Aruba è estranea all'invio massivo di queste mail che sono delle vere e proprie truffe il cui obiettivo resta, come sempre, quello di rubare dati sensibili dell'ignaro ricevente.
Analizzando il testo del messaggio notiamo fin da subito che l'indirizzo e-mail del mittente proviene da un generico <
Assistenza Clienti> utilizzata come etichetta per nascondere il vero mittente, che chiaramente non ha nulla a che vedere con il dominio ufficiale di
Aruba, questo è decisamente anomalo e dovrebbe quantomai insospettirci. Possiamo notare però che il cyber criminale ha avuto l'accortezza di inserire il noto logo di
Aruba per rendere il messaggio più attendibile.
Chi dovesse malauguratamente cliccare sul link
RINNOVA IL DOMINIO verrà dirottato su una pagina WEB anomala che non ha nulla a che vedere con il sito ufficiale di
Aruba, ma che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali..
18 Gennaio 2024 ==> Smishing UniCredit
Analizziamo di seguito un nuovo tentativo di smishing volto ad ottenere dati sensibili attraverso l'invio di un sms fraudolento.

Il messaggio, che sembra giungere da UniCredit, segnala all'ignaro ricevente che vi è una richiesta di pagamento di Euro 221,45 e invita alla verifica della transazione cliccando sul link proposto.
Attraverso la falsa rilevazione di un'operazione sospetta, i malfattori inducono l'utente ad accedere tempestivamente all'home banking per la verifica rubandone quindi le credenziali.
E' chiaro che per chi non sia cliente di UniCredit sia più intuitivo comprendere che si tratti di una vera e propria truffa. Tuttavia anche per chi fosse cliente dell'istituto stesso non è difficile intuire che si è in presenza di un vero e proprio tetativo di frode informatica.
Già a vista d'occhio il link malevole presente sul sms sembra anomalo e sicuramente non riconducibile al sito ufficiale di UniCredit.
Ricordiamo altresì che i canali di comunicazione di cui si avvalgono i vari istituti finanziari per segnalare eventuali accessi anomali sono ben diversi dall'invio di un sms di alert al malcapitato.
Chi dovesse malauguratamente cliccare sul link verrà dirottato su una pagina WEB anomala, che non ha nulla a che vedere con il sito ufficiale di Unicredit, ma che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali..
17 Gennaio 2024 ==> Smishing Istituto di Credito
Analizziamo di seguito due tentativi di smishing, che si celano dietro a falsi sms giunti, sfruttando il noto nome di un Istituto Bancario nazionale
, e che cerca di spacciarsi per una comunicazione ufficiale, per indurre l'ignaro ricevente ad effettuare quanto richiesto e a cadere in questo tranello basato su tecniche di ingegneria sociale (social engeenering).
Nei messaggi che riportiamo in alto, viene segnalato all'ignaro ricevente che è stata richiesta una spesa dal suo conto corrente per Euro 1750,00.
Lo invita quindi a fare una segnalazione nel caso non sia stato lui a richiederLa, attraverso il link proposto. Notiamo che i messaggi sono simili, quello che cambia è il sito di atterraggio, che riporta a due indirizzi url diversi:
"
https://grupo***[.]com" e "
https://um****nt[.]com"
E' logico che se il destinatario dell'sms non sia cliente del noto Istituto bancario sia più intuitivo chiedersi cosa si celi effettivamente dietro questo sms anomalo. Nel caso specifico analizzato tuttavia il destinatario risulta effettivamente cliente dell'Istituto bancario tanto che il messaggio giunge nella chat dove vengono recapitati i codici per autorizzare i pagamenti effettuati con la carta di credito associata. A maggior ragione è fondamentale saper riconoscere questi, ormai diffusi, tentativi di frode informatica. E' importante ricordare soprattutto che in nessun caso gli istituti bancari/circuiti di pagamento richiedono ai clienti di fornire i dati della propria carta di pagamento attraverso e-mail, sms o call center.
Tornando all'esempio riportato, possiamo notare in primis che l'sms ricevuto è molto generico.. si rivolge infatti ad un ''
Gentile cliente''' senza riportare di fatto alcun dato identificativo del titolare del conto oggetto dell'alert, cosa che dovrebbe già insospettire. E' chiaro che l'intento dei cyber-criminali è di portare l'utente a cliccare tempestivamente sul link per bloccare il pagamento non autorizzato.
Come possiamo vedere dall' immagine riportata, la pagina web in cui si viene dirottati è davvero ben fatta in quanto simula quel del sito ufficiale dell'Istituto bancario, risultando ragionevolmente ingannevole, sia dal punto di vista grafico che testuale.
Per rassicurare l'utente sull'autenticità della pagina i cyber-criminali hanno avuto infatti l'accorgimento di inserire il logo autentico e di impostare la pagina con la stessa grafica del sito ufficiale.
La pagina di accesso alla gestione dell'account però è ospitata su un indirizzo/dominio anomalo che non è riconducibile al dominio ufficiale dell'Istituto bancario e che riportiamo di seguito:
"
https://grupo***[.]com"
o
"
https://um****nt[.]com"
Entrambi i link riportano ad una pagina web, ospitata su due diversi domini ma che graficamente sono uguali.
Inserendo i dati di accesso su questo FORM per effettuare l'accesso al conto corrente, quest'ultimi verranno inviati su un server remoto e utilizzati da cyber-truffatori con tutti i rischi annessi e connessi facilmente immaginabili.
11 Gennaio 2024 ==> Phishing Account Posta Elettronica
OGGETTO: <
New document from ***** Office admin>
Analizziamo di seguito il tentativo di phishing che ha l'obiettivo di rubare le credenziali dell'account di posta elettronica del malcapitato.
Il messaggio, in lingua inglese, informa il destinatario di un nuovo documento condiviso che sembra inviato dall'amministratore dell'account di posta. Invita quindi il malcapitato a visualizzare il documento in .pdf, scaricandolo al seguente link:
DOWNLOAD PDF
Analizzando la mail notiamo che il messaggio proviene da un indirizzo email che non sembra riconducibile al server che ospita la casella di posta elettronica <
kunze(at)thientranlong123(dot)shop>. Questo è decisamente anomalo e dovrebbe quantomai insospettirci.
Chi dovesse malauguratamente cliccare sul link
DOWNLOAD PDF verrà dirottato su una pagina WEB anomala, che come si può vedere dall'immagine di lato non ha nulla a che fare con il gestore dell'account di Posta elettronica.
La pagina su cui si viene rimandati, per l'inserimento delle proprie credenziali dell'account di posta, è ospitata su un indirizzo/dominio anomalo
, che riportiamo di seguito:
https[:]//bafkreigsy7grro3oyncupnjsllqqz5n5twhe4up5n4pikouddrrab35c2i[.]ipfs....
Vi invitiamo sempre a far attenzione e a non inserire i vostri dati personali e/o password su form ospitati su pagine web contraffatte, in quanto verranno inviati su un server remoto e utilizzati da cyber-truffatori con tutti i rischi annessi e connessi facilmente immaginabili.
10 Gennaio 2024 ==> Phishing Trenitalia
Di seguito analizziamo il seguente tentativo di truffa che si cela dietro ad una falsa comunicazione che sfrutta la nota azienda
Trenitalia.
Si tratta nello specifico di un messaggio promozionale che allude ad una ''
Promozione di Capodanno'' che permetterebbe solo a pochi fortunati di viaggiare gratis...o per lo meno così sembrerebbe.
Sicuramente per molti utenti inesperti dietro questo phishing si cela un vero e proprio specchietto per le allodole.
D'altronde si sono appena concluse le festività natalizie e c'è chi pensa già a programmare le prossime vacanze.. una cartafreccia
Trenitalia per poter viaggiare gratis fa davvero gola!
Chiaramente
Trenitalia è estranea all'invio massivo di queste campagne malevole che sono delle vere e proprie truffe il cui obiettivo resta, come sempre, quello di rubare dati sensibili dell'ignaro ricevente.
A scanso di equivoci si tratta infatti di un tentativo di phishing volto a carpire i vostri dati personali..
Quindi occhi aperti... per evitare spiacevoli inconvenienti basta un pò di attenzione e colpo d'occhio.
Innanzitutto la pagina di ''atterraggio'' dove si viene dirottati cliccando sul link ricevuto, sebbene graficamente ben fatta (con immagini fuorvianti e il logo autentico di
Trenitalia) non sembra per nulla attendibile.
Il sondaggio per ottenere il premio è ospitato infatti su un indirizzo/dominio anomalo...
Si tratta della seguente pagina web:
"https[:]//wpclick[.]cc/....''
che non ha alcun legame con
Trenitalia.
I Cyber-criminali ideatori della truffa, per raggiungere il loro scopo, attraverso vari stratagemmi cercano di indurre l'utente a concludere velocemente il sondaggio facendogli credere che vi sono solo pochi fortunati e che i regali si stanno per esaurire.
Per dare maggior credibilità sono stati riportati altresì numerosi commenti di clienti che sembrerebbero aver già partecipato al sondaggio. Sono tutte testimonianze/feedback rassicuranti sulla consegna effettiva della vincita e sul fatto che non si tratti realmente di una truffa....
Di certo se così tanti utenti sono stati fortunati perchè non tentare la fortuna compilando un semplice sondaggio?!
Eccoci quindi al termine del sondaggio.
Le risposte sembrano essere state inviate e salvate con successo. Ora sembrebbe necessario solo dilettarsi in un semplice giochino per tentare la fortuna: abbiamo 3 tentativi per riuscire a scovare la cartafreccia omaggio all'interno di alcuni pacchi regalo...
Ma che fortunelli che siamo..
Dopo 2 tentativi ce l'abbiamo fatta: siamo riusciti ad ottenere la carta regalo Trenitalia per 1 anno di viaggi gratuiti..
Peccato che non sia ancora finita qui.. vengono fornite nuove istruzioni per finalizzare la vincita..
Ecco la sorpresa: come evidenziato nell'immagine la vincita è condizionata dalla condivisione della promozione a più gruppi e contatti su WhatsApp... una volta completata la barra di avanzamento si potrà inserire il proprio indirizzo di consegna e completare la registrazione.
Quindi non solo un tentativo di furto dei nostri dati sensibili ma pure una sorta di catena di Sant'Antonio!!
Lo scopo in questo caso è quello di diffondere questo tentativo di truffa a più contatti possibili..in questo modo siamo noi stessi a diventare "
complici" del cybercriminale difondendo la "
promozione" ai nostri contatti.
In conclusione vi invitiamo sempre a diffidare da qualunque messaggio che richieda l'inserimento di dati riservati, anche se in palio c'è la vincita di premi o buoni sconto, evitando di cliccare su link sospetti, i cui collegamenti potrebbero condurre ad un sito contaffatto difficilmente distinguibile dall'originale, mettendo i vostri dati più preziosi nelle mani di cyber-truffatori per usi di loro maggiore interesse e profitto.
09 Gennaio 2024 ==> Phishing Aruba - Fattura non pagata
OGGETTO: <
Fattura non pagata 09/01/2024>
Continuano anche questo mese i tentativi di phishing che si spacciano per comunicazioni da parte del brand
Aruba.
Il messaggio informa il ricevente che il suo dominio ospitato su
Aruba collegato al suo account di posta elettronica scadrà il giorno 09/01/2024. Lo informa quindi che dovrà rinnovare manualmente i suoi servizi per evitare la cancellazione dell'account e quindi la disattivazione di tutti servizi a questo associati, comprese le caselle di posta elettronica, non potrà più quindi ricevere e inviare messaggi.
Invita quindi l'utente a effettuare il login per rinnovare i servizi, attraverso il seguente link:
RINNOVA IL
Chiaramente la nota azienda di servizi di web hosting, e-mail e registrazione domini, Aruba è estranea all'invio massivo di queste mail che sono delle vere e proprie truffe il cui obiettivo resta, come sempre, quello di rubare dati sensibili dell'ignaro ricevente.
Analizzando il testo del messaggio notiamo fin da subito che l'indirizzo e-mail del mittente <postmaster(at)combellbe(dot)com> non proviene dal dominio ufficiale di
Aruba.
Per indurre il malcapitato a procedere tempestivamente al rinnovo della propria casella postale viene indicata la scadenza del 09/01/2024 che, guarda caso, coincide con la data di ricezione della mail.. quindi sembra non ci sia poi molto tempo a disposizione per effettuare il rinnovo ed impedire la disattivazione dei servizi. La tecnica di indicare un termine entro il quale poter concludere la procedura ha, senza dubbio, lo scopo di intimare l'utente, spinto dal timore di ritrovarsi con la sua casella e-mail disattivata, ad agire immediatamente e senza pensarci troppo.
Chi dovesse malauguratamente cliccare sul link
RINNOVA IL verrà dirottato sulla pagina visualizzata.
Come possiamo notare, innazitutto, la pagina di atterraggio, contrariamente a quanto dovremmo attenderci, non rimanda al form di accesso per effettuare il login all'AREA RISERVATA di
Aruba ma ospita un modulo di pagamento online che sembra appoggiarsi al circuito di
BancaSella e dove viene richiesto direttamente l'inserimento dei dati della carta di credito per finalizzare il pagamento della modica cifra di Euro 5,42.....
Sebbene la fretta e il timore di ritrovarsi con la casella email sospesa possano spingere l'utente a concludere velocemente l'operazione basta soffermarsi sull'indirizzo url riportato sulla barra del broswer per rendersi conto che il form di pagamento non risiede sul dominio ufficiale di
Aruba e nemmeno di
BancaSella:
https[:]//fattura[.]site[.]ku5li1KgGYy6BBCpppr8f12PMka1pJlLzMOEx.....
Vi invitiamo pertanto a ricordare che la fretta non è mai una buona consigliera e che, in presenza di questi tentativi di frodi informatiche, è necessario prestare attenzione ad ogni dettaglio, anche banale.
Procedendo all'inserimento dei dati richiesti, nello specifico i dati della carta di credito
, questi saranno recapitati ai cyber-criminali ideatori della truffa che li utilizzeranno a scopi criminali.
13 - 09 Gennaio 2024 ==> Phishing Account Posta Elettronica
Di seguito analizziamo i seguenti tentativi di phishing che hanno l'obiettivo di rubare le credenziali dell'account di posta elettronica del malcapitato.
ESEMPIO 1
< Your account ***** password expire today >
ESEMPIO 2
«Removal of **** from *****»
Negli esempi riportati in alto, in lingua inglese, viene segnalato al cliente che è necessario procedere ad aggiornare il proprio account di posta elettronica. Nel primo esempio il malfattore comunica che la password è in scadenza e che deve procedere entro 3 ore a confermare di voler mantenere la stessa password altrimenti ne verrà generata una nuova dal sistema. Nel secondo esempio invece il messaggio, informa il destinatario che al fine di liberare spazio nel loro database si sta procedendo all'eliminazione degli account inattivi. Pertanto se non dovessero ricevere riscontro alla presente comunicazione entro 7 giorni l'account verrà eliminato.
In entrambi i casi l'intento è quello di portare l'utente a cliccare sul link riportato nella mail, imponendo anche un limite temporale per far leva sull'urgenza del messaggio:
Keep Current Password o Confirm *****
Per riconoscere questi tentativi di phishing è necessario innanzittutto analizzare l'indirizzo e-mail del mittente, che come possiamo vedere nei 2 casi riportati:
<contact(at)polyflor(dot)co(dot)nz>; <
dierenselaan(at)readshop(dot)nl> sicuramente non provengono dal server che ospita la casella di posta elettronica.
Molto spesso questi messaggi sono e-mail scritte male che contengono errori di ortografia oppure richieste di rinnovo per servizi che non sono in scadenza, in quanto fanno leva sull'urgenza o sulla sicurezza dei propri dati per far si che l'utente proceda a inserire i propri dati.
Un altro elemento da analizzare sono i link o allegati che questi messaggi contengono, che di solito rimandano ad un sito web contraffatto dove viene richiesto l'inserimento dei propri dati personali come nome utente e password del proprio account o dati personali come la carta di credito per effettuare il rinnovo dell'account
e che, se inseriti, verrebbero utilizzati da
cyber-criminali per scopi criminali..
08 Gennaio 2024 ==> Phishing MetaMask
«OGGETTO: <Immediate Action Required: Enable 2FA for Account Safety>
Analizziamo di seguito un nuovo tentativo di phishing che ha l'obiettivo di rubare le credenziali di accesso al wallet "portafoglio" di criptovalute del malcapitato, di
MetaMask, società con sede a San Francisco.
MetaMask è un portafoglio software di criptovaluta utilizzato per interagire con la blockchain di Ethereum. Consente agli utenti di accedere al proprio portafoglio Ethereum tramite un'estensione del browser o un'app mobile.
Il messaggio, in lingua inglese, che analizziamo di seguito, informa il destinatario che per aumentare il livello di sicurezza viene richiesto a tutti gli utenti di
MetaMask di attivare il controllo a due fattori (
2FA). Per procedere deve cliccare sul seguente link:
Activate 2FA
Analizzando la mail notiamo che il messaggio proviene da un indirizzo e-mail quanto mai sospetto, che non sembra riconducibile al dominio ufficiale di
MetaMask <
tls6(at)ccb18089e0(dot)nxcli(dot)io>. Questo è decisamente anomalo e dovrebbe quantomai insospettirci.
Chi dovesse malauguratamente cliccare sul link
Activate 2FA verrà dirottato su una pagina WEB anomala, che non ha nulla a che vedere con il sito ufficiale di
MetaMask dove viene richiesto di continuare se si desidera procedere con l'autenticazione a 2 fattori.
La pagina su cui si viene rimandati potrebbe tarrre in inganno in quanto il cyber criminale ha avuto l'accortezza di inserire il logo di
MetaMask, notiamo tuttavia che è però ospitata su un indirizzo/dominio anomalo
, che riportiamo di seguito:
https[:]//activate-2fa[.]io/welcome
Vi invitiamo sempre a far attenzione e a non inserire i vostri dati personali e/o password su form ospitati su pagine web contraffatte, in quanto verranno inviati su un server remoto e utilizzati da cyber-truffatori con tutti i rischi annessi e connessi facilmente immaginabili.
09 - 07 Gennaio 2024 ==> Phishing Mooney
Di seguito analizziamo i seguenti tentativi di phishing che giungono da una falsa comunicazione da parte di
Mooney, la società italiana di Proximity Banking & Payments
.
ESEMPIO 1
< Messaggio importante
ESEMPIO 2
«[Notifica] Area Clienti !»
Negli esempi riportati in alto, viene segnalato al cliente che per ragioni di sicurezza deve procedere ad aggiornare il suo account
Mooney altrimenti non potrà più utilizzare la sua carta o il suo account verrà temporaneamente bloccato fino a quando non procede all'aggiornamento.
L'intento è chiaramente quello di portare l'utente a cliccare sul link riportato nella mail:
Clicca qui per attivare o Accedi
Questa volta la campagna di phishing simula una comunicazione che sembra provenire dalla società italiana di pagamenti online
Mooney,
che chiaramente è estranea all'invio massivo di queste mail che sono delle vere e proprie truffe il cui obiettivo resta, come sempre, quello di rubare dati sensibili dell'ignaro ricevente.
Per riconoscere questi tentativi di phishing è necessario innanzittutto analizzare l'indirizzo e-mail del mittente, che come possiamo vedere nei 2 casi riportati:
<communications(at)venture(dot)org(dot)nz>; <noreply(at)softpointcloud(dot)com> sicuramente non provengono dal dominio ufficiale di
Mooney.
Molto spesso questi messaggi sono e-mail scritte male che contengono errori di ortografia oppure richieste di rinnovo per servizi che non sono in scadenza, in quanto fanno leva sull'urgenza o sulla sicurezza dei propri dati per far si che l'utente proceda a inserire i propri dati.
Un altro elemento da analizzare sono i link o allegati che questi messaggi contengono, che di solito rimandano ad un sito web contraffatto dove viene richiesto l'inserimento dei propri dati personali come nome utente e password del proprio account o dati personali come la carta di credito per effettuare il rinnovo dell'account
e che, se inseriti, verrebbero utilizzati da
cyber-criminali per scopi criminali..
01 Gennaio 2024 ==> Phishing Aruba - Fattura non pagata
OGGETTO: <
Fattura non pagata 01/01/2024 .>
Ritroviamo anche nel nuovo anno i tentativi di phishing che si spacciano per comunicazioni da parte del brand
Aruba.
Il messaggio informa il ricevente che il suo dominio ospitato su
Aruba collegato al suo account di posta elettronica scadrà il giorno 01/01/2024. Lo informa quindi che dovrà rinnovare manualmente i suoi servizi per evitare la cancellazione dell'account e quindi la disattivazione di tutti servizi a questo associati, comprese le caselle di posta elettronica, non potrà più quindi ricevere e inviare messaggi.
Invita quindi l'utente a effettuare il login per rinnovare i servizi, attraverso il seguente link:
RINNOVA IL DOMINIO
Chiaramente la nota azienda di servizi di web hosting, e-mail e registrazione domini, Aruba è estranea all'invio massivo di queste mail che sono delle vere e proprie truffe il cui obiettivo resta, come sempre, quello di rubare dati sensibili dell'ignaro ricevente.
Analizzando il testo del messaggio notiamo fin da subito che l'indirizzo e-mail del mittente non proviene dal dominio ufficiale di
Aruba, <aruba(dot)restaurantcastello(dot)ru>, questo è decisamente anomalo e dovrebbe quantomai insospettirci. Possiamo notare però che il cyber criminale ha avuto l'accrotezza di inserire il noto logo d
i Aruba per rendere il messaggio più attendibile.
Chi dovesse malauguratamente cliccare sul link
RINNOVA IL DOMINIO verrà dirottato su una pagina WEB anomala che non ha nulla a che vedere con il sito ufficiale di
Aruba, ma che è già stata segnalata come pagina /SITO INGANNEVOLE.... in quanto gestito da cyber-criminali il cui obiettivo è quello di entrare in possesso dei vostri dati più preziosi per poterli utilizzare a scopi criminali..
Un po' di attenzione e colpo d'occhio, possono far risparmiare parecchi fastidi e grattacapi...
Vi invitiamo a NON farvi ingannare da queste tipologie di e-mail che, anche se utilizzano tecniche di approccio già viste e non particolarmente sofisticate, se vi è una recrudescenza, con ragionevole probabilità, più di qualche malcapitato viene ingannato.
Vi invitiamo a consultare, per maggiori approfondimenti, le seguenti informativa sulle tecniche di Phishing:
11/12/2023 09:39 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di dicembre 2023...
03/11/2023 08:58 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di novembre 2023...
03/10/2023 16:35
- Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di ottobre 2023...
05/09/2023 10:35 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di settembre 2023...
01/08/2023 17:33
- Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di agosto 2023...
03/07/2023 10:23
- Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di luglio 2023...
07/06/2023 15:57
- Phishing: i tentativi di furto credenziali e/o dati maggiormente diffusi nel mese di giugno 2023...
03/05/2023 17:59
- Phishing: i tentativi di furto credenziali e/o dati maggiormente diffusi nel mese di maggio 2023...
05/04/2023 17:34 - Phishing: i tentativi di furto credenziali e/o dati maggiormente diffusi nel mese di aprile 2023...
03/03/2023 16:54 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di marzo 2023..
06/02/2023 17:29 - Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di febbraio 2023...
02/01/2023 15:28
- Phishing: i tentativi di furto delle credenziali maggiormente diffuse nel mese di gennaio 2023...
Prova Vir.IT eXplorer Lite
 Se non doveste ancora utilizzare Vir.IT eXplorer PRO è consigliabile installare, ad integrazione dell'antivirus in uso per aumentare la sicurezza dei vostri computer, PC e SERVER indifferentemente, Vir.IT eXplorer Lite -FREE Edition-.
Se non doveste ancora utilizzare Vir.IT eXplorer PRO è consigliabile installare, ad integrazione dell'antivirus in uso per aumentare la sicurezza dei vostri computer, PC e SERVER indifferentemente, Vir.IT eXplorer Lite -FREE Edition-.
Vir.IT eXplorer Lite ha le seguenti caratteristiche peculiari:
- liberamente utilizzabile sia in ambito privato sia in ambito aziendale con aggiornamenti Motore+Firme senza limitazioni temporali;
- completamente interoperabile con altri software AntiVirus e/o prodotti per l'Internet Security (sia gratuiti che commerciali) già installati sul proprio computer, senza doverli disinstallare e senza provocare rallentamenti, poichè sono state opportunamente ridotte alcune funzionalità per garantirne l'interoperabilità con il software AntiVirus già presente sul PC/Server. Questo però permette il controllo incrociato mediante la scansione.
- identifica e, in moltissimi casi, anche rimuove la maggior parte dei virus/malware realmente circolanti o, in alternativa, ne permette l'invio al C.R.A.M. Centro Ricerche Anti-Malware di TG Soft per l'analisi e l'aggiornamento di Vir.IT eXplorer per l'univoca identificazione e la corretta rimozione;
- grazie alla tecnologia Intrusione Detection, resa disponibile anche nella versione Lite di Vir.IT eXplorer, il software è in grado di segnalare eventuali virus/malware di nuova generazione che si siano posti in esecuzione automatica e procedere all'invio dei file segnalati al C.R.A.M. di TG Soft.
- Procedi al download di Vir.IT eXplorer Lite dalla pagina ufficiale di distribuzione del sito di TG Soft.
VirIT Mobile Security AntiMalware ITALIANO per TUTTI i dispositivi AndroidTM
VirIT Mobile Security software Anti-Malware Italiano che protegge smartphone e tablet Android™, da intrusioni di Malware ed altre minacce indesiderate, e che dà la possibilità all'utente di salvaguardare la propria privacy con un approccio euristico avanzato (Permission Analyzer).
 TG Soft rende disponibile gratuitamente VirIT Mobile Security accedendo al market di Google Play Store (https://play.google.com/store/apps/details?id=it.tgsoft.virit) dal quale è possibile prelevare la versione Lite, liberamente utilizzabile sia in ambito privato che aziendale.
TG Soft rende disponibile gratuitamente VirIT Mobile Security accedendo al market di Google Play Store (https://play.google.com/store/apps/details?id=it.tgsoft.virit) dal quale è possibile prelevare la versione Lite, liberamente utilizzabile sia in ambito privato che aziendale.
E’ possibile eseguire il passaggio alla versione PRO, acquistandolo direttamente dal nostro sito=> clicca qui per ordinare
Ringraziamenti
Il Centro Ricerche Anti-Malware di TG Soft ringrazia tutti i gli utenti, i clienti, i tecnici dei rivenditori e tutte le persone che hanno trasmesso/segnalato al nostro Centro Ricerche materiale riconducibili ad attività di Phishing che ci hanno permesso di rendere il più completa possibile questa informativa.
Come inviare e-mail sospette per l'analisi come possibili phishing ma anche virus/malware o Crypto-Malware
L'invio di materiali da analizzare al Centro Ricerche Anti-Malware di TG Soft per l'analisi che è sempre e comunque gratuito può avvenire in tutta sicurezza in due modalità:
- qualsiasi e-mail che sia da considerarsi sospetta può essere inviata direttamente dalla posta elettronica del ricevente scegliendo come modalità di invio "INOLTRA come ALLEGATO" e inserendo nell'oggetto "Possibile Phishing da verificare" piuttosto che "Possibile Malware da verificare" alla mail lite@virit.com
- salvare come file esterno al programma di posta elettronica utilizzato la mail da inviare al C.R.A.M. di TG Soft per l'analisi. Il file che ne risulterà dovrà essere inviato facendone l'Upload dalla pagina di INVIO File Sospetti. Naturalmente per avere un feed-back rispetto al responso dell'analisi dei file infetti inviati sarà necessario indicare un indirizzo e-mail e sarà gradita una breve descrizione del motivo dell'invio del file (ad esempio: possiible/probabile phishing; possibile/probabile malware o altro).
 Per maggiori approfondimenti su come inoltrare in sicurezza e-mail sospette vi invitiamo a consultare la seguente pagina pubblica: Come inviare e-mail sospette per l'analisi
Per maggiori approfondimenti su come inoltrare in sicurezza e-mail sospette vi invitiamo a consultare la seguente pagina pubblica: Come inviare e-mail sospette per l'analisi
Tutto questo per aiutare ad aiutarvi cercando di evitare che possiate incappare in furti di credenziali, virus/malware o ancor peggio Ransomware / Crypto-Malware di nuova generazione.
C.R.A.M. Centro Ricerche Anti-Malware di TG Soft


 Se non doveste ancora utilizzare Vir.IT eXplorer PRO è consigliabile installare, ad integrazione dell'antivirus in uso per aumentare la sicurezza dei vostri computer, PC e SERVER indifferentemente, Vir.IT eXplorer Lite -FREE Edition-.
Se non doveste ancora utilizzare Vir.IT eXplorer PRO è consigliabile installare, ad integrazione dell'antivirus in uso per aumentare la sicurezza dei vostri computer, PC e SERVER indifferentemente, Vir.IT eXplorer Lite -FREE Edition-. TG Soft rende disponibile gratuitamente VirIT Mobile Security accedendo al market di Google Play Store (https://play.google.com/store/apps/details?id=it.tgsoft.virit) dal quale è possibile prelevare la versione Lite, liberamente utilizzabile sia in ambito privato che aziendale.
TG Soft rende disponibile gratuitamente VirIT Mobile Security accedendo al market di Google Play Store (https://play.google.com/store/apps/details?id=it.tgsoft.virit) dal quale è possibile prelevare la versione Lite, liberamente utilizzabile sia in ambito privato che aziendale. Per maggiori approfondimenti su come inoltrare in sicurezza e-mail sospette vi invitiamo a consultare la seguente pagina pubblica: Come inviare e-mail sospette per l'analisi
Per maggiori approfondimenti su come inoltrare in sicurezza e-mail sospette vi invitiamo a consultare la seguente pagina pubblica: Come inviare e-mail sospette per l'analisi