Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
If you received a suspicious email, send it to C.R.A.M. (Center for Anti-Malware Research)
: How to send suspicious emails
How Cryakl reveals itself
The infection vector used by Cryakl is e-mail. Two malware campaigns spreading the Cryakl ransomware were identified on September 9 and September 21. In the picture below we can see the Cyrillic email (targeting Russia and Eastern European countries) related to the September 9 camapaign.
We can't exclude that the examples given may change and other circulating mails can be different or translated into other languages.
| ?????? ????????????? ?? ???????? ???????????? - Mozilla Thunderbird |
Da:
Oggetto: ?????? ????????????? ?? ???????? ????????????
A: |
Здравствуйте.
Убедительно просим Вас погасить текущую задолженность до 1.11.2018 года.
На сегодняшний день сумма Вашей общей задолженности перед ООО «БухБИГ» составляет 24,712 рублей.
Если долг не будет погашен в указанные сроки, мы будет вынуждены обратиться в суд.
Отправляю еще раз, копию счета и договор.
С уважением,
Алексей Воронов.
|
1 allegato: ????????????2??????? .zip
|
The message that the unfortunate user receives, looks like those that occur when payment reminders are received in the mailbox.
The text (translated) asks to pay off an alleged debt before November 1, 2018 and deceives the user by writing the number "24,712 rubles" and the name of a company "BuhBIG". However what prompts the user to open the attachment urgently, is a threat written in the end of the email, that says:
"If the debt is not repaid within the specified time, we will be obliged to apply to the court."
If you open the compressed attachment to see its contents, you should check the file type inside, regardless of the misleading name it has.
The Cryakl ransomware examined by TG Soft's C.R.A.M. is "triggered" by the execution of a file (.scr) inserted into an archive file, contained in another ".zip" file attached to a fake email.
In the case examined, the ".zip" file containing the malware and the malware itself are called "копия счета и договор" [translated= "copy of the account and contract"]. If the user opens and executes the ".scr" file, it will activate Cryakl Ransomware in the system.
|
- File Name : <file_con_nome_cirillico>.zip
- Size: 227.417 byte
- Md5: 43270C7F68329D197BE21D27AFE37250
Inside the file "<file_with_cirillic_name>.zip", we find the file "
копия счета и договор.scr". This, after its execution, creates a copy of itself in the user's temporary folder which will then be launched to start the data encryption process. The mentioned executable, analyzed by
TG Soft's C.R.A.M. (Anti-Malware Research Center) has the following characteristics:
- File Name: копия счета и договор.scr
- VirIT: Trojan.Win32.CryptCryAkl.AD
- Size: 236.544 byte
- Md5: 6C01E0F297DEBE4606CF2CAB510C38AB
The document file inside the computer will be encrypted and renamed like this:
"email-vally@x-mail.pro.ver-CL1.5.1.0.id-2564879395-6255388384519840209810.fname-{ORIGINAL FILE NAME}.doubleoffset."
How Cryakl works
Once the file "
копия счета и договор.scr" is executed, it reruns and creates a temporary file in the following path "
C:\Users\[USER]\AppData\Local\Temp\[NUMERO IDENTIFICATIVO]" with a name equal to the victim's ID number.
It then attempts to connect to the two C&C servers:
- "dyrovpa9[.]beget[.]tech"
- "www[.]vabel[.]fr"
transmitting the Ransomware version (1.5.1.0) in addition to the unfortunate user's ID number, with the following string"/inst.php?vers=CL%201.5.1.0&id=[NUMERO IDENTIFICATIVO]-248183364050830553060281&sender= HTTP/1.1".
It then proceeds by extracting a copy of itself in temp called "
NOMECASUALE.exe" and executes it with the following command:
C:\Users\[UTENTE]\AppData\Local\Temp\[NOMECASUALE].exe "C:\Users\[UTENTE]\AppData\Local\Temp\[NOMECASUALE].exe". This re-run again before proceeding to the next step.
When the various preparation steps are finished, the last execution of "NOMECASUALE.exe" checks if the file is still present in"C:\Users\[UTENTE]\AppData\Local\Temp\[NUMERO IDENTIFICATIVO]"and, immediately after that, creates a registry key that sets the malware autostart.
HKCU\software\microsoft\windows\currentversion\run
[NUMERO IDENTIFICATIVO] = C:\Users\[UTENTE]\AppData\Local\Temp\NOMECASUALE.exe
HKLM\software\microsoft\windows\currentversion\run
[NUMEROCASUALE] = [NUMEROCASUALE]
It then creates in each folder on the system the file "README.txt" containing the e-mail to contact for information on how to pay the ransom, as shown below:
Your files was encrypted! Write us:
vally@x-mail.pro
vally@x-mail.pro
vally@x-mail.pro
|
Now the data encryption step begins, starting with the first folder in "A:\", enumerating all folders on the disk and all drives present.
Once the encryption process is finished and the ".doubleoffset" extension is added, the malware will execute some commands that allow the shadow copies to be deleted:
C:\Windows\system32\schtasks.exe "C:\Windows\system32\schtasks.exe" /Create /RU SYSTEM /SC ONCE /TN VssDataRestore /F /RL HIGHEST /TR "vssadmin delete shadows /all /quiet" /st 00:00
open schtasks /Create /RU SYSTEM /SC ONCE /TN VssDataRestore /F /RL HIGHEST /TR "vssadmin delete shadows /all /quiet" /st 00:00 |
The Ransomware then opens a message screen, inviting the user to write an e-mail for information on how to decrypt his files, to the address that will be shown.
|
The picture on the right shows the screen with the e-mail address to contact to recover the now already encrypted files, after ransom payment.
|
|
The wallet listed for payment is.:
WALLET = 1FJ1evxv3eUimCrtujLt78M6Uk3QJfyqpd
The amount of the ransom required to decrypt the files, as of 09/24/2018 is 0.1 BTC.
0.1BTC = 561.13 €
0.1BTC = 660.61 USD (Dollari statunitensi)
To date, the Wallet of the miscreants has received payments of 0.03979206 BTC.
**On 21/09/2018, a new campaign was found spreading a variant of the ransomware with different MD5.
- File Name : <file_con_nome_cirillico>.zip
- Size: 159.995 byte
- Md5: 8BB56E3AC67FD9DF2879D3C1BF61B3FE
inside is the file:
- File Name: <file_con_nome_cirillico>.scr
- VirIT: Trojan.Win32.CryptCryAkl
- Size: 174.080 byte
- Md5: 0FF29C048FA497E7616FA42EE44F85AD
It is probably not redundant to mention that Ransomware is aimed at extorting money. For this reason, the files from which the encryption process is triggered are artfully modified to avoid being recognized by the most commonly used antivirus software, so that they can continue undisturbed with their encryption attempts and related ransom demand.
Considering all this, the interception of the malicious file cannot rely on classical methods, but must necessarily use other approach methodologies such as heuristic-behavioral. These technologies enable recognition of the behavior of the process itself once it is active, regardless of the carrier file, monitoring its execution and the activities performed.
It is important to know that:
- There is no assurance that software will be forwarded after payment to provide for de-cryption of the files taken hostage;
- Paying gives strength to cyber criminals who, with the gains made, will continue their extortion activities with even greater effort and even more sophisticated methodologies. It is therefore good to avoid feeding this "market."
Below we will provide
important tips for defense against
Crypto-Malware and/or mitigation of its damage if you come in contact with ransomware such as
Cryakl.
IOC
MD5:
8BB56E3AC67FD9DF2879D3C1BF61B3FE
43270C7F68329D197BE21D27AFE37250
6C01E0F297DEBE4606CF2CAB510C38AB
0FF29C048FA497E7616FA42EE44F85AD
URL:
dyrovpa9[.]beget[.]tech (C&C)
www[.]vabel[.]fr (C&C)
Protection against Ransomware / Crypto-Malware
Vir.IT eXplorer PRO can identify and block even this Crypto-Malware already in the initial stages of the data file encryption attack against PC/ SERVER.
As reported, the heuristic-behavioral AntiRansomware Crypto-Malware protection technologies built in
Vir.IT eXplorer PRO, when properly installed, configured, updated and used, mitigate this type of attacks safeguarding from encryption, on average, at least
99.63% of PC and SERVER data files. Besides through
Vir.IT BackUp we can recovery encrypted files in the initial phase of the attack, up to 100% .
When the "Alert" generated by Vir.IT eXplorer PRO appears on the screen (visible just below on the right ) the AntiRansomware protection Crypto-Malware technologies are already BLOCKING the malware.When this happens, avoid "panic", DO NOT close the window and perform the operations indicated:
- DISCONNECT the LAN NETWORK CABLE: This will physically isolate that PC / SERVER from any other computers connected with it on the Lan network while keeping the attack limited to that computer only.
- DO NOT REBOOT THE COMPUTER: We recommend that you do not turn off and/or reboot your PC/Server but contact, as soon as possible, our technical support by writing an email reporting the current situation to the address assistenza@viritpro.com. Then contact the technical support numbers 049.631748 and 049.632750, free of charge for customers with Vir.IT eXplorer PRO license, on business days Monday through Friday 8:30 a.m. to 12:30 p.m. and 2:00 p.m. to 6:00 p.m.
|
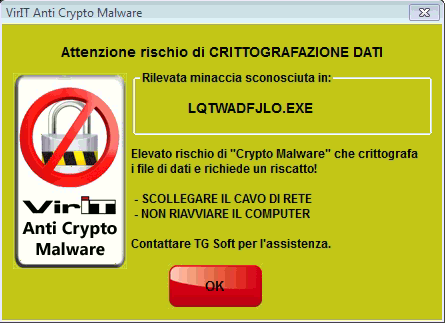
Click to enlarge
99,63%*
Average percentage expectation of files saved from encryption by Vir.IT eXplorer PRO's Anti-CryptoMalware protection ==> See the disclosure
|
You have Vir.IT eXplorer PRO on your computers
Vir.IT eXplorer PRO when properly installed, configured, updated and used following the Alert directions of AntiRansomware Technologies Crytpo-Malware protection, will allow you to safeguard from encryption, on average, AT LEAST 99.63% of your valuable data files.
In addition, through the technologies built into Vir.IT eXplorer PRO, capable of de-encrypting and restoring encrypted files, it is possible to de-encrypt/restore up to 100 percent of the files potentially encrypted in the initial phase of the attack.
These technologies are listed below:
- For some types/families of Crypto-Malware Vir.IT eXplorer PRO can capture the private encryption key when it is available in the clear, that is the activation of the encryption process. By using the encryption key through the built-in tools of Vir.IT eXplorer PRO we will de-encrypt the encrypted files at the initial stage of the attack without losing any modifications.
- For some types/families of Crypto-Malware Vir.IT eXplorer PRO the recovery is possible through Backup on-the-fly. This is a technology built into the resident shield, which automatically makes backup copies of the most common types of data files (files less than 3 MB in size). The backups made by Backup-on-the-fly allow files to be restored without losing any changes.
- Vir.IT Backup. If de-cryption or file restoration using the two technologies listed above fail to recover all of the files encrypted in the initial phase of the attack, it will be possible to restore the missing files from the backup files generated by Vir.IT Backup.
|
You do NOT have AntiVirus-AntiSpyware-AntiMalware software that can block encryption from next-generation Crypto-Malware attacks...
If there is no tool in the system that can signal and block file encryption, in the specific case of Crypto-Malware attack we recommend:
- DISCONNECT the LAN NETWORK CABLE.;
- POWER OFF the PC / SERVER so to limit the number of encrypted files.
- Contact your system technical support reporting the particular critical situation in place possibly referring to this information.
|
For more info please contact our administrative and commercial secretary by calling during office hours at 049.8977432.
C.R.A.M.
TG Soft's Anti-Malware Research Center
*Average percentage of files saved from encryption by Anti-CryptoMalware technology integrated in Vir.IT eXplorer PRO determined based on attacks objectively verified by TG Soft's C.R.A.M. in October 2015.






