PHISHING INDEX
Below are the most common email phishing attempts detected by the TG Soft Anti-Malware Research Center in August 2025:
21/08/2025 =>
Email Account
19/08/2025 =>
SumUp
15/08/2025 =>
Aruba - Please renew your domain
13/08/2025 =>
SCAM Carabinieri Police Force
13/08/2025 =>
Aruba - Account verification
11/08/2025 =>
ING Direct
11/08/2025 =>
BRT
09/08/2025 =>
PayPal
06/08/2025 =>
Aruba - Security Update
05/08/2025 =>
APS
05/08/2025 =>
Nexi Smishing
05/08/2025 =>
Phishing Survey - TEMU /DECATHLON
04/08/2025 =>
Aruba- Expired domain
04/08/2025 =>
ING Direct
01/08/2025 =>
Europages
These emails aim to deceive unsuspecting victims into providing sensitive information, such as bank account details, credit card codes, or personal login credentials, with all the easily imaginable consequences.
21 August 2025 ==> Phishing Email Account
SUBJECT: <
Notice: Domain %User_name% expired – renewal required>
The message, of suspicious origin, informs the recipient that his/her domain %User_name% has expired, and must be renewed immediately to prevent the suspension of related services, including the email account.
It then indicates a generic domain and a fee of €5.99 to be paid for its renewal. The failure to renew the domain would result in the deactivation of the website and email account and the permanent loss of the domain linked to them.
To avoid these effects, users simply need to renew by clicking on the link:
Renew Now
When we analyse the email, we realise that something is not normal. In fact, it lacks information about the sender of the message, there are no identifying logos, and moreover, the email address <
maya(at)gianiarrigucci(dot)it> cannot be traced back to any official domain. There is also no information about the recipient of the message or the domain to be renewed, as the one indicated is generic and unreliable. All these facts are highly unusual and should arouse the recipient's suspicion. Another thing that immediately stands out is the request to renew the domain via a link sent by e-mail, which is therefore not secure.
Anyone who unluckily clicks on the
Renew Now link, will be redirected to an anomalous WEB page, which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for criminal purposes.
We always urge you to pay attention to even the smallest details and not to enter your personal details and/or passwords on websites whose origin you do not know, as they will be sent to a remote server and used by cyber fraudsters, with all the associated risks that this entails.
19 August 2025 ==> Phishing SumUp
SUBJECT: <
We require you to confirm your email address immediately..>
Below, we analyze a new phishing attempt that claims to be an official communication from SumUp, a well-known London-based digital payments company.
The message asks the recipient to verify his/her email address immediately, thus ensuring the security and proper functioning of the SumUp account. To confirm, the recipient simply needs to click on the following link:
Confirm your email address
The well-known London-based company is clearly not involved in the mass sending of these emails, which are genuine scams whose aim, as always, is to steal sensitive data from unsuspecting recipients.
When we analyze the message carefully, we see some clues that should raise suspicion. In fact, the email address <
20printer[at]myt[dot].mu> does not belong the SumUp official domain. This is definitely unusual and should make us suspicious. Another strange fact is the lack of customer identification data and the request to enter account credentials via a link sent by email.
Anyone who unluckily clicks on the
Confirm your email address link, will be redirected to an anomalous WEB page, which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for criminal purposes.
We always urge you to pay attention to even the smallest details and not to enter your personal details and/or passwords on websites whose origin you do not know, as they will be sent to a remote server and used by cyber fraudsters, with all the associated risks that this entails.
15 August 2025 ==> Phishing Aruba - Please renew your domain
SUBJECT: <
Please renew your domain>
Phishing attempts, claiming to be communications from the
Aruba brand, continue.
The message informs the recipient that, despite several attempts, the bank refuses to charge the costs for renewing his/her
Aruba services, which amount to €46.00. It is therefore necessary to fill in an online renewal form, following the instructions contained in the following link:
log in to your account
If the domain is not renewed, the services associated with it will be deactivated and it will no longer be possible to use them
If we examine the text of the email, weeasily see that it is not at all trustworthy. We can immediately see that the email address <
document[at]lcbrdoc[dot]com> is not traceable to the official
Aruba domain. Moreover, the message is pretty generic, doesn't give any info about the customer or account, and has a bunch of syntax errors, which should make us suspicious. Another weird thing is that to update, you need to enter your account details through a link sent by email.
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
We always urge you to pay attention to every detail, even the minor ones, to avoid rushing, and to refrain from entering your personal data and/or passwords on forms hosted on fake web pages. In fact these details will be sent to the cybercriminals behind the scam, who will use them for criminal purposes.
13 August 2025 ==> SCAM Carabinieri Police Force
«SUBJECT: <
Viewing of child pornography.>
Below is an example of a SCAM attempt, carried out through an email citation for child pornography allegedly sent by the
General Command of the Carabinieri.
The message has a very suspicious email address <
consorsbankde[at]btconnect[dot]com> and contains the following text: "We wish to inform you that a summons has been sent to you.
After careful verification of your Internet traffic and associated devices, it has been found that you have viewed pornographic content, including content involving persons under the age of 18.
Please read the attached document, which contains important information concerning this summons. As part of this procedure, we ask you to clarify your recent Internet activities and to fully cooperate."
An email address is then provided <
armadeicarabinieri[at]btconnect[dot]com> to reply to, after viewing the attached .pdf file named <
Armadeicarabinieri_Scan>. When we open the attachment, which we see below, we notice that it is graphically misleading, and appears to come from
Dr Salvatore Luongo, Commander General of the Carabinieri. The complaint referred to in the message refers to a case of child pornography, paedophilia, exhibitionism and cybernetic pornography and concerns the victim because, according to the FALSE complaint, he visited a child pornography site.

This is an attempted scam by cyber criminals, with the aim of extorting a sum of money, in this case in the form of a fine. In fact, the message reads as follows:
"
We ask you to report your case by e-mail, writing your justifications so that they can be examined and verified in order to assess the penalties; this must be done within a strict deadline of 72 hours.."
If the victim does not respond within 72 hours, a warrant will be issued for immediate arrest by the postal or municipal police, resulting in registration in the national sex offenders register.
It is quite easy to see that this is a false complaint. First of all, the complaint is not personal, and secondly, the document contains a very suspicious stamp.
This is clearly an attempt at fraud with the aim to steal sensitive user data and extort money.
13 August 2025 ==> Phishing Aruba - Account verification
SUBJECT: <
Account verification>
Here we find another phishing attempt claiming to be a communication from the
Aruba brand.
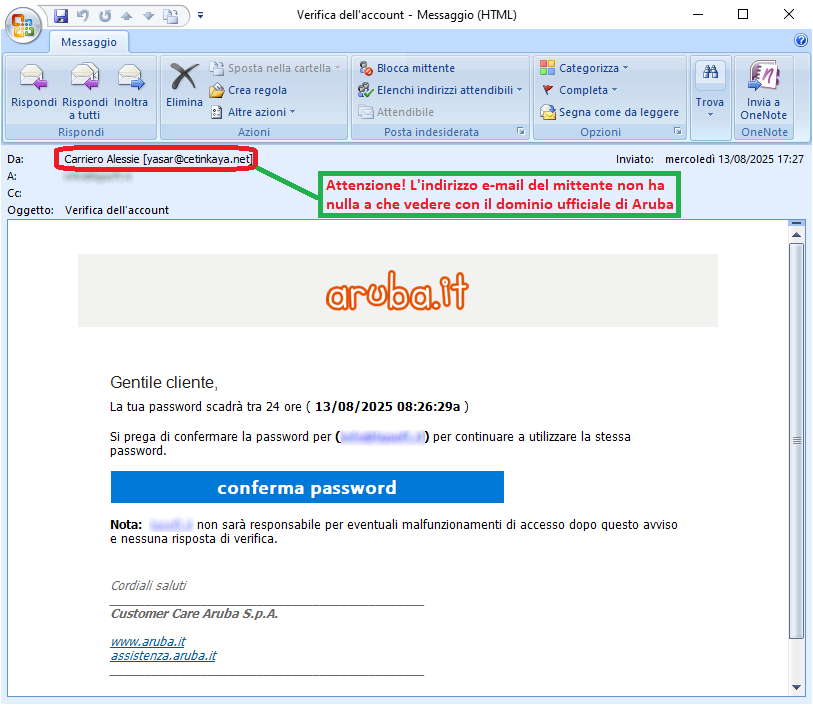
The message informs the recipient that the password for his/her account hosted on
Aruba will expire in 24 hours. It then invites the user to confirm his/her password in order to continue using it, via the following link:
password confirmation
Clearly, the well-known web hosting, e-mail and domain registration services company Aruba is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
If you carefully analyse the message, there are some clues that should raise suspicion. The email address of the message <yasar(at)cetinkaya(dot)net> does not belong to the official
Aruba domain, which is definitely unusual.
Anyone who unluckily clicks on the
password confirmation link will be redirected to a web page that, although it looks like the
Aruba account login page, as the cybercriminal has been clever enough to include the well-known company's logo, has an unusual address/domain:
[FakeDomain]document-file****online[.]cfd
On this page, the user is invited to access his/her customer area inserting the login and password of his/her email address, in order to recover messages before they are deleted.
We always urge you to pay attention to every detail, even the minor ones, to avoid rushing, and to refrain from entering your personal data and/or passwords on forms hosted on fake web pages. In fact these details will be sent to the cybercriminals behind the scam, who will use them for criminal purposes.
11 August 2025 ==> Phishing ING Direct
SUBJECT: <
Your advisor has sent you a new important message!>
Phishing attempts, posing as official communications from ING, continue.
The message, which employs stolen or similar graphics to those of a prominent banking institution, aims to appear official and prompts the recipient to provide his/her personal information.
The message warns that, in order to ensure account security, user's login details must be verified. This is a new security measure designed to prevent unauthorised access. If this procedure is not completed within 7 days, access to user's account will be restricted.
To complete the verification, the user simply needs to click on the following link:
Reserved Area
Clearly, ING is not involved in the mass sending of these emails, which are scams whose aim, as always, is to steal the home banking login credentials and/or money of the unsuspecting recipient.
Although the cybercriminal had the foresight to include a customer service number to contact in case of doubts and a logo similar to the logo of the well-known bank, which could easily mislead users, there are some clues that should raise suspicion. When we analyse the text of the message, we immediately see that it is generic and that the sender's email address <
quimenezjosyc(at)lopicrew(dot)com> does not belong to the official ING domain. Another unusual occurrence is the request to update the user's details entering his/her home banking credentials via a link sent by email.
Anyone who unluckily clicks on the
Reserved Area link, will be redirected to a fraudulent web page unrelated to the official ING website, as it is managed by cybercriminals whose goal is to obtain your home banking login details in order to use them for criminal purposes and/or to transfer funds..
We therefore urge you to always pay attention to even the smallest details and not to enter your personal details and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber fraudsters.
11 August 2025 ==> Phishing BRT
«SUBJECT:
< PAYMENT OF IMPORT DUTY/TAX IS REQUIRED >
Below is a new phishing attempt, which hides behind a fake communication from the courier
BRT, concerning the delivery of an alleged parcel.
The message informs the unsuspecting recipient that his or her shipment is on hold because ‘
PAYMENT OF IMPORT DUTY/TAX IS REQUIRED’ to receive the package. It then informs him or her that in order to receive the package, he or she must confirm advance payment of customs fees of
€ 2,99.
These messages are increasingly being used to scam consumers who are more and more likely to shop online.
A partially obfuscated tracking number is also provided. <#714****563>">. To proceed with the shipment, the recipient must click on the following link:
Click here
The email address of the message <
delcasoamaro(at)yahoo(dot)es> is unrelated to the
BRT domain, a highly unusual circumstance that should raise suspicion.
Anyone who clicks on the links will be redirected to a malicious web page.
Although the landing page is graphically misleading, its URL address is unrelated to the official domain of
BRT.
On this page, the user is asked to reschedule the delivery of their alleged parcel. The shipment details and the total cost to be paid, equal to €1.38, are shown. We immediately notice that this sum does not match the amount indicated previously. The user is then asked to pay using the following button:
Pay for shipping
Moving forward, the victim is redirected to another page where he/she is asked to enter his/her credit card details to pay €1.38 for shipping. We observe that the URL address of the browser is abnormal and cannot be traced back to the official domain of the courier.
https[:]//[FakeDomain*]/fg/NEWBRTIT/BRTIT/post/6899.....
If you enter your data into counterfeit websites, in fact, it will be delivered to the cyber-criminals behind the scam who will use it for criminal purposes. We therefore urge you not to rush and always pay attention to every detail, even trivial ones.
09 August 2025 ==> Phishing PayPal
SUBJECT: <
Unknown device detected: check your PayPal account immediately #TP10HE>
Below, we analyse a new phishing attempt that aims to steal login credentials for
PayPal accounts, the well-known US digital payments company.
The message informs the recipient that an access to his/her
PayPal account has been detected from an unknown device and asks him/her to confirm whether the access is allowed. The details of the alleged device that accessed the account, the location and the date are reported, followed by an email address that matches the recipient's email address. The message then asks the recipient to report whether the access is authorised or not. If the device is known, no action is required, otherwise the recipient is asked to report the device so that it can be removed via the following link:
Remove Device
When we analyse the email, we see that the message comes from an email address <xsend8065061[at]molinaroservizi[dot]it>, which is clearly not part of the PayPal official domain. This is definitely unusual and should make us suspicious.
Anyone who unluckily clicks on the
Remove Device link, will be redirected to a fraudulent web page, which has already been reported as a DECEPTIVE PAGE/WEBSITE.
Considering these points, we warn you to NEVER enter your credentials on websites whose origin you do not know, as they will be sent to a remote server and used by cybercriminals, with all the risks that this entails.
06 August 2025 ==> Phishing Aruba - Security Update
SUBJECT: <
****-Deactivation Last warning>
Phishing attempts, claiming to be communications from the
Aruba brand, continue.
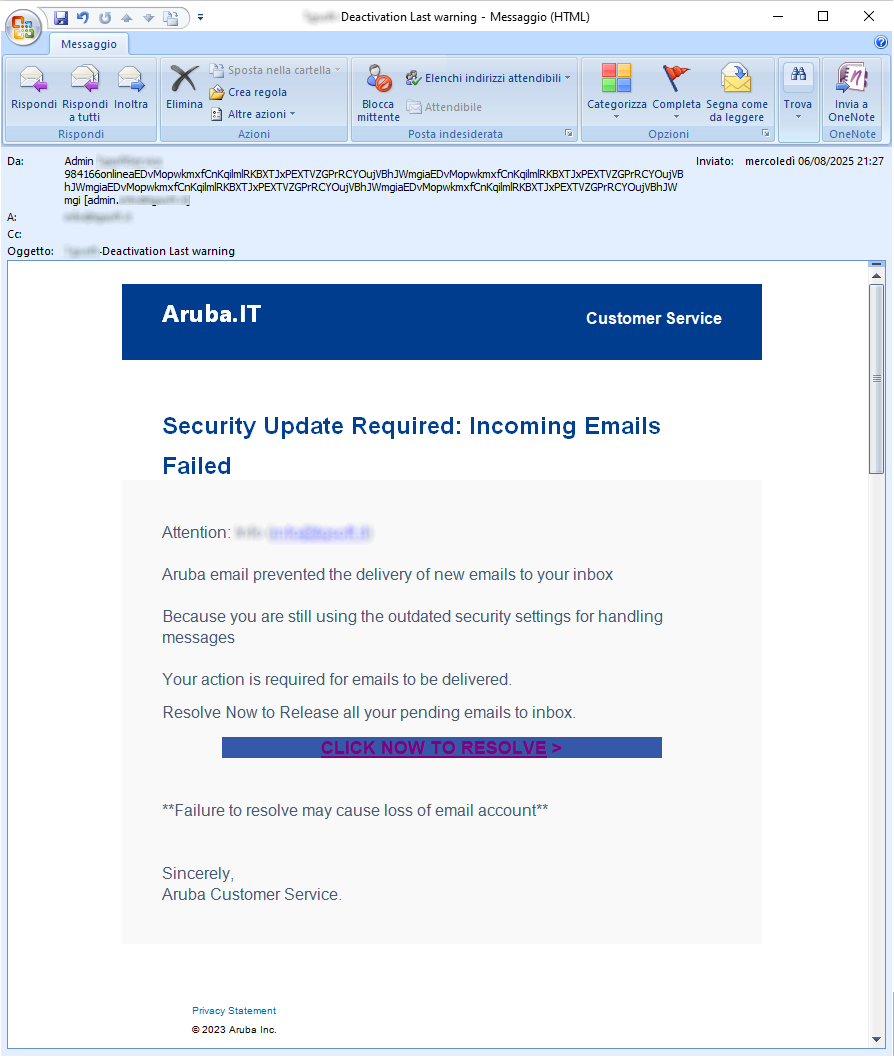
The message, in English, informs the recipient that the
Aruba servers have blocked incoming emails to his/her email account because he/she is still using outdated security settings for message management.
It then invites the user to take action and update the security system so that emails can be delivered, via the following link:
CLICK NOW TO RESOLVE>
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba, is uninvolved in the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal the unsuspecting recipient's sensitive data.
If we carefully analyse the message, there are some clues that should raise suspicion. We immediately notice that the email address of the message is not traceable to the official
Aruba domain, a highly unusual fact.
Anyone who unluckily clicks on the link
CLICK NOW TO RESOLVE> will be redirected to a web page that, although it visually mimics the login page of an
Aruba account - since the cybercriminal took care to include the company's logo -is not at all trustworthy. In this case too, the address/domain is anomalous:
https[:]//[FakeDomain]//wp-content/languages/plugins/l/l//****
On this page, the user is invited to log in to his/her customer area with his/her e-mail login and password to retrieve messages before deletion.
We always urge you not to be in a hurry, to pay attention to every detail, even trivial ones, and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as these will be delivered to cyber criminals who will use them for criminal purposes.
05 August 2025 ==> Phishing APS
Below, we analyse the following scam attempt hidden behind a fake communication from the Padua public transport company
APS Holding.
If you received the link mentioned on the side, please be careful as it is a scam attempt aimed at stealing your personal data.
Below, we analyse the link:
https[:]//www[.]facebook[.]com/share/16p6vcwUzm
Anyone who clicks on the link will be redirected to a page hosted on the well-known social networking site, which simulates the Padua public transport page. We would like to remind you that this page is not managed by
APS, as stated in the message, but by the
BusItalia company. The landing page, graphically well designed, boasts the chance to win, only for residents of Padua, ‘a limited edition transport card (...) 6 months of free travel for only €1!’. To try and win this gift, available only to 500 lucky users for the 25th anniversary of APS, all the receivers need to do is to click on the link provided:
https[:]//wanalo[.]com/zbcgQB1N
When we click on the link, we'll be taken to a short survey where we'll be asked to answer 3 questions to win a 6-month public transport pass.
|
Question 1 of 3
|
Question 2 of 3
|
|
Question 3 of 3
|
Survey end
|
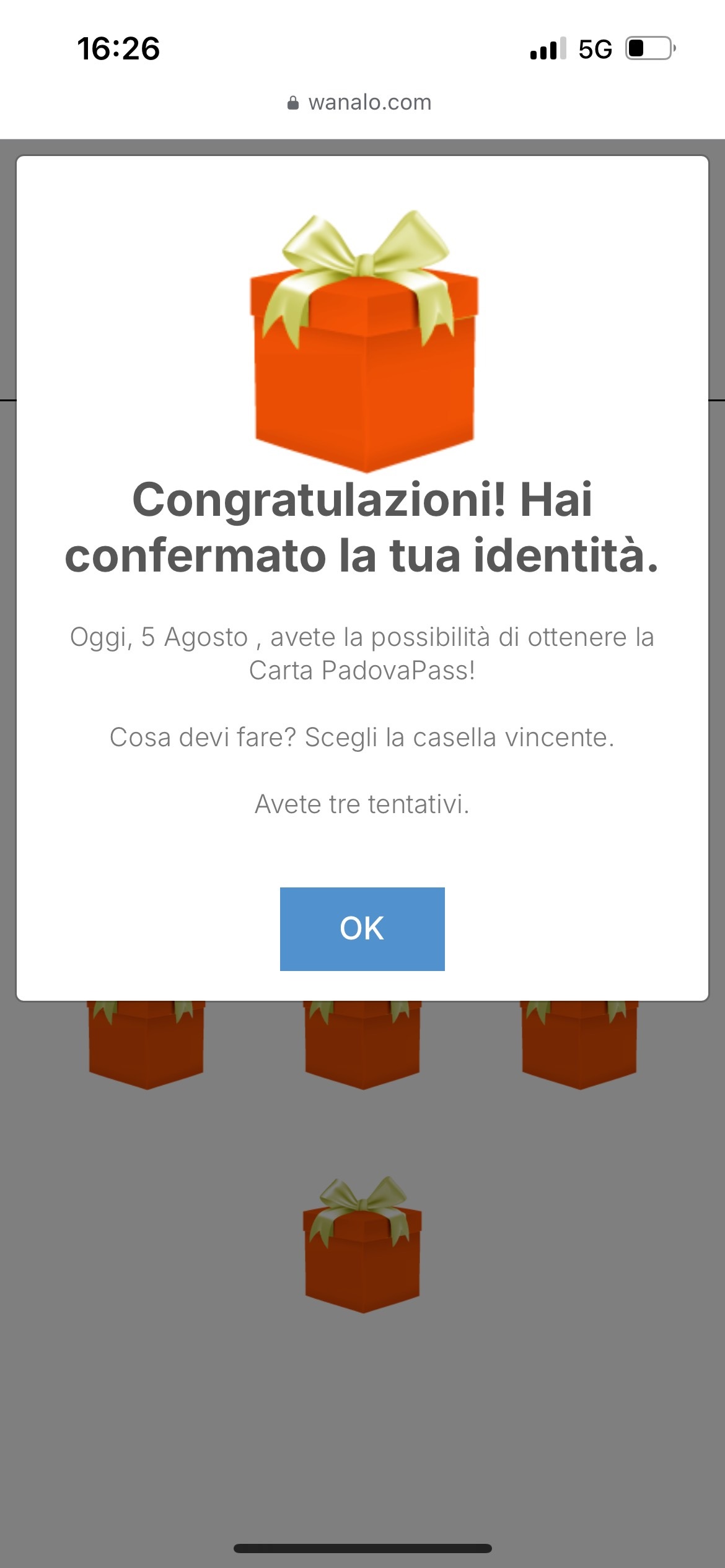
After completing the questionnaire, we finally arrive at a new screen that confirms the answers and allows us to try to win the prize by selecting one of the boxes displayed on the screen. We have 3 attempts, and on the second attempt we succeeded! We are then redirected to the screen on the side where the INSTRUCTIONS on how to win the
APS PadovaPass card...
We point out that the site is hosted on a URL unrelated to
APS:
wanalo[.]com
The purpose of the message is to induce the user to enter his/her personal data to make a payment of €1, making him/her believe that he/she will receive a pass to travel for free for 6 months! In fact, on the next screen, the user is asked to enter his/her personal data and delivery address to receive the pass at home.
To conclude, we always advise you to be wary of any email that asks you to enter confidential data, and to avoid clicking on suspicious links. These could lead to a fake website, difficult to distinguish from the original, putting your most valuable data in the hands of cyber fraudsters who can use it at will.
05 August 2025 ==> Smishing Nexi
We analyse below a new smishing attempt behind a fake text message from
Nexi.
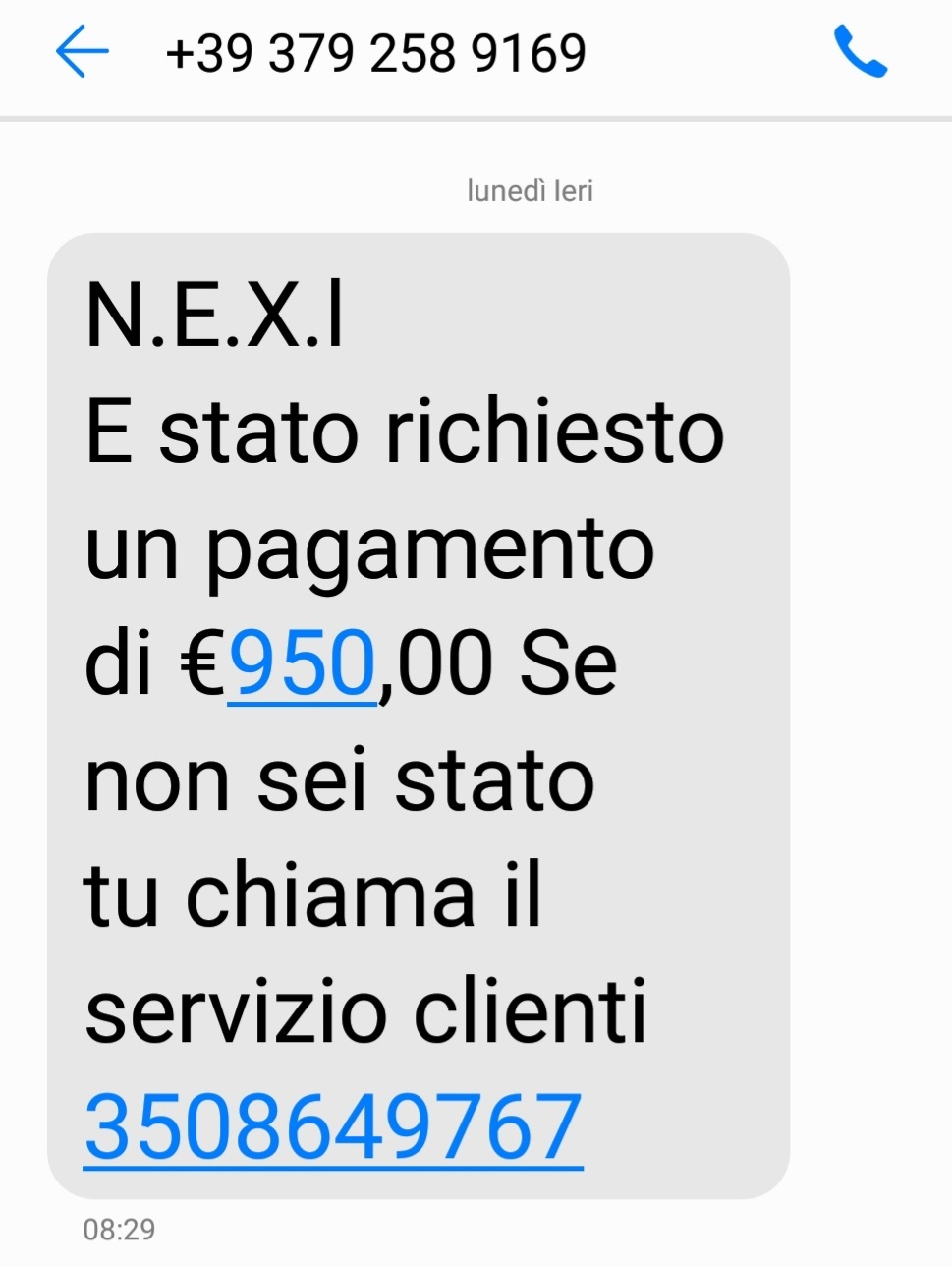
The message, which we quote on the side, informs the unsuspecting recipient that a payment of EUR 950.00 has been requested on his
Nexi credit card. It then warns him/her that if he/she did not authorise the payment, to call the customer service on the number:
3508649767
If the recipient of the text message is not a Nexi customer, he or she can obviously more easily understand that it is anomalous. In any case, it is essential to know how to recognise these now widespread attempts at computer fraud. We remind you that under no circumstances does
Nexi, or any other banking/payment institution, ask customers to provide their payment card details via email, text message or call centre.
The intention of the cyber criminals is to prompt the user to click on the link in order to block the unauthorised transaction.
Already at a glance, however, we can see that the text message is rather anomalous, as it contains a link that hides behind both the transfer amount “
950” and the telephone number given as customer service. The links they refer to are deceptive scam sites that graphically simulate the original sites.
If you enter your Nexi account login details on these FORMS hosted on counterfeit web pages, they will be sent to a remote server and used by cyber crooks with all the associated risks that are easy to imagine.
05 August 2025 ==> Phishing customer survey: TEMU / DECATHLON
Customer survey-themed phishing campaigns, exploiting well-known brands, continue. In the two cases described below, the companies are large-scale retailers.
In the first example, the cybercriminal used the well-known
Decathlon brand, which appears to be launching a promotional message offering the chance to win an exclusive prize: a <
Quechua Hiking Equipment Package>. To claim the prize, recipients just have to answer a few short questions.
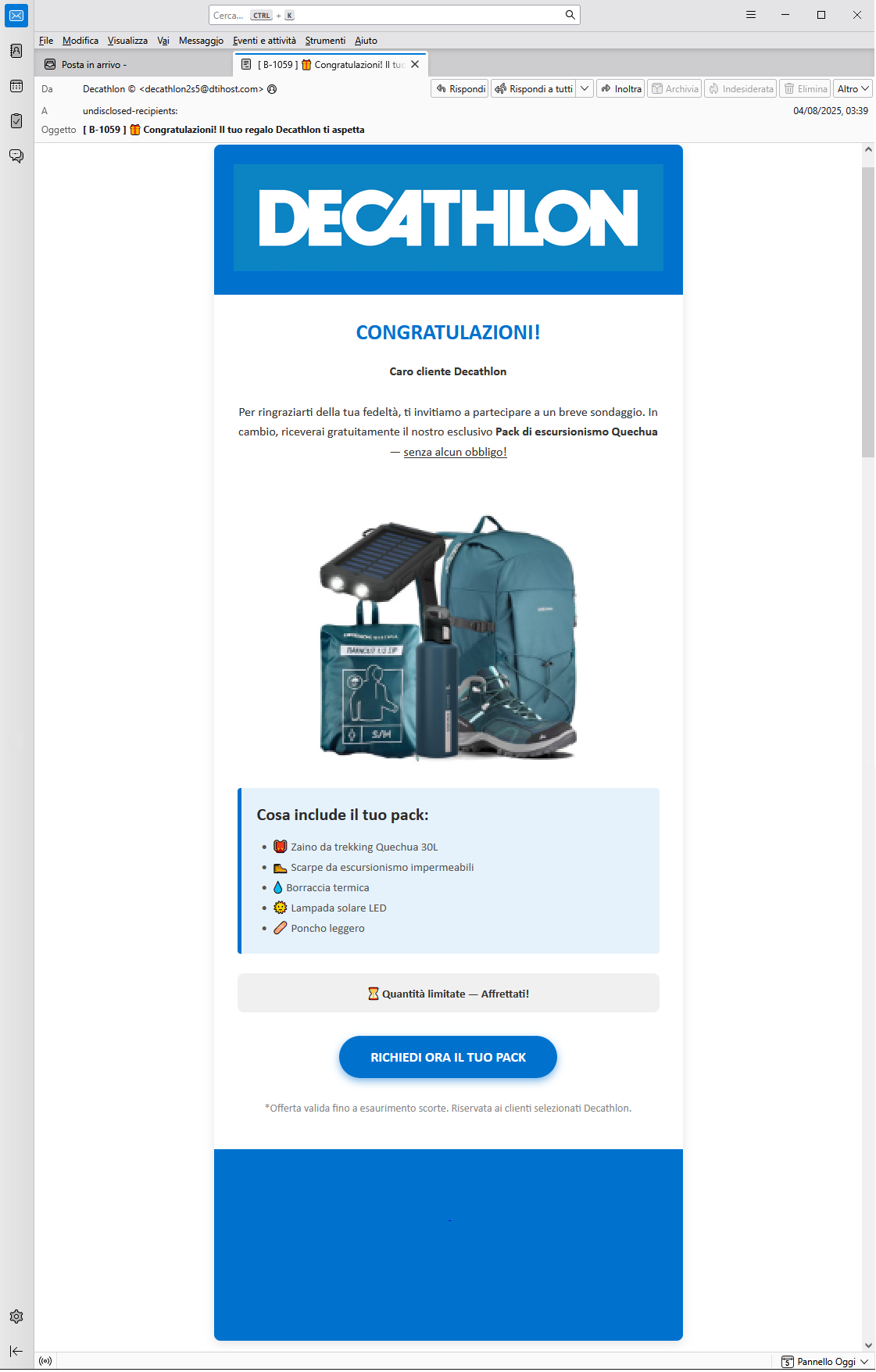
In the second example shown, a <Pallet Temu> is offered as a prize, seemingly from the well-known e-commerce platform TEMU, which can supposedly be obtained again by participating in a short survey..
The brands exploited in these campaigns are clearly unrelated to the mass sending of these malicious e-mails, which are outright scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
In the two examples above the emails clearly come from addresses <
decathlon2s5[at]dtihost[dot]com> and <
maclovio[dot]cantu[at]nuevoleon[dot]gob[dot]mx> unrelated to the official domain of
Decathlon or
TEMU. This is definitely anomalous and should certainly make us suspicious.
When we click on the links in the e-mail, we are directed to a landing page that may look graphically deceptive (with misleading images and the brand's authentic logo), but is hosted on an abnormal address/domain that is not trustworthy or traceable to the exploited brand.
The cybercriminals behind the scam, in order to achieve their goal, use various tricks, such as reporting false testimonials from customers who have won the prize. They try to persuade the user to complete the survey quickly, by making him/her believe that only a few can win, and that the offer expires today.
Surely if so many users were lucky why not try our luck?
When the survey is completed, the user is usually sent to a page for the entry of the shipping address and subsequent payment of shipping costs.
The cybercriminals' purpose, is to induce the victim to enter his/her personal information to ship the prize and then, likely, also the credit card information to pay the shipping costs.
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is stolen by cyber crooks who can use it at will.
04 August 2025 ==> Phishing Aruba - Expired domain
SUBJECT: <
Last notice for renewal of your domain>
Phishing attempts, pretending to be communications from the
Aruba brand, continue.
The message informs the recipient that his/her domain hosted on
Aruba has expired. It then informs him/her that in order to avoid service interruptions, he/she can immediately renew the domain at a cost of
€ 5.99 via the following link:
Renew Now
Let's always be careful about requests to enter personal credentials via suspicious links sent by email. Clearly, the well-known web hosting, email and domain registration company
Aruba is not involved in sending these mass emails, which are genuine scams whose aim, as always, is to steal sensitive data from unsuspecting recipients.
We immediately see that the email address of the message <
spa-hosting3[at]lopanner[dot]it> does not belong to the official official domain of
Aruba. This is definitely unusual and should make us suspicious.
To induce the victim to act quickly, the cybercriminal gives him or her little time to respond. This technique is clearly intended to intimidate the user, who, fearing that he or she will be unable to access his or her account and use the services linked to it, is prompted to act without paying due attention.
Anyone who unluckily clicks on the link, will be redirected to an anomalous WEB page, which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for criminal purposes.
04 August 2025 ==> Phishing ING Direct Bank
SUBJECT: <
ING account security: verify your telephone number>
We find again this month the phishing campaign that spreads through an e-mail exploiting stolen graphics or similar to the graphics of a well-known national banking institution. Hence it tries to pass itself off as an official communication, in order to induce the unsuspecting recipient to do what requested, and fall into a social engineering trap.
The message says to the recipient: "
the phone number associated with your ING account has not yet been confirmed. In order to ensure the security of your account, we ask you to confirm your number as soon as possible." It therefore invites the user to update his/her details using the following link:
Confirm telephone number
We can see right away that the alert message comes from a very suspicious e-mail address <
stafflng(at)cesaregalloni(dot)it> and contains a very generic text, even though the cybercriminal had the foresight to insert a logo resembling that of the well-known banking institution, that could mislead the user.
The intention is to get the victim to log in to his or her banking app under the excuse of updating the phone number.
Anyone who unluckily clicks on the
Confirm telephone number ink,ill be redirected to an anomalous WEB page, which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for criminal purposes.
1 August 2025 ==> Phishing EuroPages
«SUBJECT: <Thomas Muller sent you a request concerning your product listed on europages>
This month, we find the following phishing attempt that comes from a fake
EuroPages communication and that aims to steal the victim's account login credentials.
The message seems to come from
EuroPages, the largest international B2B sourcing platform, and notifies the user that a message has arrived concerning his product listed on EuroPages from a certain “
Thomas Muller”. It then invites the user to log in to his/her account to view the request message, via the following link:
LOG IN TO MY ACCOUNT
When we analyse the email, we see that the message comes from an email address <
info(at)clubsommozzatori(dot)it> not appear to traceable to the official
EuroPages domain. This is definitely unusual and should make us suspicious.
Anyone who unluckily clicks on the
LOG IN TO MY ACCOUNT link,ill be redirected to an anomalous WEB page, which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for criminal purposes.
5
A little bit of attention and glance can save a lot of hassles and headaches...
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on phishing techniques for more details:
01/07/2025 16:04 - Phishing: the most common credential and/or data theft attempts in July 2025.
05/06/2025 09:22 - Phishing: the most common credential and/or data theft attempts in June 2025...
05/05/2025 15:03 - Phishing: the most common credential and/or data theft attempts in May 2025...
07/04/2025 14:22 - Phishing: the most common credential and/or data theft attempts in April 2025...
07/03/2025 15:10 - Phishing: the most common credential and/or data theft attempts in March 2025..
03/02/202514:54 - Phishing: the most common credential and/or data theft attempts in February 2025...
03/01/2025 14:40 - Phishing: the most common credential and/or data theft attempts in January 2025...
03/12/2024 14:47 - Phishing: the most common credential and/or data theft attempts in December 2024...
06/11/2024 14:33 - Phishing: the most common credential and/or data theft attempts in November 2024...
07/10/2024 09:55- Phishing: the most common credential and/or data theft attempts in October 2024...
04/09/2024 09:28 - Phishing: the most common credential and/or data theft attempts in September 2024...
06/08/2024 14:50 - Phishing: most popular credential and/or data theft attempts in August 2024...
Try Vir.IT eXplorer Lite
 If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
Vir.IT eXplorer Lite has the following special features:
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- fully interoperable with other AntiVirus software and/or Internet Security products (both free and commercial) already installed on your computer. It doesn't need any uninstallation and it doesn't cause slowdowns, as some features have been appropriately reduced to ensure interoperability with the AntiVirus software already on your PC/Server. This, however, allows cross-checking through the scan;
- it identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M
- Download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
VirIT Mobile Security AntiMalware ITALIAN for ALL AndroidTM Devices
VirIT Mobile Security Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats, and empowers the user to safeguard his/her privacy with an advanced heuristic approach (Permission Analyzer).

TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can download the Lite version, which can be freely used in both private and corporate settings.
You can upgrade to the PRO version by purchasing it directly from our website=> click here to order
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities to our Research Center, that allowed us to make this information as complete as possible.
How to submit suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways:
- any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).

For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page:
How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
TG Soft Anti-Malware Research Centre (C.R.A.M.)


 This is an attempted scam by cyber criminals, with the aim of extorting a sum of money, in this case in the form of a fine. In fact, the message reads as follows:
This is an attempted scam by cyber criminals, with the aim of extorting a sum of money, in this case in the form of a fine. In fact, the message reads as follows: The message informs the recipient that the password for his/her account hosted on Aruba will expire in 24 hours. It then invites the user to confirm his/her password in order to continue using it, via the following link:
The message informs the recipient that the password for his/her account hosted on Aruba will expire in 24 hours. It then invites the user to confirm his/her password in order to continue using it, via the following link: The message, in English, informs the recipient that the Aruba servers have blocked incoming emails to his/her email account because he/she is still using outdated security settings for message management.
The message, in English, informs the recipient that the Aruba servers have blocked incoming emails to his/her email account because he/she is still using outdated security settings for message management. After completing the questionnaire, we finally arrive at a new screen that confirms the answers and allows us to try to win the prize by selecting one of the boxes displayed on the screen. We have 3 attempts, and on the second attempt we succeeded! We are then redirected to the screen on the side where the INSTRUCTIONS on how to win the APS PadovaPass card...
After completing the questionnaire, we finally arrive at a new screen that confirms the answers and allows us to try to win the prize by selecting one of the boxes displayed on the screen. We have 3 attempts, and on the second attempt we succeeded! We are then redirected to the screen on the side where the INSTRUCTIONS on how to win the APS PadovaPass card... If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS. For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis