PHISHING INDEX
Below are the most common email phishing attempts detected by TG Soft's Anti-Malware Research Center in November 2024:
29/11/2024 =>
Mooney
26/11/2024 =>
Docusign
20/11/2024 =>
Ferrino - Vincita inattesa (Unexpected win)
14/11/2024 =>
Tigotà
12/11/2024 =>
ACI
11/11/2024 =>
Aruba - verifica dell'utente (User verification)
11/11/2024 =>
Leroy Merlin
10/11/2024 =>
Decathlon
These emails are intended to trick some unfortunate person into providing sensitive data - such as bank account information, credit card codes or personal login credentials - with all the possible, easily imaginable, consequences.
29 November 2024 ==> Phishing Mooney
SUBJECT: <
Verifica dell'account>
(Account verification)
We analyze below a phishing attempt pretending to be a communication from
Mooney, a well-known Italian Proximity Banking & Payments company.
.
The message informs the recipient that, for security reasons, it is necessary to confirm his or her personal information. Therefore he/she has to confirm or update his/her data within the next 2 days.
The user is then invited to use the following link:
Conferma della vostra identità (Confirmation of your identity)
Clearly, the well-known Italian online payment company
Mooney, is unrelated to the mass sending of these emails, which are real scams whose goal remains, as always, to steal the sensitive data of the unsuspecting recipient.
Although the cyber scammer used graphics similar to or stolen from
Mooney's, and had the foresight to enter the real company's data so as to fool an unwary user, we should always exercise caution before clicking on suspicious links.
In fact, when we analyze the message, we see that the sender's e-mail address cannot be traced back to
Mooney's official domain. Another abnormal feature is the request to update the data by entering the account credentials through a link provided by e-mail.
Anyone who unluckily clicks on the
Conferma della vostra identità (Confirmation of your identity) link, will be redirected to an anomalous WEB page unrelated to
Mooney's official website.
On this page the user is asked to log in to his or her restricted area by entering his or her account login and password.
Although the site may be misleading because of the graphics similar to
Mooney's, the url address is anomalous and not traceable to the official domain of the company.
Therefore, we urge you to always pay close attention, even to the smallest details, and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber crooks.
26 November 2024 ==> Phishing Docusign
SUBJECT: <
Review Document : Kindly Sign : filename PaymentInstructions-EFT - 11/26/2024 4:42:23 p.m. Contact ->
We analyze below a new phishing attempt aimed at stealing the account login credentials of
Docusign, the American software company that provides electronic signature products.
The message, in English, ask the recipient to access his/her account to digitally sign a new document. It then invites him/her to download the document for viewing and signing through the following link:
View in DocuSign
When we analyze the email we notice that the message comes from an email address <
dse_NA2(at)docusign(dot)net> that could be misleading but is not from the domain of
Docusign. This is definitely anomalous and should, at the very least, make us suspicious..
Anyone who unluckily clicks on the View in DocuSign will be presented with the screen shown in the side image.
As we can see we are redirected to a site unrelated to Docusign, but which graphically simulates the Microsoft account login page. This is definitely anomalous.
Based on these considerations, we point out that you should NEVER enter your credentials on sites whose origin you do not know, as they will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
20 November 2024 ==> Phishing Ferrino - Vincita inattesa (Unexpected win)
SUBJECT: <
A gi sc i o ra: P o sti li mit a t i pe r u n ri sp ar m io e s c l u s i vo !>
(A c t n o w: Li m it ed p lac es fo r e x clu si ve sa vin gs)
Below we analyze the following scam attempt, hidden behind a false communication from
FERRINO, an Italian mountain equipment and clothing company.
It is a promotional message that seems to offer an unmissable opportunity. The lucky user has been selected to participate in a loyalty program, through a survey that will allow him/her to win a prize:
Outdoor adventure package - 12-piece set...or so it seems.
Certainly this phishing is a real decoy for many inexperienced users
Clearly
FERRINO is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
When we analyze the email, we notice that the message comes from an email address <
info[at]bbc[dot]co[dot]uk> not traceable to the official domain of
FERRINO. This is definitely anomalous and should, at the very least, make us suspicious. However, if we go ahead and click on the link provided, here is what happens:
we are redirected to a landing page that, although graphically well designed (with misleading images and the authentic logo of
FERRINO) does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on the following anomalous address/domain:
[FakeDomainName*]...
*
FakeDomainName is a domain that simulates a known brand domain or is a randomly named domain.
which has no connection with
FERRINO.
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey by making him/her believe that only few people can win, and offer expires in the day. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
When we click on
INIZIA IL SONDAGGIO (START THE SURVEY), we are taken to the next screens, where we are asked to answer 8 questions.
Here is specifically question 1/8. These questions are very general, focused on the degree of satisfaction with the services offered by
FERRINO, and on the daily habits of consumers. Here, too, there is a countdown to prompt the user to quickly finish the process for the award.
When the survey is over we can finally claim our prize: Outdoor adventure package - 12-piece set that would be worth 499,22 Euros but costs us 0.
We only have to pay shipping costs, which are supposed to be small.
But let's hurry. There seem to be only 2 left in stock.
Here we go: in fact, all you need to do is to enter your shipping address and pay the shipping cost, and in 5-7 business days the prize will be delivered.
To give more credibility, many comments from customers who supposedly participated in the survey, have been reported. These are all confirming testimonials/feedback about the actual delivery of the winnings, ensuring that it is not really a scam...
Surely if so many users were lucky why not try our luck?
Then, when we click on
Continua (Continue), we are sent to a further page to enter our shipping address and pay shipping costs.
WEBSITE/PAGE. As we can see from the side image, the purpose of cyber criminals is to induce the victim to enter his/her sensitive data. Therefore the user, to complete the purchase, will be asked to enter his/her credit card data to pay shipping costs, though modest,
The page where the victim is redirected, to enter his/her personal data, is hosted on an abnormal address/domain, which we report below:
[FakeDomainName*]
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, in this way your most valuable data is stolen by cyber crooks, who can use it at will.
14 November 2024 ==> Phishing Tigotà
SUBJECT: <
Offerta esclusiva: Kit Medicare gratuito per te!>
(Exclusive offer: free Medicare kit for you)
Below we analyze the following scam attempt, hidden behind a false communication from the well-known cosmetics and home care company
TIGOTA'.
It is a promotional message that, using images, tries to catch the user's interest to offer him/her an unmissable opportunity. The lucky user has in fact been selected to participate in a free loyalty program, through a survey that will allow him to win a prize: a MEDICARE KIT ...or at least so it seems.
Certainly this phishing is a real decoy for many inexperienced users.
Clearly TIGOTA' is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
When we analyze the email, we notice that the message comes from an email address <
nancy_sulik_j97585[at]saat[dot]bdwikileaks[dot]com> not traceable to the official domain of
TIGOTA'. This is definitely anomalous and should, at the very least, make us suspicious.. However, if we go ahead and click on the link provided here is what happens:
we are redirected to a landing page that, although graphically well designed (with misleading images and the authentic logo of
TIGOTA') does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on the following anomalous address/domain:
[FakeDomainName*]...
*
FakeDomainName is a domain that simulates a known brand domain or is a randomly named domain.
which has no connection with
TIGOTA'.
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey by making himbelieve that only few people can win, and that the offer expires in the day. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
When we click on
INIZIA IL SONDAGGIO (START THE SURVEY), we are taken to the next screens, where we are asked to answer 8 questions.
Here is specifically question 1/8. These are very general questions focused on the degree of satisfaction with the services offered by
TIGOTA', and on the daily habits of consumers. Here, too, there is a countdown to prompt the user to quickly finish the process for the award.
When the survey is over we can finally claim our prize: a MEDICARE KIT that would be worth 129,99 Euros but costs us 0.
We only have to pay shipping costs, which are supposed to be small.
But let's hurry. There seem to be only 2 left in stock.
Here we go: in fact, all you need to do is to enter your shipping address and pay the shipping cost, and in 5-7 business days the prize will be delivered.
To give more credibility, many comments from customers who supposedly participated in the survey, have been reported. These are all confirming testimonials/feedback about the actual delivery of the winnings, ensuring that it is not really a scam.....
Surely if so many users were lucky why not try our luck?
Then, when we click on
Continua (Continue), we are sent to a further page to enter our shipping address and pay shipping costs.
As we can see from the side image, the purpose of the cyber criminals is to induce the victim to enter his/her sensitive data to ship the prize.
The page requesting the user's personal data, is hosted on a new abnormal address/domain:
[FakeDomainName*]
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, in this way your most valuable data is stolen by cyber crooks who can use it at will.
12 November 2024 ==> Phishing ACI
SUBJECT: <
S i p r e g a d i co n f e r ma r e la ri ce v u ta >
(P l e a s e c o n f i r m r e c e i p t)
Below we analyze the following new scam attempt, hidden behind a false communication from
ACI (The Automobile Club of Italy).
It is a promotional message that seems to propose an unmissable opportunity. The lucky user has been selected by
ACI to participate in a survey offering a prize: an
emergency car kit...or so it seems.
Certainly this phishing is a real decoy for many inexperienced users.
Clearly
ACI is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient. So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
When we analyze the email, we notice that the message comes from an email address <
ticket[at]ticket[dot]com> not traceable to the official domain of
ACI. This is definitely anomalous and should, at the very least, make us suspicious. However, if we go ahead and click on the link provided, here is what happens:
we are redirected to a landing page that, although graphically well designed (with misleading images and the authentic logo of
ACI) does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on the following anomalous address/domain:
"https[:]//[FakeDomainName*]...''
which has no connection with
ACI.
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey, by making him/her believe that only few people can win and that the gifts are running out. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
When we click on
INIZIA IL SONDAGGIO (START THE SURVEY), we are taken to the next screens, where we are asked to answer 8 questions.
Here is specifically question 1/8. These are very general questions focused on the degree of satisfaction with the services offered by
ACI and on the daily habits of consumers. Here, too, there is a countdown to prompt the user to quickly finish the procedure for the award.
When the survey is over, we can finally claim our prize: an emergency car kit that would be worth 99.95 Euros but costs us 0. We only have to pay for shipping costs..which we assume are small.
But let's hurry.. there seems to be only 2 left in stock.
''Congratulazioni! Abbiamo riservato (1) kit di emergenza per auto esclusivamente per te.''
(Congratulations! We have reserved (1) emergency car kit exclusively for you.)
Here we go: in fact, all you need to do is to enter your shipping address and pay the shipping cost, and in 5-7 business days the prize will be delivered.
To give more credibility, many comments from customers who supposedly participated in the survey, have been reported. These are all confirming testimonials/feedback about the actual delivery of the winnings, ensuring that it is not really a scam.....
Surely if so many users were lucky why not try our luck?
Then, when we click on
Continua (Continue), we are redirected to a further page to enter our shipping address and pay shipping costs
The page hosting the data entry form, however, has already been reported as a DECEPTIVE WEBSITE/ PAGE..... Since the purpose of cyber criminals is to induce the victim to enter his/her sensitive data, we expect a request to enter credit card information for shipping charges, although modest.
The page shown for the entry of our personal data is hosted on a different but still suspicious address/domain:
"https[:]//[FakeDomainName*]...''
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is placed in the hands of cyber crooks, who can use it at will.
11 November 2024 ==> Phishing Aruba - Verifica dell'utente (User verification)
SUBJECT: <
Verifica della proprietà_(*****) 11/11/2024 7:39:04 a.m.>
(Property verification _(*****) 11/11/2024 7:39:04 a.m.)
We find below another phishing attempt that pretends to be a communication from the
Aruba brand
.
The message warns the recipient that checks are being carried out on active e-mail boxes on
Aruba. The user is then asked to verify that the indicated mailbox is still active and belongs to him/her. If no response is received within 72 hours, the account will be deactivated. The following link is provided for verification:
Verifica della proprietà (Property verification)
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba, is uninvolved in the mass sending of these e-mails, which are real scams whose objective remains, as always, to steal sensitive data of the unsuspecting recipient.
When we analyse the text of the message, we immediately notice that the sender's e-mail address <
noreply[at]arubq[dot]it> is not from
Aruba's official domain.
Anyone who unluckily clicks on the link will be redirected to the displayed page.
On this page, the user is invited to access his/her customer area by entering his/her login and password, and confirm his/her data, to avoid the blocking of the account and related services.
Although the site may be misleading due to the well-known logo of
Aruba, the url address in the browser bar is anomalous and not traceable to the company's official domain:
https[:]//[FakeDomainName*].com/vvxcvbsg/...
If you enter our data into counterfeit websites, it will be delivered to the cyber-criminals behind the scam, who can use it for malicious purposes. Although you may be prompted by haste and fear of mailbox suspension, to complete the task quickly, we always urge you to pay close attention to every detail, even trivial ones.
11 November 2024 ==> Phishing Leroy Merlin
SUBJECT: <
H a iv i nt o un C a rr el lo Po rt aut e ns ili D e W A LT>
(Y o u w o n a t o o l c a r t D e W A LT)
Below we analyze the following scam attempt, hidden behind a false communication from
Leroy Merlin, the well-known large distribution company.
This is a promotional message that seems to propose an unmissable opportunity. The lucky user has been selected to participate in a free loyalty program through a survey that will allow him or her to win a prize: a brand new
Tool Trolley with drawer DeWALT… or so it seems.
Certainly this phishing is a real decoy for many inexperienced users.
Leroy Merlin is clearly uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient. So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
When we analyze the email, we notice that the message comes from an email address <
info[at]bbc[dot]co[dot]uk> not traceable to the official domain of
Leroy Merlin. This is definitely anomalous and should, at the very least, make us suspicious. However, if we go ahead and click on the link provided, here is what happens:
we are redirected to a landing page that, although graphically well designed (with misleading images and the authentic logo of
Leroy Merlin) does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on the following anomalous address/domain:
[FakeDomainName*]...
*
FakeDomainName is a domain that simulates a known brand domain or is a randomly named domain.
which has no connection with
Leroy Merlin.
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey, by making him/her believe that only few people can win, and the offer expires in the day. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
When we click on
INIZIA IL SONDAGGIO (START THE SURVEY), we are taken to the next screens, where we are asked to answer 8 questions.
Here is specifically question 1/8. These are very general questions focused on the degree of satisfaction with the services offered by
Leroy Merlin and on the daily habits of consumers. Here, too, there is a countdown to prompt the user to quickly finish the process for the award.
When the survey is over we can finally claim our prize: a brand new Tool Trolley with drawer DeWALT that would be worth 669,00 Euros but costs us 0. We only have to pay shipping costs, which are supposed to be small.
But let's hurry. There seem to be only 2 left in stock.
Here we go: in fact, all you need to do is to enter your shipping address and pay the shipping cost, and in 5-7 business days the prize will be delivered.
To give more credibility, many comments from customers who supposedly participated in the survey, have been reported. These are all confirming testimonials/feedback about the actual delivery of the winnings, ensuring that it is not a scam.
Surely if so many users were lucky why not try our luck?
Then, when we click on
Continua (Continue), we are redirected to a further page to enter our shipping address and pay shipping costs.
As we can see from the image on the side, the cybercriminals try to trick the victim into entering his/her personal data to ship the prize. Most likely, credit card information will also be requested later for the payment of shipping costs.
The page where we are redirected, to enter our personal data, is hosted on a new abnormal address/domain, which we report below:
[FakeDomainName*]
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links which may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data can be stolen by cyber crooks, who can use it at will.
10 November 2024 ==> Phishing Decathlon
Below we analyze the following scam attempt, hidden behind a false communication from the well-known company
Decathlon, which spreads massively through social networks.
These ''unmissable promotions'' are now very common. The following is an example from the month of November, which aims to brag about an unmissable occasion.
''...Chiunque può ottenere uno zaino The North Face Borealis Classic al prezzo speciale di €2!
Tutto quello che devi fare è andare sul sito [NomeDominioFake*].site e rispondere a qualche semplice domanda…''
(...Anyone can get a The North Face Borealis Classic backpack for the special price of €2!
All you have to do is go to [NameFakeName*].site and answer a few simple questions...)
The first step to obtain a gorgeous The North Face Borealis Classic backpack seems the participation in a quick and easy survey, answering only 3 questions....or at least so it seems.
Certainly this phishing is a real decoy for many inexperienced users.
Clearly the well-known company
Decathlon is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
To give more credibility, many comments from customers who supposedly participated in the survey, have been reported. These are all confirming testimonials/feedback about the actual delivery of the winnings, ensuring that it is not a scam.
Surely if so many users were lucky why not try our luck?
We then try to click on the link, this is what happens:
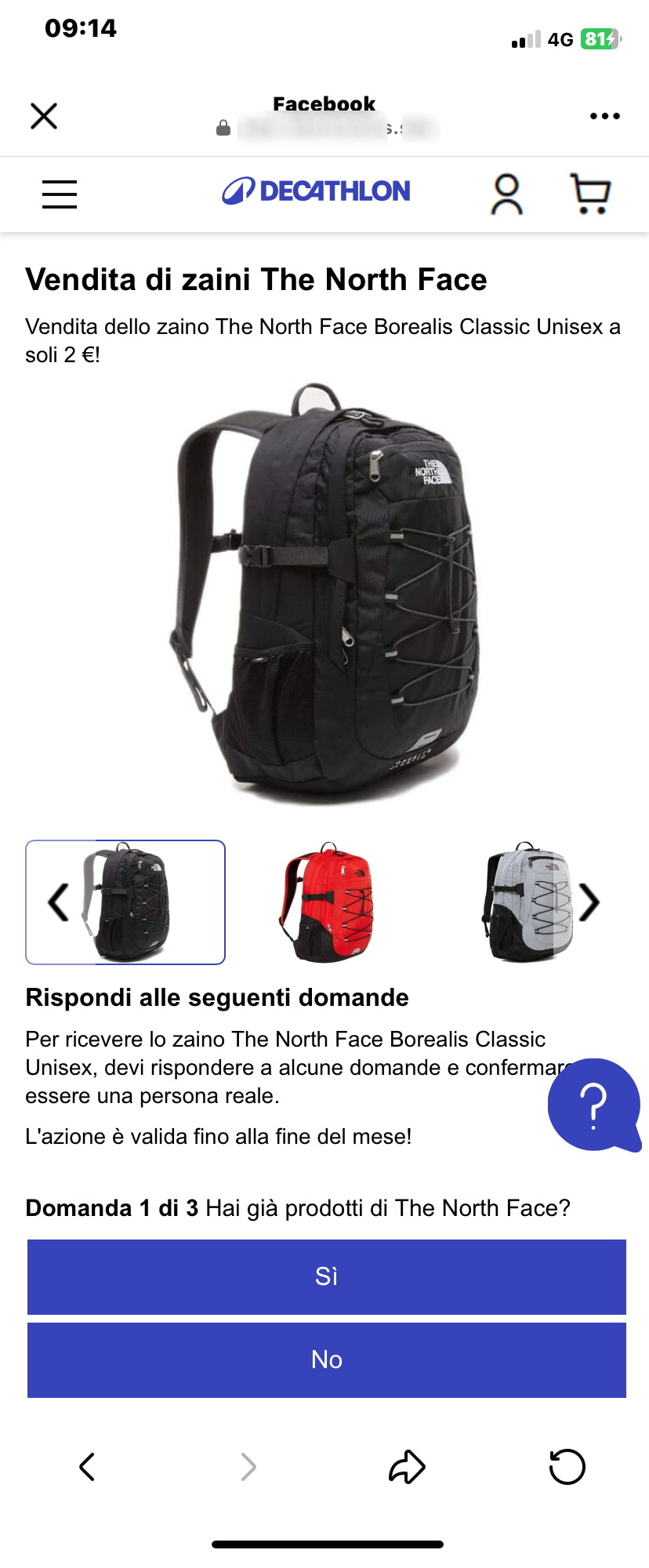
we are redirected to a landing page that, although graphically well done, with misleading images, does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on the following abnormal address/domain:
*
FakeDomainName is a domain that simulates a known brand domain or is a randomly named domain.
which has no connection with
Decathlon.
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey, by making him/her believe that only few people can win, and the gifts are running out.
After answering the 3 generic survey questions., we are presented with a simple little game to try our luck:
we have 3 attempts to find the prize inside some gift packages..
We are really lucky.
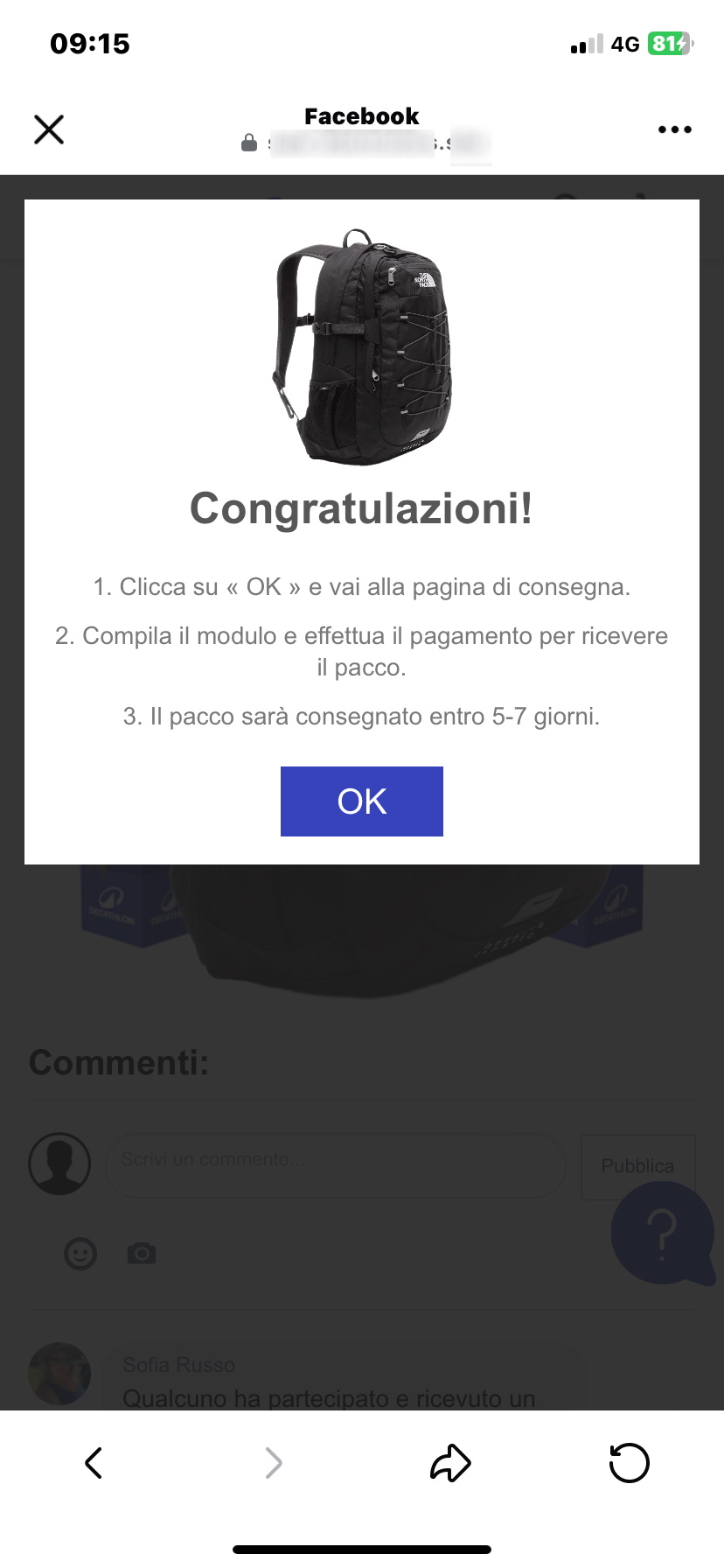
After 2 attempts we made it: we managed to get the award.
But it is not over yet.
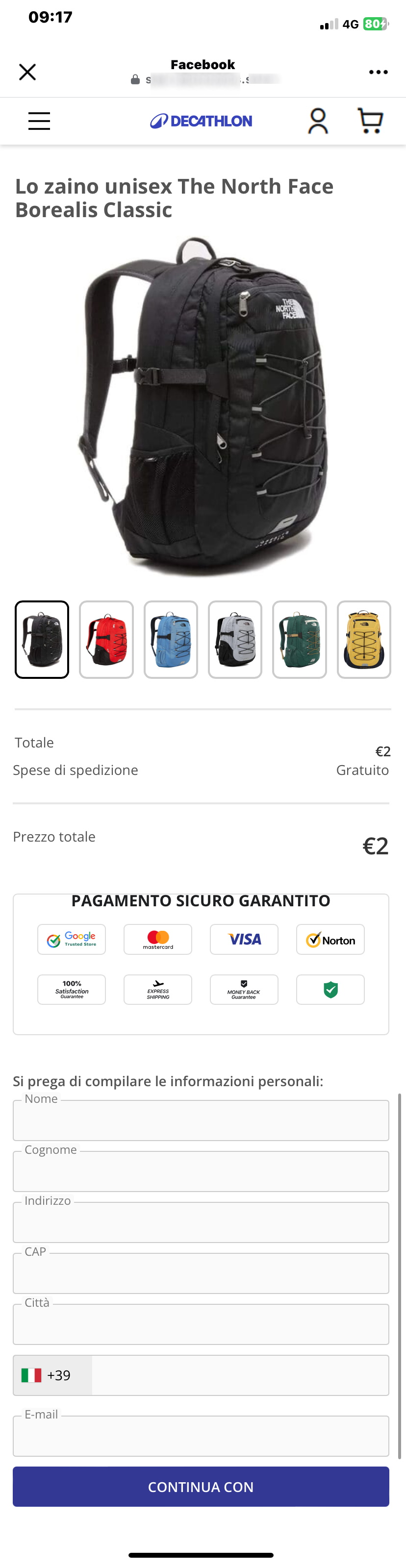
As highlighted in the picture, the winning is conditional on paying 2€ Euros although the shipping costs seem to be zero.
The goal of cybercriminals is to trick the victim into entering his/her sensitive credit card data. These are in fact necessary to pay the required 2 euros.
The page requesting the user's personal information is hosted on a different address/domain from the previous one, but still suspicious:
[FakeDomainName*].com
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is delivered to cyber crooks, who can use it at will.
A little bit of attention and glance can save a lot of hassles and headaches...
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on phishing techniques for more details:
06/11/2024 14:33
- Phishing: the most common credential and/or data theft attempts in October 2024...
04/09/2024 09:28 - Phishing: the most common credential and/or data theft attempts in September 2024
06/08/2024 14:50 - Phishing: most popular credential and/or data theft attempts in August 2024...
04/07/2024 17:22 - Phishing: the most common credential and/or data theft attempts in July 2024.
03/06/2024 17:22 - Phishing: the most common credential and/or data theft attempts in June 2024..
03/05/2024 11:56 - Phishing: the most common credential and/or data theft attempts in May 2024..
03/04/2024 10:23 - Phishing: the most common credential and/or data theft attempts in April 2024...
04/03/2024 10:42 - Phishing: the most common credential and/or data theft attempts in March 2024..
06/02/2024 08:55 - Phishing: the most common credential and/or data theft attempts in February 2024...
02/01/2024 16:04 - Phishing: the most common credential and/or data theft attempts in January 2024....
11/12/2023 09:39 - Phishing: the most common credential and/or data theft attempts in December 2023...
03/11/2023 08:58 - Phishing: the most common credential and/or data theft attempts in November 2023....
03/10/2023 16:35 - Phishing: the most common credential and/or data theft attempts in October 2023....
05/09/2023 10:35 - Phishing: the most common credential and/or data theft attempts in September 2023...
Try Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
Vir.IT eXplorer Lite has the following special features:
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- fully interoperable with other AntiVirus software and/or Internet Security products (both free and commercial) already installed on your computer. It doesn't need any uninstallation and it doesn't cause slowdowns, as some features have been appropriately reduced to ensure interoperability with the AntiVirus software already on your PC/Server. This, however, allows cross-checking through the scan;
- it identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M
- Download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
VirIT Mobile Security AntiMalware ITALIAN for ALL AndroidTM Devices
VirIT Mobile Security Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats, and empowers the user to safeguard their privacy with an advanced heuristic approach (Permission Analyzer).

TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can download the Lite version, which can be freely used in both private and corporate settings.
You can upgrade to the PRO version by purchasing it directly from our website=> click here to order
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities to our Research Center, that allowed us to make this information as complete as possible.
How to submit suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways:
- any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
 For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
TG Soft's C.R.A.M. (Anti-Malware Research Center)


 we are redirected to a landing page that, although graphically well done, with misleading images, does not seem trustworthy at all.
we are redirected to a landing page that, although graphically well done, with misleading images, does not seem trustworthy at all.

 For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis