These emails are intended to trick some unfortunate person into providing sensitive data - such as bank account information, credit card codes or personal login credentials - with all the possible, easily imaginable, consequences.
29 January 2025 ==> Phishing Docusign
SUBJECT: <
dahsboard update attached—please save or print now>
We analyze below a new phishing attempt aimed at stealing the account login credentials of
Docusign, the American software company that provides electronic signature.
The message, in English, informs the recipient that there is a pending update awaiting review and confirmation. It then invites him/her to log in by clicking on the following link:
Click View
When we analyze the email, we see that the message comes from an email address <
info[at]fdtrust[dot]org> not traceable to the domain of
Docusign. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the
Click View link, will be confronted with the screen shown in the side image.
As we can see we are redirected to a site unrelated to
Docusign but which graphically simulates the account login page of Microsoft. This is definitely anomalous.
The goal of the scammers is to induce us to enter, specifically, the mailbox password.
Given these considerations, we urge you to NEVER enter your credentials on unknown sites, as they will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
28 January 2025 ==> Phishing Account Posta Elettronica (Phishing Email Account )
SUBJECT:<
Dominio.it 5 Incomplete Messαges Delivery Stαtus>
We analyze below a new phishing attempt that aims to steal the login credentials of the email account.
The message, of dubious origin, informs the recipient that some messages have not been delivered to his/her mailbox, due to a server problem.
It seems therefore necessary to click on one of the two links:
Receive all 5 emails
Delete all 5 emails
When we analyze the email, which is very sparse and without provenance information, we notice that the message comes from an anomalous email address <
admin[t]conversion[-]crafters[dot]com>. This should already make us suspicious.
The purpose of the message is to prompt the recipient to click on the Receive all 5 emails
Delete all 5 emails link, which, we would like to point out, redirects to an abnormal page intended to steal the password of the e-mail account but which has already been reported as a deceptive WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data, in order to use it for illegal purposes.
Given these considerations, we urge you to NEVER enter your credentials on sites whose origin is unknown, as they will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
28 January 2025 ==> Phishing Shein
SUBJECT: <
S co p ri la t ua Sca to la Mi s teri osa S hei n o gg i! >
(D isco ver y our S hei n My ster y B o x to da y)
Below we analyze a scam attemp, hiddent behind a false communication from the well-known company
SHEIN.
It is a promotional message proposing an opportunity to win a prize. The lucky user has been selected to participate in a survey to win Shein's mystery box...or so it seems.
Certainly for many inexperienced users behind this phishing there is a real decoy.
The well-known Chinese online sales site
SHEIN is clearly uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as usual, to steal sensitive data of the unsuspecting recipient.
So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
When we analyze the email, we see that the message comes from an email address <
patricia[_]shaw[_]v26476[at]samartc[dot]pitrom[dot]store> not traceable to the official site of
SHEIN. This is definitely anomalous and should, at the very least, make us suspicious. However, if we go ahead and click on the link
Completa il sondaggio adesso (Complete the survey now) link, here is what happens:
we are redirected to a landing page that, although graphically well crafted (with misleading images and the authentic logo of
SHEIN), does not seem trustworthy at all.
In fact, the survey is hosted on the following anomalous address/domain..
https[:]//[FakeDomainName*]....
which has no connection with
SHEIN.
The cybercriminals running the scam, in order to induce the user to quickly end the survey and obtain his/her sensitive data, pretend that the offer is about to expire. At the bottom of the screen there is also a countdown timer, which however, if reset to zero as simulated, would restart immediately thereafter.. rather strange thing.
If we click on
INIZIA IL SONDAGGIO (START THE SURVEY), we are taken to the next screens, where we are asked to answer 8 questions.
Here specifically is question 1/8. These are, in fact, all very general questions focusing on the degree of satisfaction with the
SHEIN shopping site and the products sold. The countdown timer is also present here, to prompt the user to quickly complete the process for the award.
After the survey is completed we can finally claim our prize: Shein's Mystery Box which would be worth Euro 399.99 but costs us 0..We only have to pay shipping costs, which are supposed to be small.
Better hurry up and finish the procedure.
To give greater credibility, many comments from customers who appear to have already participated in the survey, have also been reported. These are all reassuring testimonials/feedback about the actual delivery of the winnings and therefore about the trustfulness of the message. Some of them are even documented with photos of the prize received.
If so many users were lucky why not try to claim the delivery?!
Just enter your shipping address and pay the shipping costs to receive the prize in 5-7 working days.....
Then we will be sent to a further page, as shown in the image below, to enter our shipping address and pay the shipping charges.
The page, hosting the data-entry form, looks graphically well designed and misleading. In order to complete the process, we need to pay the shipping costs, which, although modest, likely involve entering credit card information in order to finish the purchase.
In fact, the purpose of cyber criminals is precisely to trick the user into entering his/her sensitive data and, in this case, his/her credit card data!
The page that asks for our personal information, is hosted on a new abnormal address/domain.
https[:]//[FakeDomainName*]....
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links which may lead to a counterfeit site. In fact, in this way your most valuable data is stolen by cyber crooks who can use it at will.
21 - 26 January 2025 ==> Phishing TELEPASS
Below we analyze the attempted scams hidden behind false communications by the well-known Italian company
TELEPASS , that works in the urban and suburban mobility services industry.
These are 2 examples, graphically and textually different but with the same goal of making the recipient believe that he or she is facing an unmissable opportunity.The lucky user has been selected as winner of a fantastic prize: a new "
car emergency kit", which can be claimed by participating in a a short survey.
Example no. 1
SUBJECT: <Abbiamo una sorpresa per i clienti Telepass>
(We have a surprise for Telepass customers)
Example no. 2
SUBJECT: <N o n as p e tt a r e! Ri sp o n di e r ic evi il K it d i E me rg e nz a ora!>
(Don’t wait! Reply and get the Emergency Kit now)
Certainly this phishing is a real decoy for many inexperienced users.
Clearly the well-known company
TELEPASS is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
When we analyze the emails, we see that the messages come from email addresses <
Telepass[-]nqe[at]stanbertoffers[dot]click> and <
roxanne[_]pigman[_]r33621[at]samartc[dot]pitrom[dot]store> clearly not traceable to the official domain of
TELEPASS. This is definitely anomalous and should, at the very least, make us suspicious. However, if we go ahead and click on the links in the emails, here is what happens:
we are redirected to a landing page that, although graphically well designed (with misleading images and the authentic logo of
TELEPASS) does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on the following anomalous address/domain:
https[:]//[NomeDominioFake*]....
which has no connection with
TELEPASS.
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey, by making him/her believe that only few people can win, and the offer expires in the day. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
When we click on
INIZIA IL SONDAGGIO (START THE SURVEY), we are taken to the next screens, where we are asked to answer 8 questions.
Here is specifically question 1/8. These are very general questions focused on the degree of satisfaction with the services offered by
TELEPASS and about the company's marketing/promotional choices. Here, too, there is a countdown to prompt the user to quickly finish the process for the award.
When the survey is over, we can finally claim our prize: a Car emergency kit that would be worth 99,95 Euros but costs us 0 Euros. We only have to pay shipping costs, which are supposed to be small.
But let's hurry. There seem to be only 2 left in stock.
Just enter your shipping address and pay the shipping costs to receive the prize in 5-7 working days.
To give more credibility, many comments from customers who supposedly participated in the survey, have been reported. These are all confirming testimonials/feedback about the actual delivery of the winnings, ensuring that it is not really a scam.....
Surely if so many users were lucky why not try our luck?!
Then, when we click on
Continua (Continue), we are sent to a further page to enter our shipping address and pay shipping costs.
As we can see from the image on the side, the cybercriminals try to trick the victim into entering his/her sensitive data, to ship the prize. Most likely, credit card information will also be requested later for the payment of shipping costs.
The page where we are redirected, to enter our personal data, is hosted on a new abnormal address/domain, which we report below:
https[:]//[FakeDomainName*][.]com
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links that may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is stolen by cyber crooks who can use it at will.
17 January 2025==> Phishing PayPal
SUBJECT: <
Ogg etto: Imp orta nte: Limit azi oni su l tu o acc oun t – Azi one ri chies ta>
(Su bje ct: Imp orta nt: Restrictio ns on you r accoun t – Re quested ac tion)
We analyze below a new phishing attempt aimed at stealing the account login credentials of
PayPal, the well-known U.S. digital payments company.
The message informs the recipient that his/her
PayPal account has been restricted due to unauthorized use. To avoid account deactivation, the user has 24 hours to confirm the data by clicking on the link:
Conferma le tue informazioni (Confirm your information)
When we analyze the email we see that the message comes from an email address <
poi2[at]annacaiazzo[dot].it> clearly not from the official domain of
PayPal. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link.
Conferma le tue informazioni (Confirm your information) will be presented with the image shown in the side image.
As we can see, the user is redirected to a site that graphically simulates the
PayPal login page. However, the page is hosted on an anomalous address/domain.
Given these considerations, we point out that you should NEVER enter your credentials on sites whose origin is unknown, as they will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
14 January 2025==> Phishing GLS
SUBJECT: <
"Il Tuo Pacco È Pronto per la Consegna - Dettagli Richiesti">
(Your Package Is Ready For Delivery - Details Required)
We analyze below a new data theft attempt that comes through a deceptive message, pretending to be from the well-known courier company
GLS.
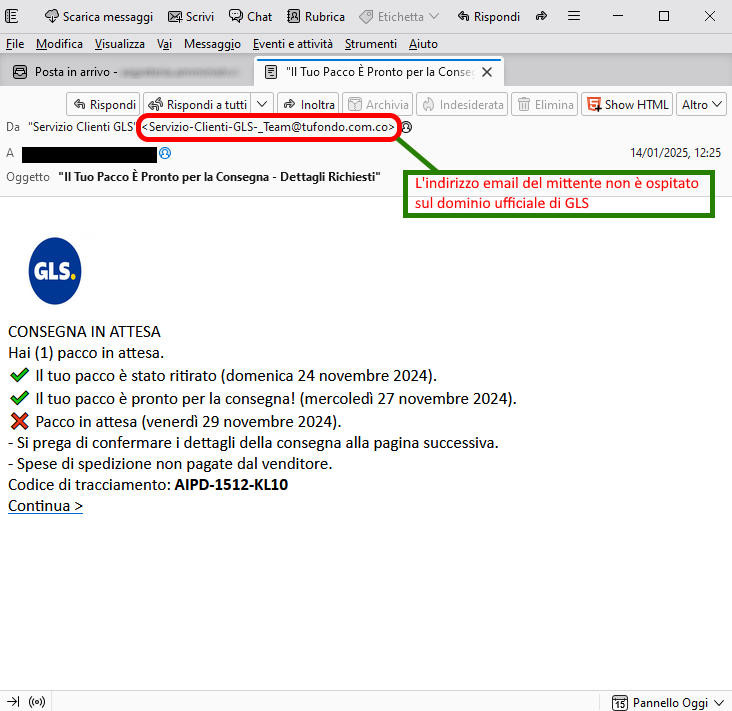
The message, which we quote on the side, refers specifically to a package awaiting delivery. To unlock the delivery, it is necessary to confirm the shipping information and pay the shipping charges not paid by the seller. The recipient is then asked to click on the
Continua (Continue) link.
The message, although seemingly from the courier
GLS, is very poor and lacking in information to identify the delivery. Only a tracking code
(AIPD-1512-KL10) is reported, which could be proven false by checking the tracking on official website of
GLS.
Clearly
GLS is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
So keep an eye out, all it takes to avoid unpleasant incidents is a little attention and a quick glance.
Anyone who unluckily clicks on the Continua (Continue) link, will be directed to a web page simulating the official website of GLS. Although the site is graphically well designed, we see that the url address is anomalous and not traceable to any courier company.
The next page shows a precise reference tracking code (AIPD-1512-KL10). Then clicking on ''Continue'', a new screen follows showing the pending shipping charges.
Moving on, we click on ''Pianifica la tua consegna ora'' (Schedule your delivery now) and a new screen is offered inviting us to choose how to arrange the new delivery, followed by an additional one where we specify when we prefer the delivery.
Here we are finally at the conclusion of the shipment rescheduling procedure, which should end with the data confirmation. However, in order for the delivery to take place, we need to pay the shipping costs
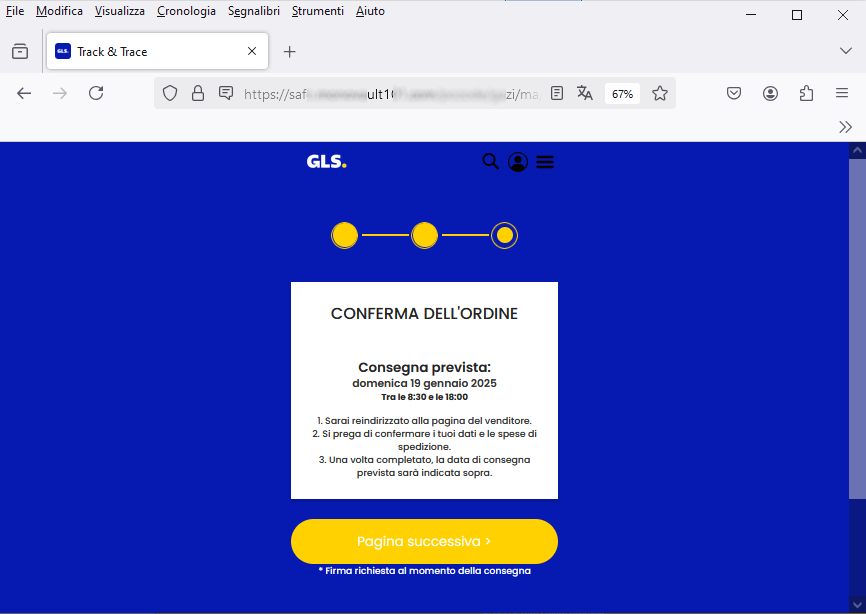
HERE'S THE SURPRISE! After clicking on 'Pagina successiva'' (Next Page) we are in fact redirected to a data-entry FORM that requires, in addition to ''Nome'', (First Name), ''Cognome'' (Last Name), '''Indirizzo'' (Address), ''Numero di telefono'' (Phone Number) and ''E-Mail'', our credit card information to proceed with the payment of € 19.95 related to shipping costs.
We point out that the form page has a different address from the address above but still is totally unreliable and unrelated to any courier site.
The purpose of this phishing is to induce the user to enter his or her personal information. On the side we show in detail the screenshot of the completion form.
To conclude, we always urge you to be wary of any email asking for confidential data, and avoid clicking on suspicious links, which may lead to a counterfeit site difficult to distinguish from the original one. In fact, if you trust these messages, your most valuable data is stolen by cyber crooks who can use it at will.
14 January 2025==> Phishing MetaMask
«SUBJECT: <
Security Notification>
We analyze below a new phishing attempt aimed at stealing the credentials of the victim's cryptocurrency wallet, run on
MetaMask, a San Francisco-based company.
MetaMask is a cryptocurrency software wallet used to interact with the Ethereum blockchain. It allows users to access their Ethereum wallet via a browser extension or mobile app.
The message prompts the recipient to activate 2-factor checking (2FA) through the following link, to increase the security of his/her wallet if he/she has not already done it.
Enable 2FA Now
When we analyze the message, we see that it comes from a very suspicious e-mail address<
zbdt7a4j[at]info[dot]mailservice[dot]com> not traceable to the official domain of
MetaMask. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the
Enable 2FA Now link, will be redirected to an anomalous WEB page, unrelated to the official site of
MetaMask.
Such a page might mislead the user as it simulates
MetaMask's graphics. However, it is hosted on an anomalous address/domain.
To conclude, we always urge you to be careful and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as it will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
10 January 2025==> Phishing ESSELUNGA
SUBJECT: <
Fai sentire la tua voce e ricevi un premio!>
(Make your voice heard and receive a prize!)
Below we analyze the following scam attempt, hidden behind a false communication from the well-known large distribution company
Esselunga.
It is a promotional message that seems to propose an unmissable opportunity. The lucky user has been selected to participate in the current promotion through a survey that will allow him/her to win a prize:
36-piece Tupperware Modular Mates set...or so it seems.
Certainly behind this phishing there is a real decoy for many inexperienced users.
Clearly
Esselunga is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient. So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
When we analyze the email, we notice that the message comes from an email address <
ticket[at]ticket[dot]com> not traceable to the official domain of
Esselunga. This is definitely anomalous and should, at the very least, make us suspicious. However, if we go ahead and click on the link provided, here is what happens:
we are redirected to a landing page that, although graphically well designed (with misleading images and the authentic logo of
Esselunga) does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on the following anomalous address/domain:
"https[:]//[FakeDomainName*]...''
which has no connection with
Esselunga.
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey, by making him believe that only few people can win, and the offer expires in the day. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
When we click on
INIZIA IL SONDAGGIO (START THE SURVEY), we are taken to the next screens, where we are asked to answer 8 questions.
Here specifically is question 1/10. These are, in fact, all very general questions focusing on the degree of satisfaction with the services offered by
Esselunga and the daily habits of consumers. We see that the countdown timer is also present here to prompt the user to quickly finish the process for the award.
When the survey is over, we can finally claim our prize: 36 Piece Tupperware Modular Set which is worth Euro 399,99 but costs us zero. We only have to pay shipping costs, which are supposed to be small.
But let's hurry.. There seems to be only 2 left in stock.
''Congratulazioni! Abbiamo riservato (1) Set Tupperware da 36 pezzi esclusivamente per te.''
(Congratulations! We have reserved (1) 36-piece Tupperware Modular Mates set exclusively for you)
Here we go: in fact, all we need to do is enter our shipping address and pay the shipping cost, and in 5-7 business days the prize will be delivered....
To make the scam more trustworthy, several comments have been reported from customers who seem to have already participated in the survey. These are all reassuring testimonials/feedback about the actual delivery of the winnings and thus on the reliability of the message.
Surely if so many users were lucky why not try our luck?!
Then, if we click on
Continua (Continue), we will be directed to another page to enter our shipping address and pay shipping costs.
As we can see from the side image, the purpose of the cyber criminals is to induce the victim to enter his/her sensitive data needed to ship the prize. Then credit card information will very probably be requested to pay the shipping costs .
The page we are redirected to, in order to enter our personal information, is hosted on a new abnormal address/domain:
"https[:]//[FakeDomainName*]...''
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links that may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is stolen by cyber crooks who can use it at will.
06 January 2025==> Phishing Account Posta Elettronica (Phishing Email Account )
SUBJECT: <
Final Notice: 01/06/2025 06:21:24 AM!>
We analyze below a new phishing attempt that aims to steal email account login credentials.
The message, of dubious origin, invites the recipient to read the attached message, a zipped .pdf document, named RecipientName-Service_installation_Quote.
When we analyze the mail, very poor and lacking information to identify its origin, we see that the message comes from an abnormal email address <
documents(at)docusign(dot)com>. This is very suspicious
In any case, anyone who unluckily tries to open the attached file, will be presented with the screen shown in the side image.
As we can see, we are redirected to a site that graphically simulates the Yahoo mail login page, where we are prompted to enter our login information (E-mail and password) in order to view the document. The page is hosted on an anomalous address/domain.
Based on these considerations, we point out that you should NEVER enter your credentials on sites whose origin you do not know, as they will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
01 - 27 January 2025 ==> Phishing Leroy Merlin
Below we analyze the following scam attempts hidden behind a false communication from
Leroy Merlin, the well-known large distribution company.
These are 2 examples, graphically and textually different, but with the same goal of making the user believe that he or she is facing an unmissable opportunity.The e-mail seems to offer the lucky user a chance to win a set of 108 Dexter tools, just by participating in a short survey.
Example no. 1
SUBJECT: <S i p r e g a d i c on fe rm a r e l a ri c ezi on e>
(P l e a s e c o n f ir m r e c e i p t)
Example no. 2
SUBJECT: <V i n c i u n s e t di ut e n s i li D ex t er: p ar t eci pa og gi ste ss o al no str o s on da gg io L er o y M erli n!>
(Wi n a s e t of D ext er t o ol s: j oi n o u r Le ro y Me rli n su rve y to da y!)
Clearly, the well-known company is unrelated to the mass sending of these e-mails, which are real scams whose goal is, as always, to steal sensitive data of the unsuspecting recipient and use them for criminal purposes.
Although the cyber crook had the graphic foresight to include the logo of the well-known chain, there are clues that should make one suspicious. In fact, the source addresses of the e-mails <
's official domain.
we are redirected to a landing page that, although graphically well designed, does not seem trustworthy at all, as it is hosted on an anomalous address/domain, unrelated to
.
The cyber criminals masterminding the scam, try to induce the user to quickly finish the survey pretending that there is little time left to participate and win the prize. In fact, at the bottom of the screen there is a countdown timer, which, however, if it resets to zero, it would start over again immediately afterward... rather strange thing.
, we are taken to the next screens, where we are asked to answer 8 questions. These are very general questions focused on the degree of satisfaction with the services offered by
and on the daily habits of consumers. Here, too, there is a countdown to prompt the user to quickly finish the process for the prize without much thought.
To make it more credible, the cyber-scammer included some fake comments from users who supposedly participated in the survey and actually received the promised prize. Obviously, the purpose is to reassure the victims that the message is not a scam and thus induce them to continue.
, a window will open notifying us that we've won the prize and how to receive it: enter the shipping address, pay the shipping cost, and in 5-7 business days the 108-piece Dexter tool set will be delivered.
, and we are redirected to another page, hosted on a fake address/domain, where we are asked to enter our personal information, such as name and shipping address. Continuing further, we will likely also be prompted to enter our credit card information to pay shipping charges.
We always urge you not to rush and pay attention to even the smallest details. Besides we invite you to be wary of offers/promotions that are "too good to be true," and above all not to enter your personal information and/or passwords on forms hosted on counterfeit web pages, as they will be used by cyber crooks for criminal purposes.


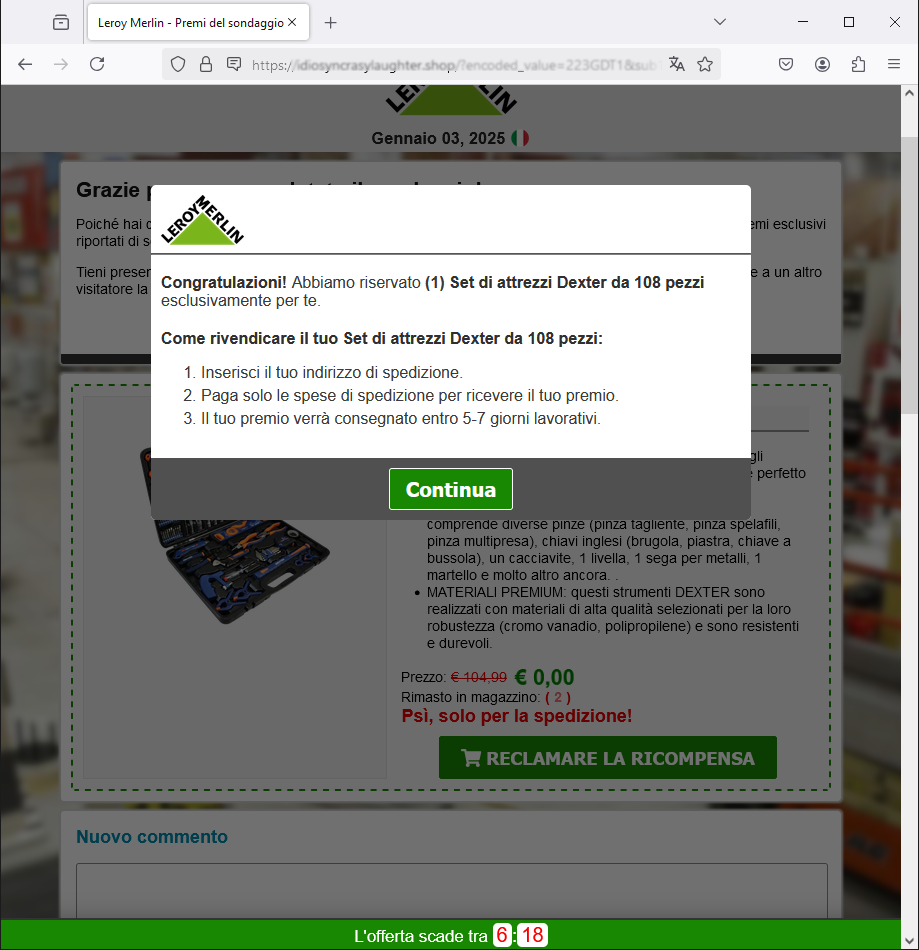 Clicking on RECLAMARE LA RICOMPENSA (CLAIM THE REWARD), a window will open notifying us that we've won the prize and how to receive it: enter the shipping address, pay the shipping cost, and in 5-7 business days the 108-piece Dexter tool set will be delivered.
Clicking on RECLAMARE LA RICOMPENSA (CLAIM THE REWARD), a window will open notifying us that we've won the prize and how to receive it: enter the shipping address, pay the shipping cost, and in 5-7 business days the 108-piece Dexter tool set will be delivered.  If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS. For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis