PHISHING INDEX
Below are the most common email phishing attempts detected by the TG Soft Anti-Malware Research Center in April 2025:
25/04/2025 =>
Netflix
25/04/2025 =>
PayPal
25/04/2025 =>
SumUp
22/04/2025 =>
Aruba - Rinnova il dominio (Renew your domain)
16/04/2025 =>
Phishing sondaggio clienti (Phishing customer survey) - LEROY MERLIN - DECATHLON
16/04/2025 =>
Aruba - Verifica Password (Password Verification)
12/04/2025 =>
Amazon PRIME
12/04/2025 =>
SexTortion
07/04/2025 =>
SCAM Polizia di Stato
05/04/2025 =>
Phishing sondaggio clienti (Phishing customer survey)- BOSCH
05/04/2025 =>
Phishing sondaggio clienti (Phishing customer survey)- CONAD - ESSELUNGA
04/04/2025 =>
Aruba - Aggiorna pagamento (Update Payment)
03/04/2025 =>
Netflix
03/04/2025 =>
Aruba - Verifica Password (Password Verification)
03/04/2025 =>
Google
01/04/2025 =>
Phishing sondaggio clienti (Phishing customer survey)- TELEPASS - LAVAZZA
These emails aim to deceive unsuspecting victims into providing sensitive information, such as bank account details, credit card codes, or personal login credentials, with all the easily imaginable consequences.
25 April 2025 ==> Phishing NETFLIX
«SUBJECT:
<Join the Netfli loyalty programx>
Let's analyze another phishing attempt that originates from a fake communication claiming to be from NETFLIX, the well-known streaming platform for movies, TV series, and other paid content. Its goal is to steal the victim's credit card information.
The message informs the user that his/her membership has expired, but as part of the loyalty programme he/she can extend the membership for 90 days FREE OF CHARGE! However, he/she needs to hurry as the offer expires soon. The following link is provided for membership extension:
Estendi GRATUITAMENTE (Extend for FREE)
When we examine the e-mail, we notice that the message comes from an e-mail address <
info(at)bci(dot)tourplannerslanka(dot)com> that cannot be traced back to the official domain of
NETFLIX. This is definitely anomalous and should, at the very least, raise our suspicions.
Anyone who unluckily clicks on the Estendi
Estendi GRATUITAMENTE (Extend for FREE) link, will be redirected to an anomalous web page.
In the side image, we see that the web page where we are redirected is graphically deceptive in that it shows the well-known
NETFLIX logo. Continuing on and clicking on
Prolunga gratuitamente (Free Extension), we are redirected to a further screen..
Here we are asked to enter our data (first name, last name and e-mail address) and to pay the sum of Euro 6.99. This is very strange, as the service extension was supposed to be free of charge.
We also observe that the access page is hosted on an abnormal address/domain.
https[:]//[NomeDominioFake*]....
If we continue, our personal and credit card data will be used by cyber crooks with all the associated, easily imaginable, risks.
25 April 2025 ==> Phishing PayPal
SUBJECT: <
Avviso di Blocco Temporaneo del Conto>
(Notice of Temporary Account Block)
We analyse below a new phishing attempt aimed at stealing the login credentials of the account of
PayPal, the well-known US digital payments company.
The message informs the recipient that, as a result of
PayPal Services Italy's new policy aimed at "maximising the security and confidentiality of their accounts", data processing methods will be extended. In order to facilitate this transition, the user is asked to update his/her information; until then, the account will remain locked. To update, users just need to click on the following link:
AGGIORNA ORA (UPDATE NOW)
When we analyse the message, we see that it comes from an email address <
ew-alerts[at]dtihost[dot].com> that is clearly not traceable to the official domain of
PayPal. This is definitely abnormal and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the
AGGIORNA ORA (UPDATE NOW) link, will be presented with the screen shown in the side image.
As we can see, we are redirected to a site that graphically simulates the
PayPal login page, but is hosted on an anomalous address/domain.
Based on these considerations, we recommend that you NEVER enter your credentials on sites whose origin you do not know, as they will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
25 April 2025 ==> Phishing SumUp
SUBJECT: <
Per motivi di sicurezza, conferma il tuo indirizzo email.>
(For security reasons, please confirm your email address)
We analyze below a new phishing attempt aimed at stealing the account login credentials of
SumUp, the London-based digital payments company.
The message asks the recipient to confirm his or her e-mail address linked to his or her
SumUp account, via the link provided, to ensure the functionality and security of his or her account.
Conferma il tuo indirizzo email (Confirm your email address)
When we examine the message we see that it comes from an email address <
mediaworld7711[at]assistenzaanzianitoscana[dot].it> that is clearly not traceable to the official domain of
SumUp. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the Conferma il tuo indirizzo email
Conferma il tuo indirizzo email (Confirm your email address) link, will be redirected to an anomalous WEB page which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for criminal purposes.
22 April 2025 ==> Phishing Aruba - Rinnova il dominio (Renew your domain)
SUBJECT: <
Importante: Scadenza dominio il 23/04/2025> (
Important: Domain expiration on 23/04/2025)
Phishing attempts pretending to be communications from the
Aruba brand continue
.
The message warns the recipient that his/her domain hosted on
Aruba will expire on
23/04/2025. It therefore informs him/her that, in order to avoid service interruptions, he/she can renew the domain through the following link:
Rinnova il mio dominio (Renew my domain)
We immediately see that the text of the e-mail is generic and does not provide any identifiers of the customer or the linked account. Furthermore,
to proceed with the renewal, the user is asked to enter his/her account credentials through a suspicious link sent via email.
Clearly, the well-known web hosting, e-mail and domain registration services company,
Aruba, is uninvolved in the mass sending of these e-mails, which are real scams whose objective remains, as always, to steal sensitive data of the unsuspecting recipient.
In order to induce the victim to act promptly, the cybercriminal allows little time to act. In this way, the user, fearing the blocking of the account and related services, is prompted to act without paying due attention.
Anyone who unluckily clicks on the
Rinnova il mio dominio (Renew my domain) link, will be redirected to a web page which, although graphically well-designed - the cybercriminal had the graphic foresight to include the Aruba logo - is not at all trustworthy. In this case too, the address/domain is anomalous and unrelated to the company's official site.
On this page, the user is invited to log in to his/her customer area by entering a login and password, in order to renew the password and avoid malfunctions/blocks.
We always urge you to be careful and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be delivered to the cyber-criminals creators of the scam, who will use them for their own purposes. In case of these cyber fraud attempts, we remind you not to be in a hurry and to pay attention to every detail, even the most trivial.
16 April 2025 ==> Phishing sondaggio clienti (Phishing customer survey): LEROY MERLIN / DECATHLON
Customer survey-themed phishing campaigns, exploiting well-known brands, continue. In the following two cases, large-scale distribution companies, particularly in the crafts, clothing, and sports equipment sectors, are concerned.
In the first reported example, the cybercriminal used the well-known brand name of
LEROY MERLIN, to launch a promotional message that would allow the user to win an exclusive prize <NEW PROFESSIONAL TOOL SET!>. To claim the prize, simply answer a few short questions.
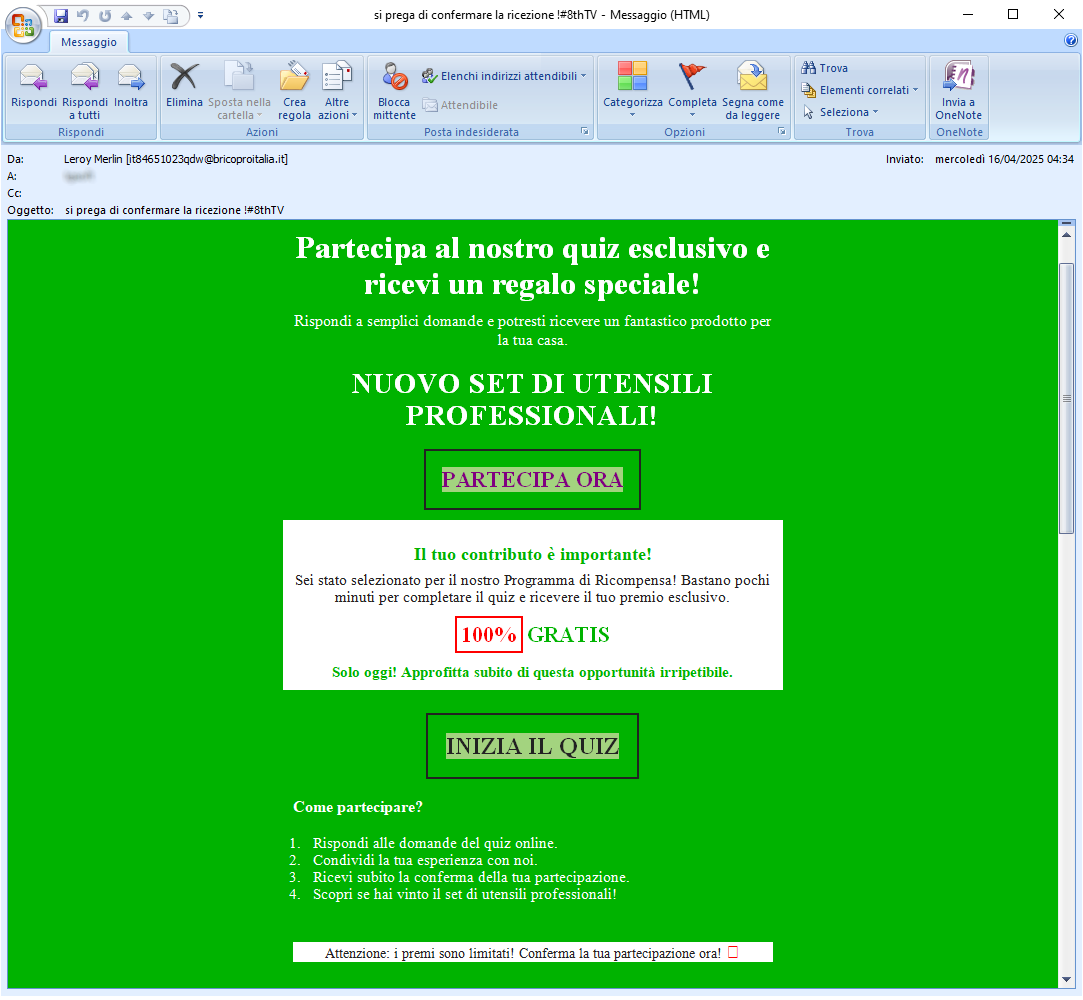
In the second reported example, a<
Quechua Hiking Equipment Package!> is supposedly offered as a prize by
DECATHLON, and it can again be claimed by participating in a short survey.
Clearly, the brands exploited in these campaigns are unrelated to the mass sending of these malicious e-mails, which are outright scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
In the two examples above we see that the emails clearly come from addresses <it84651023qdw[at]bricoproitalia[dot]it> and <support[at]jor[dot]zapateriadefer[dot]com> unrelated to the official domain of
LEROY MERLIN or
DECATHLON. This is definitely anomalous and should certainly make us suspicious.
If we click on the links in the email, we are redirected to a landing page that, although graphically deceptive (with misleading images and the brand's authentic logo), is always hosted on an anomalous address/domain, which does not seem at all trustworthy or traceable to the exploited brand.
The cybercriminals behind the scam, in order to achieve their goal, use various tricks, such as reporting false testimonials from customers who have won the prize. They try to persuade the user to complete the survey quickly, by making him/her believe that only a few can win, and that the offer expires today.
Surely if so many users were lucky why not try our luck?
When the survey is completed, the user is usually redirected to a page for the entry of the shipping address and subsequent payment of shipping costs.
The cybercriminals' purpose, is to induce the victim to enter his/her personal information to ship the prize and then, likely, also the credit card information to pay the shipping costs.
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links that may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is stolen by cyber crooks who can use it at will.
16 April 2025 ==> Phishing Aruba - Verifica Password (Password Verification)
SUBJECT: <
Verifica Password>
(Password Verification)
We find below another phishing attempt, pretending to be a communication from
Aruba.
The message warns the recipient that the password for his Aruba account will expire within 24 hours. To continue using the same password, the user must confirm it through the following link:
VERIFICA PASSWORD (Password Verification)
In case of non-confirmation any errors in accessing the account will be attributable only to the recipient..
We immediately see that the text of the e-mail is generic and does not provide any identifier of the client or the linked account. Another anomalous occurrence is the request to enter credentials, to update the account, through a link communicated via e-mail.
Clearly, the well-known web hosting, e-mail and domain registration services company,
Aruba, is uninvolved in the mass sending of these e-mails, which are real scams whose objective remains, as always, to steal sensitive data of the unsuspecting recipient.
The cybercriminal, in order to induce the victim to proceed promptly, allows little time to act. This technique is intended to intimidate the user, who is prompted to act without paying due attention, for fear of the block of his account and related services.
Anyone who unluckily clicks on the
VERIFICA PASSWORD (Password Verification), link will be directed to a WEB page that, although graphically well designed - in fact, the cybercriminal had the graphic foresight to include the logo of
Aruba - is not at all trustworthy. Again, the address/domain is anomalous and unrelated to
Aruba's official website.
On this page, the user is invited to access his or her client area by entering login and password to renew the password, and avoid malfunctions/locks.
We always urge you to be careful and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be delivered to the cyber-criminals creators of the scam, who will use them for their own purposes. In case of these cyber fraud attempts, we remind you not to be in a hurry and to pay attention to every detail, even the most trivial.
12 April 2025 ==> Phishing Amazon PRIME
«SUBJECT:
<Agisci ora: prolunga gratuitamente la tua iscrizione per 90 giorni!> (Act now: extend your membership for 90 days for free!)
We analyze the phishing attempt below, which comes from a fake
Amazon PRIME communication.
Amazon PRIME is the well-known streaming platform for movies, TV series, and other paid content. The goal of this scam is to steal the victim's credit card information.
The message, informs the user that his/her membership has expired, but that under the loyalty program,
Amazon PRIME allows the user to extend the membership for another 90 days free of charge. The offer can be activated through the following link:
Estendi e attiva (Extend and activate)
When we analyze the message, we see that it comes from an email address <
support(at)vol(dot)noxai(dot)co> not traceable to the official domain of
Amazon PRIME. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the
Estendi e attiva (Extend and activate) link, will be redirected to an anomalous WEB page which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for criminal purposes.
12 April 2025 ==> SexTortion
We find again the SexTortion-themed SCAM campaign. The sender of this scam email claims to have access to the user's device. The purpose of the message is to blackmail the recipient demanding the payment of a sum of money, in Bitcoin, in order not to divulge, among his/her email and social contacts, a private video of him/her viewing adult sites.
The following is an extract from the text of the email on the side:
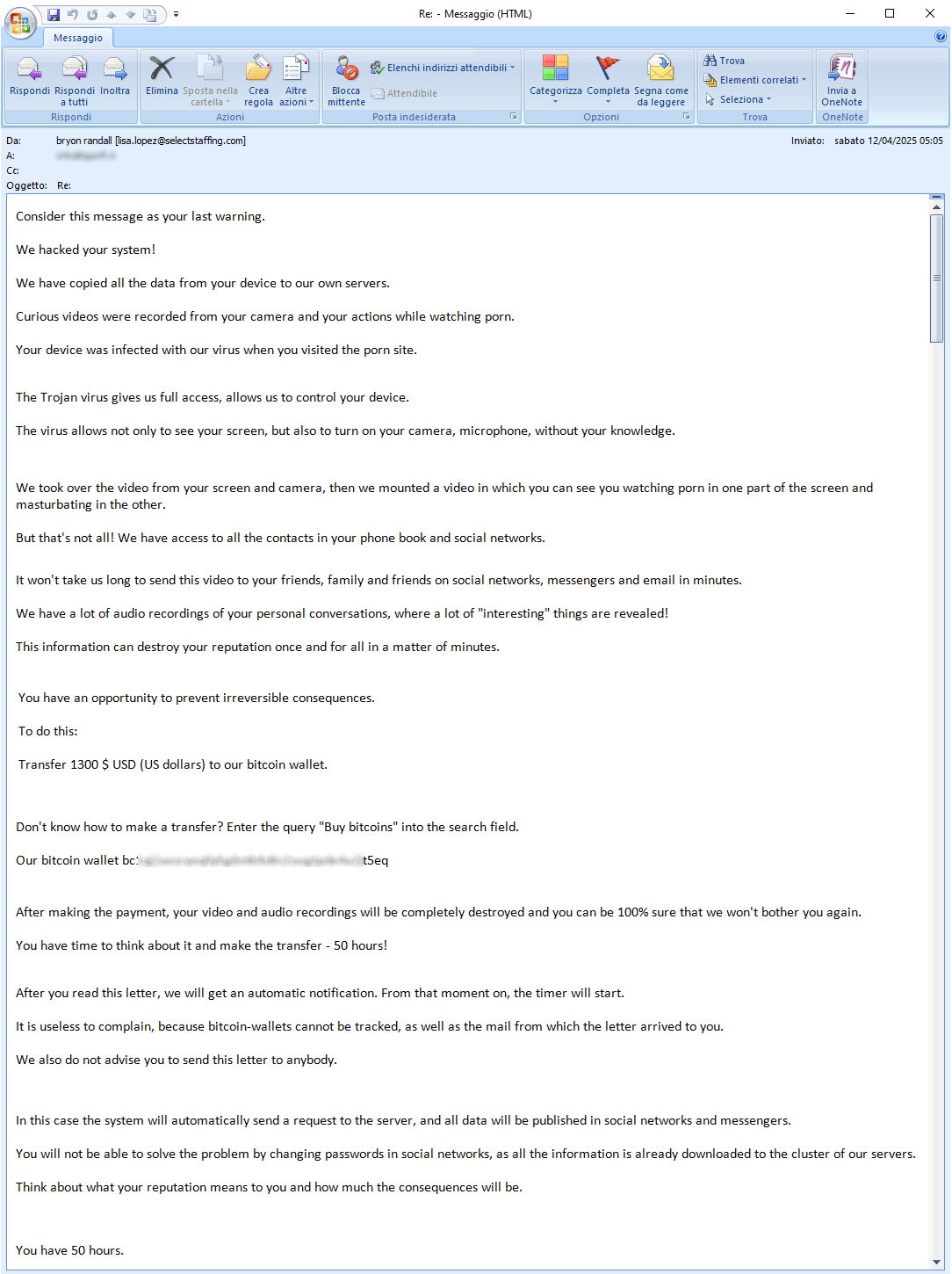
"Consider this message as your last warning. We hacked your system! We have copied all the data from your device to our own servers. Curious videos were recorded from your camera and your actions while watching porn. Your device was infected with our virus when you visited the porn site. The Trojan virus gives us full access, allows us to control your device. The virus allows not only to see your screen, but also turn on your camera, microphone, without knowledge. We took over the video from your screen and camera, then we mounted a video in which you can see you watching porn in una parte dello schermo and masturbating in the other. But that’s not all! We have access to all the contacts in your phone book and social networks. It won’t take us long to send this video to your friends, family and friends on social networks. We have a lot of audio recordings of your personal conversations, where a lot of “interesting” things are revealed! This information can destroy your reputation once and for all in a matter of minutes. You have an opportunity to prevent irreversible consequences…”
Next the victim is asked to send 1300 USD in Bitcoin to the wallet listed below: "
bc1XXXXXXXXXXXXXXXXXXXXXX85p'. After receiving the transaction, all data will be deleted, otherwise a video depicting the user will be sent to all colleagues, friends and relatives. The victim has 50 hours to make the payment!
As of
14/04/2025, there are no transactions on the reported wallet.
In such cases we always invite you:
- not to respond to these kinds of emails and not to open attachments or click unsafe links, and certainly NOT to send any money. You can safely ignore or delete them.
- if the criminal reports an actual user’s password – usually it is a password obtained from public Leaks (compromised data theft) of official sites occurred in the past (e.g., LinkedIn, Yahoo, etc.) - it is recommended to change it and enable two-factor authentication on that service.
07 April 2025 ==> SCAM Polizia di Stato (State Police)
«SUBJECT: <
Fwd: Risposta Urgente Convocazíone>
(Fwd: Urgent Response Convocation)
Below is an attempt at SCAM, which notifies a citation against the victim.
The message, which arrived via a very suspicious e-mail <
jose[dot]souza[dot]neto[at]icsa[dot]ufpa[dot]br>, contains only a .jpg attachment called <
IT070456-(1)> and a very concise text, which only mentions an e-mail to write to, for more information: <
pgiudiziaria39[at]gmail[dot]com>. The attachment, which we see below, is graphically deceptive and concerns a child pornography warrant, allegedly from “
Mr. Lamberto Giannini, Chief of Police and Director General of Public Security”. The victim is charged with child pornography, pedophilia, exhibitionism, and cyber pornography because he allegedly visited a child pornography site.

This is an attempted scam by cyber criminals, whose goal is to extort a sum of money, in this case in the form of a fine. In fact, the message states the following:
"Please respond to us via e-
email writing your justifications for them to be reviewed and verified in order to assess sanctions that within a strict 72-hour period."
If the victim fails to respond within 72 hours, a warrant will be issued with immediate arrest by the municipal postal police with subsequent entry in the national sex offender registry.
It is quite easy to understand that this is a false report, since we see that the report is not personal, moreover the document contains a very suspicious stamp.
This is clearly a scam attempt to steal sensitive user data and extort sums of money.
05 April 2025 ==> Phishing Sondaggio clienti BOSCH (Phishing BOSCH customer survey)
SUBJECT: <
Hai vinto un compressore d\'aria portatile per pneumatici Bosch GRATUITO! !# bZzSUU>
(You won a FREE portable Bosch tyre air compressor! bZzSUU)
Below we analyse the following scam attempt, concerning a false communication by the well-known German company
BOSCH.
The lucky user has been selected to take part in a quick survey and win a "BOSCH PORTABLE PNEUMATIC AIR COMPRESSOR".
Certainly this phishing is a real decoy for many inexperienced users.
Clearly
BOSCH is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient. So keep an eye out.
All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
We immediately realise that the message comes from an email address <
chell03[at]nexusart[dot]it> clearly not traceable to the official domain of
BOSCH. This is definitely abnormal and should, at the very least, make us suspicious. However, if we go ahead and click on the link
Clicca qui per iniziare! (Click here to start!) in the email, this is what happens:
we are redirected to a landing page which, although graphically well designed (with misleading images and the authentic
BOSCH logo) does not seem trustworthy at all.
The survey to obtain the prize is, in fact, hosted on an anomalous address/domain:
https[:]//[FakeDomainName*]....
which has no connection with
BOSCH.
The cyber-criminals masterminding the scam, try to induce the user to quickly complete the survey by making him/her believe that there are only a few lucky people and that the offer expires in the day. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
When we click on
INIZIA IL SONDAGGIO (START THE SURVEY), we are taken to the next screens, where we are asked to answer 8 questions.
Here specifically is question 1/8. These are generic and poorly worded questions, focused on the degree of satisfaction with the services offered and the marketing/promotional choices implemented by
BOSCH. We see that the countdown timer is also present here, to induce the user to quickly conclude the process for the prize.
When the survey is over, we can finally claim our prize: a Bosch portable air compressor for tyres. which would be worth Euro 59.99 but costs us 0..We only have to pay the shipping costs...
But let's hurry.. Looks like there are only 2 left in stock
Here we are: we just have to enter our shipping address and pay the shipping costs and, in 5-7 working days, the prize will be delivered.
To make it more reliable, many comments from customers who supposedly participated in the survey, have been reported. These are all confirming testimonials/feedback about the actual delivery of the winnings, ensuring that it is not really a scam.....
Surely if so many users were lucky why not try our luck?
Then, when we click on
Continua (Continue), we are redirected to a further page to enter our shipping address and pay shipping costs of Euro 2.
As we can see from the image on the side, the cybercriminals' intent is to lure the victim into entering sensitive data in order to proceed with the shipment of the prize. Subsequently, it is presumed that they also request credit card details for the payment of shipping fees.
The page we are redirected to, for entering our personal data, is hosted on an address/domain that is still abnormal:
https[:]//[FakeDomainName*][.]com
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is placed in the hands of cyber crooks who can use it at will.
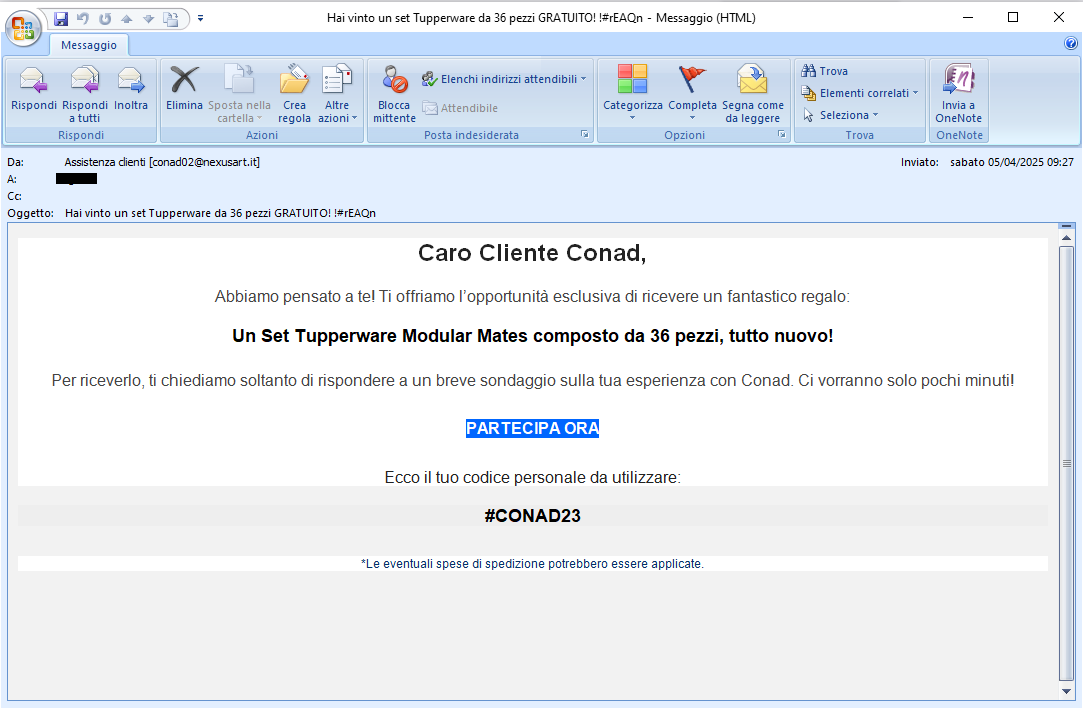
05 April 2025 ==> Phishing sondaggio clienti (Phishing customer survey): CONAD/ESSELUNGA
Customer survey-themed phishing campaigns, exploiting well-known brands, continue. In the two cases below they involve large-scale retail companies.
In the first reported example, the cybercriminal used the well-known
CONAD brand name, for a promotional message that would allow one to win an exclusive prize: <
A Tupperware Modular Mates Set consisting of 36 pieces>. To claim the prize, you just need to answer a few short questions.
In the second example shown, the same prize <
Tupperware Modular Mates set consisting of 36 pieces> is offered - again by participating in a short survey - seemingly by the large retail company
ESSELUNGA.
Clearly the brands exploited in these campaigns are unrelated to the mass sending of these malicious e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
In the two examples shown we see that the emails <
conad02[at]nexusart[dot]it> and <
mega[dot]botar[dot]co[dot]uk-*****> clearly come from addresses unrelated to the official domain of
CONAD or
ESSELUNGA. This is definitely abnormal and should certainly make us suspicious.
If we click on the links in the e-mail, we are directed to a page that is graphically deceptive (with misleading images and the brand's authentic logo), but is located on an abnormal address/domain that does not seem at all reliable or traceable to the exploited brand.
The cybercriminals behind the scam, in order to achieve their goal, use various tricks, such as reporting false testimonials from customers who have won the prize. They try to persuade the user to complete the survey quickly by making him/her believe that only a few can win and that the offer expires today.
Surely if so many users were lucky why not try our luck?
When the survey is over, the user is redirected to a page to enter his/her shipping address and pay the charges.
The cybercriminals' purpose is to induce the victim to enter his/her personal information to ship the prize and then, likely, also the credit card information to pay the shipping costs.
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links that may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is stolen by cyber crooks who can use it at will.
04 April 2025 ==> Phishing Aruba - Aggiorna pagamento (Update Payment)
SUBJECT: <
Ultimo Avviso per il Rinnovo del Tuo Dominio>
(Last Notice for Domain Renewal)
Phishing attempts pretending to be communications from the
Aruba brand continue.
The message informs the receiver that the last payment for his/her domain hosted on
Aruba was not successful. The user must pay within 48 hours, otherwise the account may be suspended and the services deactivated.
The message then invites him/her to update the payment method via the following link:
Aggiorna Metodo di Pagamento (Update Payment Method)
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba, is uninvolved in the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal the sensitive data of the unsuspecting recipient.
When we analyse the text of the message, we immediately notice that the sender's e-mail address <
anis[dot]hassar-etu[at]etu[dot]univh2c[dot]ma> is not from the official domain of
Aruba.
In order to induce the victim to quickly renew his/her mailbox, 48 hours are given. This is intended to prompt the user to act immediately and without much thought, due to fear of the mailbox deactivation.
Anyone who unluckily clicks on the
Aggiorna Metodo di Pagamento (Update Payment Method) link, will be directed to the displayed page.
The landing page, unlike what expected, does not refer to the form to access
Aruba's RESTRICTED AREA, but hosts an online payment form, that appears to rely on the circuit of
BancaSella. Here we are directly asked to enter credit card data to pay the modest sum of Euro 12.99.
Although haste and fear of the suspended email box may push the user to quickly complete the transaction, if we look at the url address of the broswer, we see that the payment form does not reside on the official domain of
Aruba or even
BancaSella.
Therefore, we urge you not to rush and to be aware that, in case of these cyber fraud attempts, you should pay attention to every detail, even trivial ones.
If you enter the requested data, in our case credit card information, it will be delivered to the cyber criminals masterminding the scam, who will use it for malicious purposes.
03 April 2025 ==> Phishing NETFLIX
«SUBJECT:
<Azione Richiesta: Verifica i Dati di Pagamento del Tuo Abbonamento> (Required Action: Verify Your Subscription Payment Detail)
Below we analyze a phishing attempt that originates from a fake communication claiming to be from NETFLIX, the well-known streaming platform for movies, TV series, and other paid content. The goal of this scam is to steal the victim's credit card information.
The message informs the user that
NETFLIX is unable to renew his/her subscription, due to problems with the payment of €
6.99. The user is then asked to update his/her data using the link:
Aggiorna i dati (Update your data)
When we analyse the message comes from an e-mail address <
cin(at)nucl(dot)it> not traceable to the official domani of
NETFLIX. This is definitely abnormal and should raise our suspicions.
Anyone who unluckily clicks on the
Aggiorna i dati (Update your data) link, will be redirected to an anomalous WEB page, which has no connection with the official website of
NETFLIX, but which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for criminal purposes.
03 April 2025 ==> Phishing Aruba - Verifica Password ( Password Verification)
SUBJECT:<
Final Warning-Verifica Password> (
Final Warning- Password Verification)
Phishing attempts, pretending to be communications from the
Aruba brand, continue.
The message informs the recipient that the password of his/her account will expire in 24 hours, on 4/4/2025. It then invites the user to log in to his/her domain on Aruba and confirm the password in order to guarantee the continuity of the services, and keep the same password. In order to confirm the password a link is provided:
VERIFICA PASSWORD (Password Verification)
Clearly the well-known web hosting, e-mail and domain registration services company
Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
When we analyse the e-mail we immediately notice that the message comes from the recipient's own address and not from the official domain of
Aruba. It is crucial to always pay the utmost attention before clicking on suspicious links.
Anyone who unluckily clicks on the VERIFICA PASSWORD (Verify Password) link, will be redirected to the displayed web page.
On this page, the user is invited to access his/her customer area entering a login and password to confirm his/her access data and thus avoid a block of services.
Although the site may be misleading due to the Aruba logo, we see that the url address in the browser bar is anomalous and not traceable to the company's official domain:
https[:]//[FakeDomainName*].com.br...
If you enter your data on counterfeit websites, it will be delivered to the cyber criminals behind the scam who will use it for malicious purposes. We therefore urge you not to rush and to be aware that, in case of these attempted cyber frauds, it is necessary to pay attention to every detail, even trivial ones.
03 April 2025 ==> Phishing Google Drive
SUBJECT: <
"Hai raggiunto il limite di spazio di archiviazione!">
(You have reached your storage space limit!)
We analyse below the phishing attempt aimed at stealing the credentials of the victim's
Google account.
The message informs the recipient that the storage space is full, so photos and videos are no longer being updated and are at risk of deletion. However, a special offer is available for customers of the loyalty programme, which entitle them to 50GB of extra space at a cost of EUR 2 per year. To obtain the 50GB, simply click on the following link:
Ricevi 50 GB (Get 50 GB)
When we analyse the message, we see that it comes from an email address <
support[at]xht[dot]decormonks[dot]com> clearly not traceable to the
Google server. This is definitely abnormal and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link, will be directed to an abnormal web page, which is supposed to simulate the Google account login page.
This page reiterates the chance to receive 50 GB more storage space for only EUR 2 per year. Promotions that require payment of a small fee are usually used to steal credit card data.
The link refers to another page for the credit card data entry, again with an abnormal address/domain:
https[:]//[FakeDomainName*].com/.....
We always urge you to pay attention to every detail, even trivial ones, and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber crooks, with all the easily imaginable risks.
01-02 April 2025 ==> Phishing sondaggio clienti (Phishing customer survey): LAVAZZA/TELEPASS
Customer survey-themed phishing campaigns, exploiting well-known brands, continue. In the two cases below, they involve companies from the retail and mobility services sectors..
In the first reported example the cybercriminal used the well-known LAVAZZA brand for a promotional message. It would allow the participant to win an exclusive <Free Lavazza Coffee Machine>, through a short survey.

In the second case, again taking part in a short survey - seemingly by
TELEPASS - the participant can win a <
Car Emergency Kit>.
Clearly the brands involved in these campaigns, are unrelated to the mass sending of these malicious e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
In the two examples shown, the e-mails come from addresses <support[at]gsp[dot]trenbaru[dot]com>, <info[at]pes[dot]sub2earn[dot]in> clearly unrelated to the official domain of
LAVAZZA or
TELEPASS. This is definitely abnormal and should certainly raise our suspicions.
If we click on the links in the e-mail, we are directed to a page that is graphically deceptive (with misleading images and the brand's authentic logo), but is located on an abnormal address/domain, that does not seem at all reliable or traceable to the exploited brand.
The cybercriminals behind the scam, in order to achieve their goal, use various tricks, such as reporting false testimonials from customers who have won the prize. They try to persuade the user to complete the survey quickly by making him/her believe that only a few can win and that the offer expires today.
Surely if so many users were lucky why not try our luck?
When the survey is over, we are redirected to a page to enter the shipping address and pay the charges.
The cybercriminals' purpose, is to induce the victim to enter his/her personal information to ship the prize and then, likely, also the credit card information to pay the shipping costs.
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links that may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is stolen by cyber crooks who can use it at will.
A little bit of attention and glance can save a lot of hassles and headaches...
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on phishing techniques for more details:
03/02/202514:54 - Phishing: the most common credential and/or data theft attempts in February 2025...
03/01/2025 14:40 - Phishing: the most common credential and/or data theft attempts in January 2025...
03/12/2024 14:47 - Phishing: the most common credential and/or data theft attempts in December 2024...
06/11/2024 14:33 - Phishing: the most common credential and/or data theft attempts in November 2024...
07/10/2024 14:33 - Phishing: the most common credential and/or data theft attempts in October 2024...
04/09/2024 09:28 - Phishing: the most common credential and/or data theft attempts in September 2024
06/08/2024 14:50 - Phishing: most popular credential and/or data theft attempts in August 2024...
04/07/2024 17:22 - Phishing: the most common credential and/or data theft attempts in July 2024.
03/06/2024 17:22 - Phishing: the most common credential and/or data theft attempts in June 2024..
03/05/2024 11:56 - Phishing: the most common credential and/or data theft attempts in May 2024..
03/04/2024 10:23 - Phishing: the most common credential and/or data theft attempts in April 2024...
04/03/2024 10:42 - Phishing: the most common credential and/or data theft attempts in March 2024..
Try Vir.IT eXplorer Lite
 If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
Vir.IT eXplorer Lite has the following special features:
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- fully interoperable with other AntiVirus software and/or Internet Security products (both free and commercial) already installed on your computer. It doesn't need any uninstallation and it doesn't cause slowdowns, as some features have been appropriately reduced to ensure interoperability with the AntiVirus software already on your PC/Server. This, however, allows cross-checking through the scan;
- it identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M
- Download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
VirIT Mobile Security AntiMalware ITALIAN for ALL AndroidTM Devices
VirIT Mobile Security Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats, and empowers the user to safeguard his/her privacy with an advanced heuristic approach (Permission Analyzer).

TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can download the Lite version, which can be freely used in both private and corporate settings.
You can upgrade to the PRO version by purchasing it directly from our website=> click here to order
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities to our Research Center, that allowed us to make this information as complete as possible.
How to submit suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways:
- any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).

For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page:
How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
TG Soft Anti-Malware Research Centre (C.R.A.M.)


 "Consider this message as your last warning. We hacked your system! We have copied all the data from your device to our own servers. Curious videos were recorded from your camera and your actions while watching porn. Your device was infected with our virus when you visited the porn site. The Trojan virus gives us full access, allows us to control your device. The virus allows not only to see your screen, but also turn on your camera, microphone, without knowledge. We took over the video from your screen and camera, then we mounted a video in which you can see you watching porn in una parte dello schermo and masturbating in the other. But that’s not all! We have access to all the contacts in your phone book and social networks. It won’t take us long to send this video to your friends, family and friends on social networks. We have a lot of audio recordings of your personal conversations, where a lot of “interesting” things are revealed! This information can destroy your reputation once and for all in a matter of minutes. You have an opportunity to prevent irreversible consequences…”
"Consider this message as your last warning. We hacked your system! We have copied all the data from your device to our own servers. Curious videos were recorded from your camera and your actions while watching porn. Your device was infected with our virus when you visited the porn site. The Trojan virus gives us full access, allows us to control your device. The virus allows not only to see your screen, but also turn on your camera, microphone, without knowledge. We took over the video from your screen and camera, then we mounted a video in which you can see you watching porn in una parte dello schermo and masturbating in the other. But that’s not all! We have access to all the contacts in your phone book and social networks. It won’t take us long to send this video to your friends, family and friends on social networks. We have a lot of audio recordings of your personal conversations, where a lot of “interesting” things are revealed! This information can destroy your reputation once and for all in a matter of minutes. You have an opportunity to prevent irreversible consequences…”  This is an attempted scam by cyber criminals, whose goal is to extort a sum of money, in this case in the form of a fine. In fact, the message states the following:
This is an attempted scam by cyber criminals, whose goal is to extort a sum of money, in this case in the form of a fine. In fact, the message states the following: If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS. For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis