PHISHING INDEX
Below are the most common email phishing attempts detected by the TG Soft Anti-Malware Research Center in October 2025:
16/10/2025 =>
PayPal
15/10/2025 =>
Webmail
10/10/2025 =>
Email Account
08/10/2025 =>
Judicial Police Scam
07/10/2025 =>
Survey - Esselunga / Telepass
07/10/2025 =>
Netflix
06/10/2025 =>
SexTortion
06/10/2025 =>
WeTransfer
05/10/2025 =>
SumUp
03/10/2025 =>
Aruba - Expired domain
01/10/2025 =>
Google Cloud
These emails aim to deceive unsuspecting victims into providing sensitive information, such as bank account details, credit card codes, or personal login credentials, with all the easily imaginable consequences.
16 October 2025 ==> Phishing PayPal
SUBJECT: <
Identification required by 16 October.>
Below, we analyse a new phishing attempt that aims to steal login credentials for
PayPal accounts, the well-known US digital payments company.
The message informs the recipient that he/she must identify himself/herself online by logging into his/her
PayPal account to avoid the block of online banking services. A code valid for 24 hours is then provided to be entered for identification, and then the account will be blocked. The user is then invited to identify himself/herself via the following link:
https://www[dot]paypal[dot]com/id[=]672300648776
When we analyse the email, we notice that the message comes from an email address <
postmaster[at]06fd44e6c9[dot]nxcli[dot]io> that is clearly not linked to the
PayPal official domain. This is definitely unusual and should make us suspicious.
Anyone who unluckily clicks on the link will be taken to the screen shown in the image on the right.
As we can see, the user is redirected to a site that graphically simulates the
PayPal login page. However, the site is hosted on an unusual address/domain.
Given these considerations, we advise you to NEVER enter your credentials on websites whose origin you do not know, as they will be sent to a remote server and used by cyber fraudsters, with all the associated risks easy to imagine.
15 October 2025 ==> Phishing Webmail
SUBJECT: <
Your Password is About to Expire>
Below, we analyse another phishing attempt that aims to steal the victim's
Webmail account credentials.
The message, in English, informs the recipient that his/her email account password is about to expire. It then invites him/her to update his/her password before it expires, in order to avoid service interruptions, via the following link:
Keep My Password o Modify My Password
When we analyse the email, we see that the message appears to come from the recipient's own email account. Cybercriminals use this trick to induce users to enter their real credentials, which are then used for criminal purposes. This is highly unusual and should make us very suspicious.
Anyone who unluckily clicks on the link will be redirected to a fake web page, which is designed to look like the
Webmail login page.
On this page, users are asked to log in to their account by entering their email password to confirm or change their password, which is due to expire.
Actually, the page where the user is redirected to enter his/her email account credentials is hosted on an unusual address/domain, which we report below:
https[:]//[FakeDomainName*].com/.....
We urge you to always pay attention to every detail, even trivial ones, and not to enter your personal details and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber fraudsters, with all the associated risks that this entails.
10 October 2025 ==> Phishing Email Account
SUBJECT: <
Action required: ***** Your password is set to expire today.>
Below, we analyse a phishing attempt that aims to steal the email account credentials of the victim.
The message informs the recipient that his/her email account password expires today. It then invites him/her to update his/her password before the expiry date, in order to avoid service interruptions, via the following link:
Keep your current password
When we analyse the message, we see that it has an email address <
marie(dot)trnkova(at)techlib(dot)cz> that cannot be traced back to the email server. This is definitely unusual and should make us suspicious.
Anyone who unluckily clicks on the link will be redirected to a fake web page, which is designed to look like the email account login page.
On this page, users are asked to log in to their account by entering their email password to confirm or change their current password, which is due to expire.
Actually, the page where we are redirected to enter our email account credentials is hosted on an unusual address/domain, which we report below:
https[:]//[FakeDomainName*].com/.....
We urge you to always pay attention to every detail, even trivial ones, and not to enter your personal details and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber fraudsters, with all the associated risks that this entails.
08 October 2025 ==> Judicial Police scam
«SUBJECT: <
POLICE SUMMONS LETTER>
Below is an example of a SCAM attempt, consisting of a false summons for child pornography that comes via email, supposedly from the
Central Directorate of the Criminal Police.
The message, which has a highly suspicious email address <
boboy08993672[at]gmail[dot]com>, contains the following message: ‘ATTENTION: THE ATTACHED FILE IS A POLICE REPORT. PLEASE READ THE ATTACHED FILE AND RESPOND IMMEDIATELY.’
When we open the PDF attachment named <
State Police>, shown below, we notice that it is graphically misleading and appears to come from
Mauro Falesiedi from the Central Directorate of the Criminal Police. The fasle complaint accuses the victim of child pornography, paedophilia, exhibitionism and cyber pornography, as he allegedly visited a child pornography website.

This is an attempt at fraud by cybercriminals, whose aim is to extort money, in this case in the form of a fine. In fact, the message states the following:
"
[...[ We hereby request that you respond to these (three) charges within a strict time limit of 48 hours.."
If the victim does not respond within 48 hours, an arrest warrant will be issued, punishable by imprisonment for six to twelve years and a fine from €78,000 to €250,000.
The complaint is clearly fake because it is not personal.
This is clearly an attempt at fraud with the aim of stealing sensitive user data and extorting money.
4-7 October 2025 ==> Phishing customer survey: ESSELUNGA / TELEPASS
This month, we are once again seeing phishing campaigns themed around customer surveys that exploit the brands of well-known companies. In the two cases reported below, the companies involved are large retailers and mobility service providers.
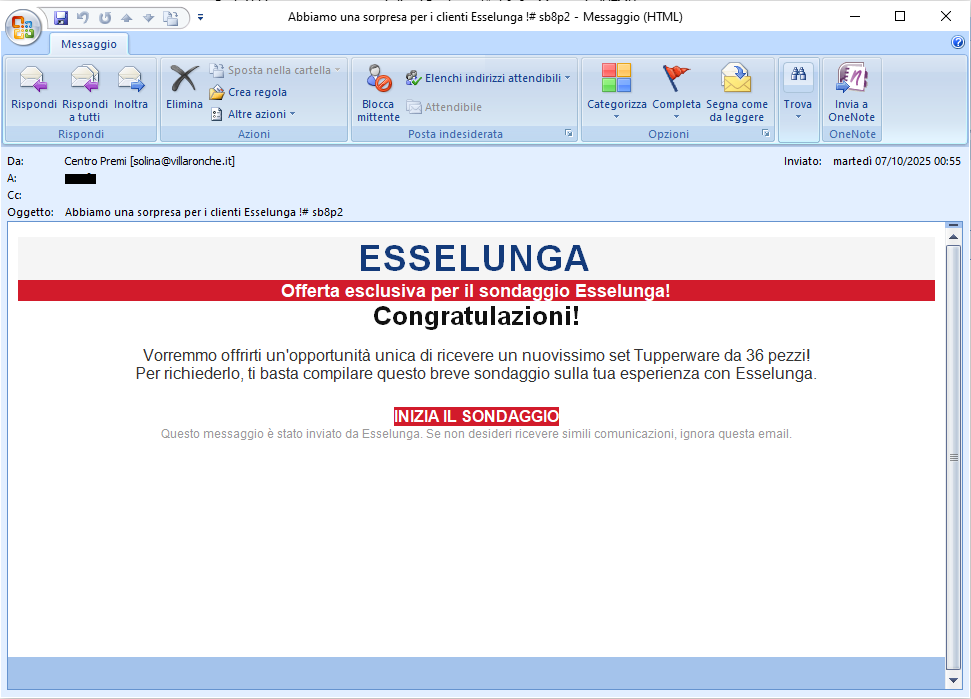
In the first example, the cybercriminal used the well-known
ESSELUNGA, brand to launch a promotional message that seems to offer the chance to win an exclusive prize: <
Set Tupperware da 36 pezzi!>. To claim the prize, all the user has to do is to answer a few short questions.
In the second example, the cybercriminal used the well-known
TELEPASS, brand to launch a promotional message that seems to offer the chance to win an exclusive prize: <
EMERGENCY CAR KIT>. To claim the prize, all the user has to do is to answer a few short questions.
Clearly, the brands exploited in these campaigns are unrelated to the mass sending of these malicious emails, which are genuine scams whose aim remains, as always, to steal sensitive data from unsuspecting recipients.
In the two examples shown, we can see that the emails clearly come from addresses <
it004passa[at]leggiparrucchieri[dot]it> and <
solina[at]villaronche[dot]it>unrelated to the official
TELEPASS and
ESSELUNGA domains. This is definitely unusual and should make us suspicious.
When we click on the links in the e-mail, we are directed to a landing page that may look graphically deceptive (with misleading images and the brand's authentic logo), but is hosted on an abnormal address/domain that is not trustworthy or traceable to the exploited brand.
The cybercriminals behind the scam, in order to achieve their goal, use various tricks, such as reporting false testimonials from customers who have won the prize. They try to persuade the user to complete the survey quickly, by making him/her believe that only a few can win, and that the offer expires today.
Surely if so many users were lucky why not take a chance?!
When the survey is completed, the user is usually sent to a page for the entry of the shipping address and subsequent payment of shipping costs.
The cybercriminals' purpose, is to induce the victim to enter his/her personal information to ship the prize and then, likely, also the credit card information to pay the shipping costs.
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is stolen by cyber crooks who can use it at will.
07 October 2025 ==> Phishing NETFLIX
SUBJECT:
<Your payment has not been processed. — update your details>
We examine another phishing attempt coming as a fake communication from
NETFLIX, the well-known streaming platform for films, television series, and other paid content, which aims to steal the credit card details of the victim.
The message informs the user that a problem has been encountered in processing the payment of
£6.99 for his/her subscription. To continue using the service without interruption, the user must update his/her payment details within 48 hours via the following link:
Update payment
When we examine the email, we see that the message has an email address <
alp(at)fidelfatti-impianti(dot)it> that is not traceable to the official
NETFLIX domain. This is definitely unusual and should make us suspicious.
Anyone who unluckily clicks on the
Update payment link will be redirected to a web page unrelated to
NETFLIX but designed to steal your most valuable data for criminal purposes.
06 October 2025 ==> SexTortion
The SexTortion-themed SCAM campaign is back. The e-mail seems to hint that the scammer had access to the victim's device. In fact, he appears to have used it to collect data and personal videos and then blackmailed the user by demanding payment of a sum of money, in the form of Bitcoin, not to divulge among his/her email and social contacts a private video of him/her looking at adult sites.
Below is an extract from the text of the email shown on the side:
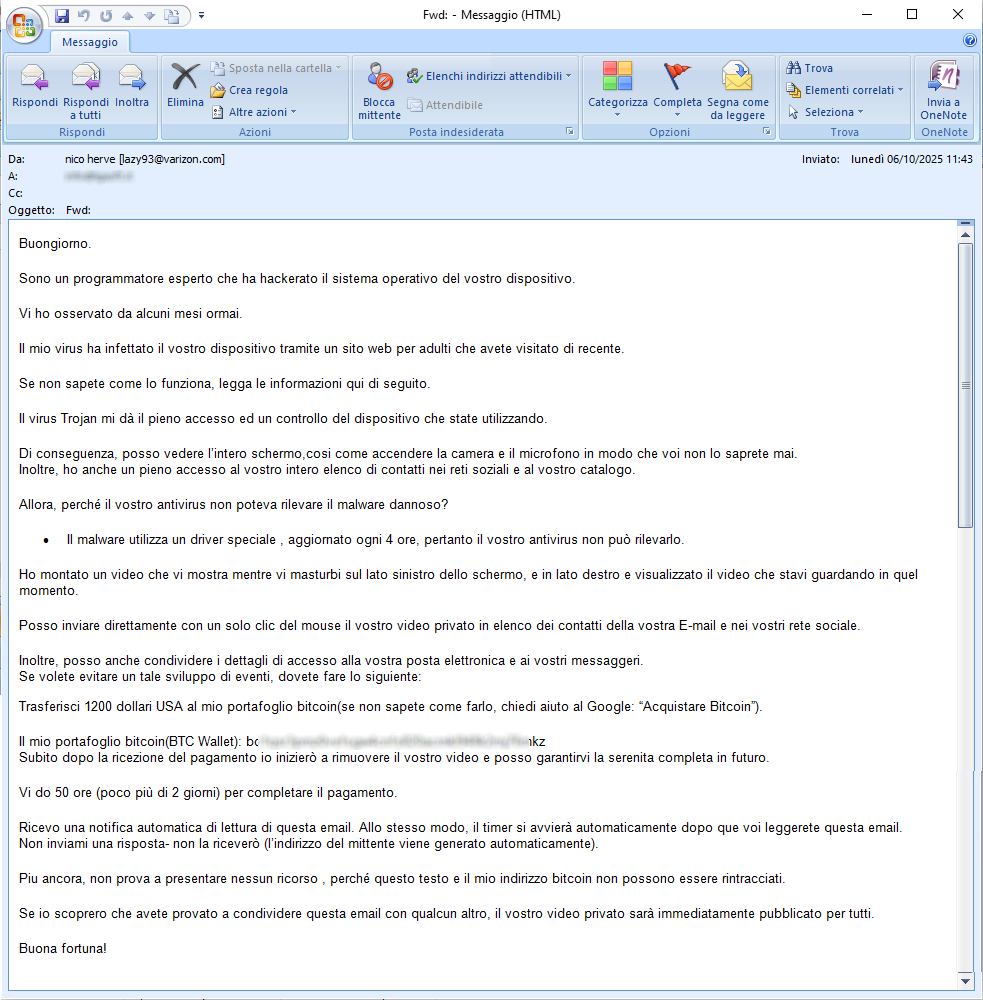
"
Good morning. I am an experienced programmer who has hacked into your device's operating system. I have been watching you for several months now. My virus infected your device via an adult website you visited recently. If you don't know how it works, please read the information below. The Trojan virus gives me full access and control of the device you are using. As a result, I can see your entire screen, as well as turn on your camera and microphone without you ever knowing. In addition, I also have full access to your entire list of contacts on social networks and your catalogue. So why couldn't your antivirus detect the malicious malware? • The malware uses a special driver, updated every 4 hours, so your antivirus cannot detect it. I have created a video showing you masturbating on the left side of the screen, and on the right side, I have displayed the video you were watching at that moment. With a single click of the mouse, I can send your private video directly to your email contacts and social networks. In addition, I can also share your email and messenger login details."
At this stage, the agreement not to disclose the video is to send 1,200 USD in Bitcoin to the wallet indicated below: “
bc1XXXXXXXXXXXXXxXXXXXXXXmkz”. After receiving the transaction, all data will be deleted. Otherwise, a video depicting the user will be sent to all colleagues, friends and relatives. The victim has 50 hours to make the payment!
An analysis of the payments made to the wallet on
08/10/2025 shows no transactions.
In such cases we always invite you:
- not to respond to these kinds of emails and not to open attachments or click unsafe links, and certainly NOT to send any money. You can safely ignore or delete them.
- if the criminal reports an actual user’s password – usually it is a password obtained from public Leaks (compromised data theft) of official sites occurred in the past (e.g., LinkedIn, Yahoo, etc.) - it is recommended to change it and enable two-factor authentication on that service.
06 October 2025 ==> Phishing WeTransfer
SUBJECT:<
Your files have not yet been downloaded...>
Below, we analyse a phishing attempt that aims to steal
WeTransfer account credentials.
The message informs the recipient that there are files that have not yet been downloaded and there is until 7 October to download them. After that date, only Ultimate users will be able to access the documents within a certain number of days. It then invites him or her to upgrade the account to postpone the expiry date of the pending files via the following link:
Upgrade now
When we analyse the email, we see that the message comes from an email address <
merry(at)merryriana(dot)com> that is not linked to the
WeTransfer domain. This is definitely unusual and should make us suspicious.
Anyone who unluckily clicks on the
Upgrade now link, will be redirected to an anomalous WEB page, which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for malicious purposes.
05 October 2025 ==> Phishing SumUp
SUBJECT: <
Confirm your email address so as not to miss any communications from SumUp>
Below, we analyse a new phishing attempt that pretends to be an official communication from
SumUp, a well-known London-based digital payments company.
The message asks the recipient to verify his/her email address immediately to ensure the security and proper functioning of the
SumUp account.
To confirm, the user just needs to click on the following link:
Check Now
The well-known London-based company is clearly not involved in the mass sending of these emails, which are genuine scams whose aim, as always, is to steal sensitive data from unsuspecting recipients.
If we look closely at the message, there are a few clues that should raise suspicion. First of all the email address of the message <
danysamyue[at]myt[dot]mu> does not belong to the official
SumUp domain. This is definitely unusual and should raise suspicion. Another strange fact is that the email does not provide any customer identification details and asks the user to enter his/her account credentials via a link provided in the email.
Anyone who unluckily clicks on the
Check Now link, will be redirected to an anomalous WEB page, which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for malicious purposes.
We therefore urge you to always pay close attention to even the smallest details and not to enter your personal details and/or passwords on forms hosted on counterfeit web pages, as they will be used by cyber criminals for illegal purposes.
03 October 2025 ==> Phishing Aruba - Expired domain
SUBJECT: <
Expired domain: imminent suspension risk>
Phishing attempts, claiming to be communications from the
Aruba brand, continue this month.
The message informs the recipient that his/her domain hosted on
Aruba has expired. It then warns him/her that in order to avoid service interruptions, he/she can immediately renew the domain via the following link:
Renew your domain
Let's always be careful with requests to enter personal credentials via suspicious links sent by e-mail.
Clearly, the well-known web hosting, e-mail and domain registration company,
Aruba, is not involved in the mass sending of these emails, which are genuine scams whose aim, as always, is to steal sensitive data from unsuspecting recipients
We immediately see that the email address of the message <
postmaster[at]vmt[dot]alicornaqua[dot]com> does not belong to the official
Aruba domain. This is highly unusual and should make us suspicious.
The cybercriminal, to induce the victim to act quickly, the cybercriminal allows little time to respond. This technique is clearly intended to intimidate the user, who, fearing that he/she will be unable to access his/her account and use the services linked to it, is prompted to act without paying due attention.
Anyone who unluckily clicks on the link, will be redirected to an anomalous WEB page, which has already been reported as DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for illegal purposes.
01 October 2025 ==> Google Cloud
SUBJECT: <
"Your 50 GB cloud offer is pending" >
Below, we analyse the scam attempt hidden behind a fake communication supposedly from
Google Cloud, a service that allows users to store photos, videos and documents. Specifically, it is a message warning users that their documents will soon be deleted.
As we can see in the image on the side, the message warns the user that his/her storage space on
Google Cloud is full, and that if he/she does not take action as soon as possible, his/her photos, videos, contacts, files and data will be lost. The user is then invited to purchase additional space in order to prevent the loss of all data.
Google Cloud is clearly not involved in sending these malicious campaigns, which are outright scams whose goal remains, as always, to steal sensitive data from unsuspecting recipients.
This is, in fact, a phishing attempt aimed at stealing the personal data of unsuspecting users.
So keep your eyes open... a little caution and a quick glance are all it takes to avoid unpleasant surprises.
If we look at the email, we see that the sender <
service[at]sk[dot]tapajosdepremios[dot]com[dot]br> is clearly not linked to the official
Google Cloud domain, a decidedly unusual fact that should make us suspicious.
Moreover, if we click on
UPDATE SPACE, we are redirected to a “landing” page which, although graphically well designed, does not seem at all trustworthy. In fact, it is hosted on an unusual address/domain unrelated to the official
Google Cloud domain.
If we click on
Continue, a page will open showing us how to prevent photos, videos and documents from being lost forever.
In fact, thanks to a loyalty programme, an additional 50 GB of storage space can be obtained for just £1.95. To take advantage of this special offer, we need to answer three simple, generic questions, which provide cyber fraudsters with information about the users, such as their country of origin.
Once all questions have been answered, it will finally be possible to request the additional storage space that will allow us to save all the data stored so far.
Then, when we click
Continue, we will be taken back to the last screen where we are asked to enter our personal details and proceed with the payment of $1.95 to obtain the additional 50 GB of storage space.
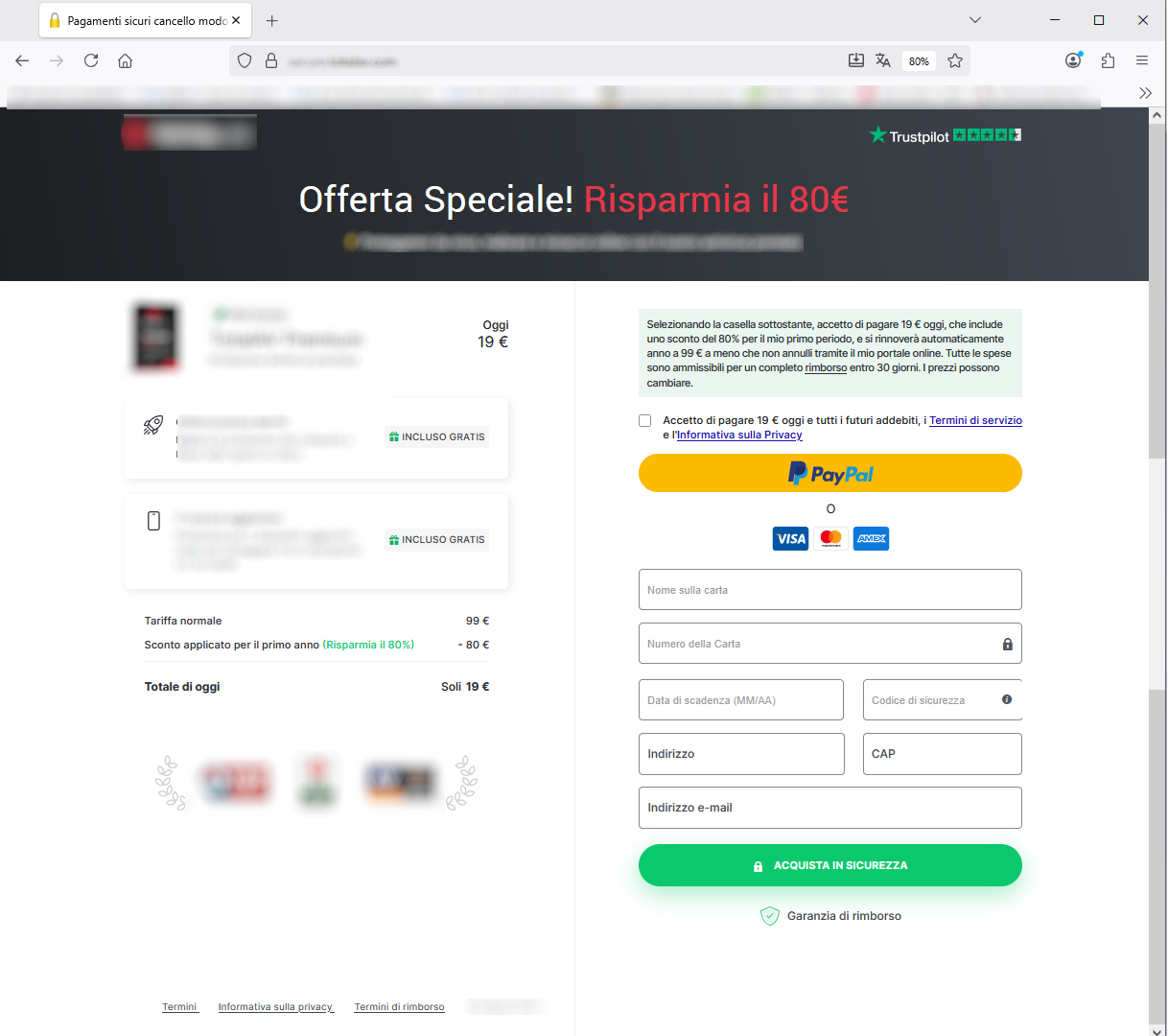
The aim of cyber criminals is precisely to induce users to enter their sensitive data!
The page where we are redirected to enter our personal data is hosted on the following anomalous address/domain, which we report below
https[:]//gryoulucky[.]com/it/....
To conclude, we urge you to always be vigilant and avoid clicking on suspicious links which could lead you to a fake website, putting your most valuable data in the hands of cyber criminals who can use use it at will.
A little attention and glance can save a lot of hassles and headaches
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on phishing techniques for more details:
04/09/2025 09:45 - Phishing: the most common credential and/or data theft attempts in September 2025...
05/08/2025 08:58- Phishing: the most common credential and/or data theft attempts in August 2025...
01/07/2025 16:04 - Phishing: the most common credential and/or data theft attempts in July 2025.
05/06/2025 09:22 - Phishing: the most common credential and/or data theft attempts in June 2025...
05/05/2025 15:03 - Phishing: the most common credential and/or data theft attempts in May 2025...
07/04/2025 14:22 - Phishing: the most common credential and/or data theft attempts in April 2025...
07/03/2025 15:10 - Phishing: the most common credential and/or data theft attempts in March 2025..
03/02/202514:54 - Phishing: the most common credential and/or data theft attempts in February 2025...
03/01/2025 14:40 - Phishing: the most common credential and/or data theft attempts in January 2025...
03/12/2024 14:47 - Phishing: the most common credential and/or data theft attempts in December 2024...
06/11/2024 14:33 - Phishing: the most common credential and/or data theft attempts in November 2024...
07/10/2024 09:55- Phishing: the most common credential and/or data theft attempts in October 2024...
Try Vir.IT eXplorer Lite
 If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
Vir.IT eXplorer Lite has the following special features:
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- fully interoperable with other AntiVirus software and/or Internet Security products (both free and commercial) already installed on your computer. It doesn't need any uninstallation and it doesn't cause slowdowns, as some features have been appropriately reduced to ensure interoperability with the AntiVirus software already on your PC/Server. This, however, allows cross-checking through the scan;
- it identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M
- Download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
VirIT Mobile Security AntiMalware ITALIAN for ALL AndroidTM Devices
VirIT Mobile Security Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats, and empowers the user to safeguard his/her privacy with an advanced heuristic approach (Permission Analyzer).

TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can download the Lite version, which can be freely used in both private and corporate settings.
You can upgrade to the PRO version by purchasing it directly from our website=> click here to order
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities to our Research Center, that allowed us to make this information as complete as possible.
How to submit suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways:
- any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).

For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page:
How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
TG Soft Anti-Malware Research Centre (C.R.A.M.)


 This is an attempt at fraud by cybercriminals, whose aim is to extort money, in this case in the form of a fine. In fact, the message states the following:
This is an attempt at fraud by cybercriminals, whose aim is to extort money, in this case in the form of a fine. In fact, the message states the following: "Good morning. I am an experienced programmer who has hacked into your device's operating system. I have been watching you for several months now. My virus infected your device via an adult website you visited recently. If you don't know how it works, please read the information below. The Trojan virus gives me full access and control of the device you are using. As a result, I can see your entire screen, as well as turn on your camera and microphone without you ever knowing. In addition, I also have full access to your entire list of contacts on social networks and your catalogue. So why couldn't your antivirus detect the malicious malware? • The malware uses a special driver, updated every 4 hours, so your antivirus cannot detect it. I have created a video showing you masturbating on the left side of the screen, and on the right side, I have displayed the video you were watching at that moment. With a single click of the mouse, I can send your private video directly to your email contacts and social networks. In addition, I can also share your email and messenger login details."
"Good morning. I am an experienced programmer who has hacked into your device's operating system. I have been watching you for several months now. My virus infected your device via an adult website you visited recently. If you don't know how it works, please read the information below. The Trojan virus gives me full access and control of the device you are using. As a result, I can see your entire screen, as well as turn on your camera and microphone without you ever knowing. In addition, I also have full access to your entire list of contacts on social networks and your catalogue. So why couldn't your antivirus detect the malicious malware? • The malware uses a special driver, updated every 4 hours, so your antivirus cannot detect it. I have created a video showing you masturbating on the left side of the screen, and on the right side, I have displayed the video you were watching at that moment. With a single click of the mouse, I can send your private video directly to your email contacts and social networks. In addition, I can also share your email and messenger login details." The aim of cyber criminals is precisely to induce users to enter their sensitive data!
The aim of cyber criminals is precisely to induce users to enter their sensitive data! If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS. For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis