PHISHING INDEX
Below are the most common email phishing attempts detected by TG Soft's Anti-Malware Research Center in June 2024:
28/06/2024 =>
RelaxBanking
28/06/2024 =>
Aruba - Avviso importante (Important Notice)
26/06/2024 =>
BRT
24/06/2024 =>
DocsOnline Shared
22/06/2024 =>
Poste Italiane
19/06/2024 =>
Facebook - Diritto d'autore (Copyright)
19/06/2024 =>
Istituto Bancario (Bank)
13/06/2024 =>
SexTortion
12/06/2024 =>
Aruba - Fattura non pagata (Unpaid invoice)
03/06/2024 =>
Aruba - Rinnova il Dominio (Renew your Domain)
These emails are intended to trick some unfortunate person into providing sensitive data - such as bank account information, credit card codes or personal login credentials - with all the possible easily imaginable consequences.
28 June 2024 ==> Phishing Relax Banking
SUBJECT: <
Richiamata finale per confermare il tuo numero di telefono! >
(Final callback to confirm your phone number!)
Below we analyze the following phishing attempt that comes as a false communication from
RelaxBanking, the home banking app of the BCC banking institution.
The
message informs the receiver that, as a result of updates to the bank's system, all customers are asked to confirm their phone number, otherwise data loss and delays may occur.
It then invites the user to register as soon as possible, in 3 easy steps, through the following link:
Conferma la connessione (Confirm connection)
Analyzing the text of the message, we notice right away that the alert message comes from an e-mail address <kpolillo(at)bell(dot)net> that clearly does not come from the official RelaxBanking domain. Let's always be very careful before clicking on suspicious links.
Anyone who unluckily clicks on the link
Conferma la connessione (Confirm connection) will be redirected to an anomalous WEB page, which is unrelated to the official site of
RelaxBanking, but which has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals who want to get hold of your most valuable data, in order to use it for illegal purposes.
28 June 2024 ==> Phishing Aruba - Avviso importante (Important Notice)
SUBJECT: <
Avviso importante sul rinnovo del tuo dominio>
(Important notice about renewing your domain)
Phishing attempts pretending to be communications from the
Aruba brand continue this month.
The message informs the recipient that payment concerning the renewal of his domain hosted on
Aruba has not yet been made and that non-payment will result in the suspension of the account and thus the deactivation of all services associated with it, including mailboxes. He will then no longer be able to receive and send messages.
Thus, the cost of renewing the domain products/services for 12 months is reported.
It then invites the user to contact his bank or credit card company, to verify the reason for non-payment.Besides auto-renewal activation is proposed, via the following link:
ATTIVA RINNOVO AUTOMATICO (ENABLE AUTOMATIC RENEWAL)
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
Analyzing the text of the message, we notice right away that the sender's e-mail address <
support(at)auksight[.]com> is not from
Aruba's official domain.
Anyone who unluckily clicks on the
ATTIVA RINNOVO AUTOMATICO (ENABLE AUTOMATIC RENEWAL) link, will be redirected to the displayed page.
In this page the user is invited to access his client area by entering a login and password to renew the domain, avoiding the block of services.
Although haste and fear of the email suspension may prompt a quick conclusion, the invitation, as always, is to pay close attention to every detail.
In fact when we enter data into counterfeit websites, they will be delivered to the cyber criminals behind the scam, who will use them for malicious purposes.
https[:]//bikipark[.]com[.]/.well-known/3546bdf897cf8380eda3d5d4f8c1d7f8.....
We therefore urge you not to hurry because, in case of these attempts at computer fraud, you need to pay attention to every detail, even trivial ones.
26 June 2024 ==> Phishing BRT
SUBJECT:
< Notifica: il tuo pacco è stato sospeso a causa di un indirizzo di consegna errato. > (Notification: your package has been suspended due to an incorrect delivery address)
Below is a new phishing attempt, hiding behind a false communication from
BRT's service concerning the delivery of an alleged package.
The message notifies the unsuspecting recipient that his shipment is pending because the delivery address is incorrect. It then says that, in order to receive his package, the user must confirm the payment of delivery charges and the delivery address. These messages are increasingly being used to scam consumers who increasingly use e-commerce for their purchases.
The following link is provided to complete the shipment:
Enviar meu pacote (Send my package)
The alert email comes from an email address <support(at)approveithq(dot)com> that is unrelated to BRT's domain. This is definitely abnormal and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals who want to get hold of your most valuable data, in order to use it for illegal purposes.
24 June 2024 ==> Phishing DocsOnLine
SUBJECT: <
Completed Docs #-*****-9UJ7-MGYL7F-EQS7>
We analyze below the phishing attempt that aims to steal e-mail account credentials.
The message, in English, informs the recipient that he has received 1 file and can download it for viewing through the link:
View Document
When we analyze the message, we notice that it comes from an email address <suryadi_i(at)baramultigroup(dot)co(dot)id> that is not traceable to the DocsOnLine's domain.
This is definitely abnormal and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the
View Document, will be redirected to an anomalous WEB page, which has already been flagged as a DECEPTIVE PAGE /SITE.....
We always urge you to be careful and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
22 June 2024 ==> Phishing PosteItaliane
SUBJECT: <
Importante: verifica la fattura e i dettagli dell'indirizzo>
(Important: verify invoice and address details)
We find again this month the phishing attempt hidden behind a false communication supposedly from the
PosteItaliane service, concerning the delivery of an alleged package.
The message, which we quote on the side, refers to a shipment seemingly awaiting delivery due to unpaid shipping charges. It then informs the unsuspecting recipient that, in order to receive the package, he must pay shipping charges of €2.96 by clicking on the following button:
Link per il pagamento (Payment link)
The message seems to be from PosteItaliane. The tracking number 9903921 is reported, but we find no identifier associated with the recipient of the shipment. The email is rather general and is addressed to a Dear Customer. Moreover, the message comes from an e-mail address <miguel[dot]diaz[at]adventistas[dot]org> that is clearly not connected to the official domain of PosteItaliane. The purpose is surely to lead the user to click on the proposed link, which redirects to a web page that has, as always, the goal of inducing the user to enter his/her sensitive data.
Clicking the link in the message we are redirected to a web page that is supposed to simulate the official site of
PosteItaliane. Although the site may be misleading - in that the familiar
PosteItaliane logo has been included with the package number <IT245278896P> - we see that the url address on the broswer bar is anomalous and not traceable to
PosteItaliane:
<<https[:]//postaitsezioneregistro[.]freeXXXhostmost[.]com/avvisodiconsegna...>>
To conclude, we always urge you to be wary of any email that asks you to enter confidential data, and avoid clicking on suspicious links, which could lead to a counterfeit site difficult to distinguish from the original one. In fact in this way your most valuable data is put in the hands of cyber crooks and can be used at will.
19 June 2024 ==> Phishing Facebook Policy
SUBJECT: <
La tua pagina "******" rischia di essere disabilitata>
(Your "******" page is at risk of disablement)
This month we analyze a new phishing attempt that comes as a false communication from
Meta.
The message informs the recipient that the mentioned Facebook page "Has used images and content without the owner's permission. The copyright owner may inform us and complain that you have infringed on their copyrighted works.
Using copyrighted content without the owner's permission violates Facebook policies. If violations continue, your account may be suspended or permanently blocked."
Therefore, it calls on him to remove the infringing content or provide evidence that he/she has the right to use the content. It
then invites the user to report if the information is incorrect or if he has evidence that he/she owns the content or is authorized to use it, by submitting an objection using the form below:
Richiedi una revisione (Request review)
Clearly, the well-known U.S. company Meta, is unrelated to the mass sending of these emails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
When we analyze the text of the message, we notice right away that the sender's e-mail address <fb-meta-business-team-report-page-sp-sa(at)outlook(dot)it> is not from Meta's official domain and is very anomalous.
Anyone who unluckily clicks on the link
Richiedi una revisione (Request review), will be redirected to an anomalous WEB page, which is unrelated to the official site of
Meta.
From the image on the side we can see that the web page is graphically well designed and quite well simulates the official website of
Meta.
The landing page in this case is hosted on the url address:
https[:]//violation-policy-meta-ticket-id9968554[.]vercel[.]app
Which is unrelated to the official website of Meta.
This deceptive PAGE/ WEBSITE is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for criminal purposes.
19 June 2024 ==> Phishing Istituto Bancario (Bank)
SUBJECT: <
Importante: Attivare il nuovo sistema di sicurezza >
(Important: Activate the new security system)
This month we find again the phishing campaign, that spreads through an e-mail exploiting stolen graphics or similar to the graphics of a well-known national banking institution. Hence it tries to pass itself off as an official communication, in order to induce the unsuspecting recipient to do what requested and fall into a social engineering trap.
The message notifies the unsuspecting recipient that as of
06/22/2024 he/she will not be able to use his card unless he activates the new web security system. Without activation, the user will no longer be able to use his card. The procedure is simple and takes only 3 minutes, through the following link:
Clicca qui (Click here)
We can see right away that the alert message comes from an highly suspicious e-mail address <
****(at)verification[-]of[-]information(dot)net> and contains a very generic text, although the cybercriminal had the graphic foresight to include the well-known logo of the banking institution, which could mislead the user.
The purpose is to get the victim to log in and renew their banking app activation.
Anyone who unluckily clicks on the link
Clicca qui (Click here), will be redirected to an anomalous WEB page, unrelated to the official site of the bank.
From the side image we can see that the page is graphically well designed and quite well simulates the official website of the banking portal.
We also see other sub-menus such as Persone e Famiglie (People and Families), Giovani (Youth), Business, which identify the type of user... all with the aim of further reassuring the victim about the truthfulness of the portal. However many of the links do not lead to the expected pages.
With this in mind, we urge you to pay close attention to any misleading details, and remember that before entering sensitive data - in this case, home banking credentials i.e., Holder Code and PIN - it is crucial to examine the url address of the authentication form.
In our example, the landing page is hosted on the following url address:
https[:]//************[.]com/IT-OBBFIEY1LS/APP1[.]217[.]198[.]140[.]128...7...
which is unrelated to the official website of the well-known bank.
This DECEPTIVE PAGE/SITE is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use it for malicious purposes.
13 June 2024 ==> SexTortion
This month we find again the SexTortion-themed SCAM campaign. The e-mail suggests a breach of the victim's account by the scammer. The purpose of the message is to blackmail the recipient demanding the payment of a sum of money, in Bitcoin, in order not to divulge, among his email and social contacts, a private video of him viewing adult sites.
In fact, to make the extortion more plausible, an access password to his account is also given, probably a password previously hacked and available on the dark web.
The following is an extract from the text of the email on the side:
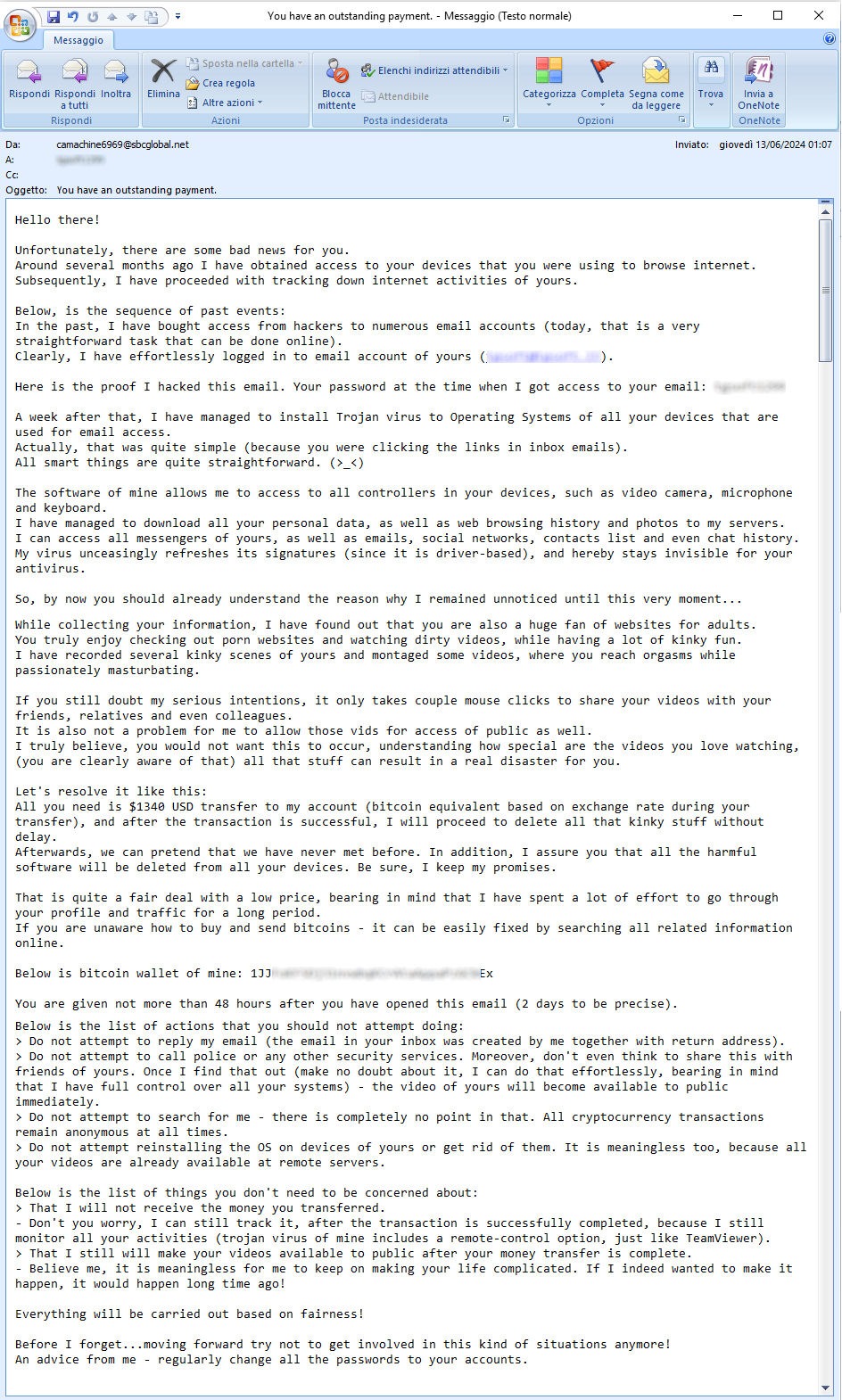
"Hello there! Unfortunately, there are some bad news for you. Around several months ago I have obtained access to your devices that you were using to browse internet. Subsequently, I have proceeded with tracking down internet activities of yours. Below, is the sequence of the past events: In the past, I have bought access from hackers to numerous email accounts (today that is a very straightforward task that can be done online). Clearly, I have effortlessly logged in to email account of yours(***). Here is the proof I hacked this email. Your password at the time when I got access to your email:***. A week after that, I have managed to install Trojan virus to Operating Systems of all yor devices that are used for email access. Actually, that was quite simple (because you were clicking the links in inbox emails). All smart sthings are quite straightforward. (>_<). The software of mine allows me to access to all controllers in your devices, such as video camera and keyboard. I have managed to download all your personal data, as well as web beowsing history and photos to my servers. I can access all messengers of yours, as well as emails, social networks, contacts list and even chat history. My virus unceasingly refreshe its signatures (since it is driver based), and hereby stays invisible for your antivirus. So, by now you should already understand the reason why I remained unnticed until this very moment … While collecting your information, Ihave found out that you are also a huge fan of sites for adults. You truly enjoy checking out”.
Next the victim is asked to send 1340 USD in Bitcoin to the wallet listed below: "1JJ
XXXXXXXXXXXXXXXXXXXXXXXEx'. After receiving the transaction, all data will be deleted, otherwise a video depicting the user, will be sent to all colleagues, friends and relatives. The victim has 2 days to make the payment!
Transactions recorded on the mentioned wallet as of
06/14/2024 are:
Wallet "
1JJXXXXXXXXXXXXXXXXXXXXXXXEx" amount requested 1340 USD => no transactions reported..
In such cases we always invite you:
- not to respond to these kinds of emails and not to open attachments or click unsafe links, and certainly NOT to send any money. You can safely ignore or delete them.
- if the criminal reports an actual user’s password – usually it is a password obtained from public Leaks (compromised data theft) of official sites occurred in the past (e.g., LinkedIn, Yahoo, etc.) - it is recommended to:
- Get experienced personnel to perform checks. Researchers and Analysts from the Anti Malware Research Center #CRAM of TG Soft are available to perform consultative verification activities on potentially compromised PCs / Servers;
- only after this verification by qualified personnel experienced in spy viruses and/or malware (also new generation malware), and once you have cleaned up the machine, you absolutely must change the passwords of the web services in use on the pc.
12 June 2024 ==> Phishing Aruba - Fattura non pagata (Unpaid invoice)
SUBJECT: <
Fattura non pagata #7RQ584#o>
(Unpaid invoice #7RQ584#o)
This month phishing attempts, that pretend to be communications from the
Aruba brand, continue.
The message notifies the recipient that his/her domain hosted on
Aruba, linked to his e-mail account, will expire on 06/12/2024. It then warns him to manually renew his services to avoid the deletion of the account and thus the deactivation of all services associated with it, including the mailboxes (therefore the chance to receive and send messages).
It then invites the user to log in to renew his/her services, through the following link:
RINNOVA IL DOMINIO (RENEW YOUR DOMAIN)
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal is always to steal sensitive data of the unsuspecting recipient.
When we analyze the message, we notice right away that the sender's e-mail address <
trovaprezzi(at)mediagomme[.]it> is not from the official domain of
Aruba.
An expiration date of 06/12/2024 is given to induce the victim to renew his mailbox in a timely manner. Since the email was delivered on the same day, there is not much time to renew and prevent services from being deactivated. The technique of stating a deadline to conclude the procedure is intended to push the user to act immediately and without much thought, driven by the fear of his/her e-mail account deactivation
Anyone who unluckily clicks on the
RINNOVA IL DOMINIO (RENEW YOUR DOMAIN) link, will be redirected to the displayed page.
Anyone who unluckily clicks on the
RINNOVA IL DOMINIO (RENEW YOUR DOMAIN) link, will be redirected to the displayed page.
As we can see, first of all, the landing page, unlike what expected, does not refer to the login form to log in to
Aruba's RESERVED AREA but hosts an online payment form that seems to rely on
BancaSella's circuit. Here you are directly requested to enter your credit card information to complete the payment of the modest amount of Euro 5.99.....
Although the user may be pushed to quickly complete the transaction by haste and fear of email box suspension, he can realize, looking at the browser bar, that the payment form is not on the official domain of
Aruba or even
BancaSella:
https[:]//pagamento[.]in[.]net/aopRBf-BA8Vt-jERKw-0zw14-.....
In these cases we therefore urge you not to rush and pay attention to every detail, even trivial ones.
By proceeding to enter the requested data, in this case your credit card details specifically, it will be delivered to the cyber criminals masterminding the scam who will use it for criminal purposes.
03 June 2024 ==> Phishing Aruba - Rinnova il dominio
SUBJECT: <
Aruba:Rinnovo abbonamento in sospeso #3128881892>
(Aruba:Pending subscription renewal #3128881892)
Phishing attempts, that pretend to be communications from the
Aruba brand, continue this month.
The message informs the recipient that, despite repeated requests, the renewal of his domain hosted on
Aruba, has been rejected because attempts to charge Euro 5.99 have always been rejected by the bank.
It then invites the user to make the renewal manually through the following link:
RINNOVA CON UN CLIC (RENEW WITH A CLICK)
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as usual, to steal sensitive data of the unsuspecting recipient.
When we analyze the text of the message, we notice right away that the sender's e-mail address <registration[at]trattorepocalaquila[dot]it> is not from
Aruba's official domain.
Anyone who unluckily clicks on the
RINNOVA CON UN CLIC (RENEW WITH A CLICK) link, will be redirected to the displayed page.
The landing page, however, unlike what expected, does not link to the login form for
Aruba's RESTRICTED AREA, but hosts an online payment form seemingly linked to the circuit of
BancaSella. Here you are prompted to enter your credit card information to complete the payment of the modest amount of Euro 5.99 .....
Although the user may be pushed to quickly complete the transaction by haste and the fear of ending up with a suspended email box, if we just look at the url address shown on the broswer bar we can realize that the payment form does not reside on the official domain of
Aruba or even
BancaSella:
https[:]//aruba[-]spa[.]id65200315104[.]org/2ckor...
In these cases we therefore urge you not to rush and pay attention to every detail, even trivial ones.
By proceeding to enter the requested data, in this case your credit card details specifically, it will be delivered to the cyber criminals masterminding the scam who will use it for criminal purposes.
A little bit of attention and glance, can save a lot of hassles and headaches...
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on phishing techniques for more details:
03/05/2024 11:56 - Phishing: the most common credential and/or data theft attempts in May 2024..
03/04/2024 10:23 - Phishing: the most common credential and/or data theft attempts in April 2024...
04/03/2024 10:42 - Phishing: the most common credential and/or data theft attempts in March 2024..
06/02/2024 08:55
- Phishing: the most common credential and/or data theft attempts in February 2024...
02/01/2024 16:04 - Phishing: the most common credential and/or data theft attempts in January 2024....
11/12/2023 09:39 - Phishing: the most common credential and/or data theft attempts in December 2023...
03/11/2023 08:58 - Phishing: the most common credential and/or data theft attempts in November 2023....
03/10/2023 16:35 - Phishing: the most common credential and/or data theft attempts in October 2023....
05/09/2023 10:35 - Phishing: the most common credential and/or data theft attempts in September 2023....
01/08/2023 17:33 - Phishing: the most common credential and/or data theft attempts in August 2023..
03/07/2023 10:23 - Phishing: the most common credential and/or data theft attempts in July 2023....
07/06/2023 15:57 - Phishing: the most common credential and/or data theft attempts in June 2023...
Try Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
Vir.IT eXplorer Lite has the following special features:
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- fully interoperable with other AntiVirus software and/or Internet Security products (both free and commercial) already installed on your computer. It doesn't need any uninstallation and it doesn't cause slowdowns, as some features have been appropriately reduced to ensure interoperability with the AntiVirus software already on your PC/Server. This, however, allows cross-checking through the scan;
- it identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M
- Download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
VirIT Mobile Security AntiMalware ITALIAN for ALL AndroidTM Devices
VirIT Mobile Security Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats, and empowers the user to safeguard their privacy with an advanced heuristic approach (Permission Analyzer).

TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can download the Lite version, which can be freely used in both private and corporate settings.
You can upgrade to the PRO version by purchasing it directly from our website=> click here to order
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities to our Research Center, that allowed us to make this information as complete as possible.
How to submit suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways:
- any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
 For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware..
TG Soft's C.R.A.M. (Anti-Malware Research Center)


 "Hello there! Unfortunately, there are some bad news for you. Around several months ago I have obtained access to your devices that you were using to browse internet. Subsequently, I have proceeded with tracking down internet activities of yours. Below, is the sequence of the past events: In the past, I have bought access from hackers to numerous email accounts (today that is a very straightforward task that can be done online). Clearly, I have effortlessly logged in to email account of yours(***). Here is the proof I hacked this email. Your password at the time when I got access to your email:***. A week after that, I have managed to install Trojan virus to Operating Systems of all yor devices that are used for email access. Actually, that was quite simple (because you were clicking the links in inbox emails). All smart sthings are quite straightforward. (>_<). The software of mine allows me to access to all controllers in your devices, such as video camera and keyboard. I have managed to download all your personal data, as well as web beowsing history and photos to my servers. I can access all messengers of yours, as well as emails, social networks, contacts list and even chat history. My virus unceasingly refreshe its signatures (since it is driver based), and hereby stays invisible for your antivirus. So, by now you should already understand the reason why I remained unnticed until this very moment … While collecting your information, Ihave found out that you are also a huge fan of sites for adults. You truly enjoy checking out”.
"Hello there! Unfortunately, there are some bad news for you. Around several months ago I have obtained access to your devices that you were using to browse internet. Subsequently, I have proceeded with tracking down internet activities of yours. Below, is the sequence of the past events: In the past, I have bought access from hackers to numerous email accounts (today that is a very straightforward task that can be done online). Clearly, I have effortlessly logged in to email account of yours(***). Here is the proof I hacked this email. Your password at the time when I got access to your email:***. A week after that, I have managed to install Trojan virus to Operating Systems of all yor devices that are used for email access. Actually, that was quite simple (because you were clicking the links in inbox emails). All smart sthings are quite straightforward. (>_<). The software of mine allows me to access to all controllers in your devices, such as video camera and keyboard. I have managed to download all your personal data, as well as web beowsing history and photos to my servers. I can access all messengers of yours, as well as emails, social networks, contacts list and even chat history. My virus unceasingly refreshe its signatures (since it is driver based), and hereby stays invisible for your antivirus. So, by now you should already understand the reason why I remained unnticed until this very moment … While collecting your information, Ihave found out that you are also a huge fan of sites for adults. You truly enjoy checking out”.  For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis